We are wanting to configure our Windows client to use only TLS 1.1 and greater. We've learned that we can do this by editing the registry. Now we want to make several HTTPS requests from different applications and check to be sure that they all use TLS 1.1 and above.
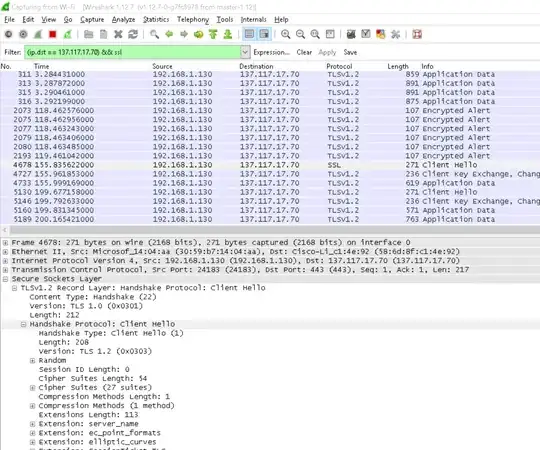
What we have tried is to run Wireshark with (ip.dst == 137.117.17.70) && ssl and with (ip.src == 137.117.17.70) && ssl as the filter and then run a web request from Internet Explorer. The results show this for the Client Hello.
Secure Sockets Layer
TLSv1.2 Record Layer: Handshake Protocol: Client Hello
Version: TLS 1.0
Handshake Protocol: Client Hello
Version: TLS 1.2
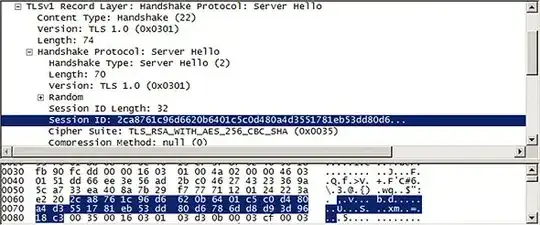
And they show this for the Server Hello.
Secure Sockets Layer
TLSv1.2 Record Layer: Handshake Protocol: Server Hello
Version: TLS 1.2
Handshake Protocol: Server Hello
Version: TLS 1.2
My sense is that that means we have not successfully turned off the legacy protocol, because the Client Hello initially says 1.0. Is that right?
Here is a better way of filtering for the Client Hello and Server Hello for a specific IP address.
(ip.src == 137.117.17.70) && ssl.handshake.type == 1
(ip.dst == 137.117.17.70) && ssl.handshake.type == 2