Root name server
A root name server is a name server for the root zone of the Domain Name System (DNS) of the Internet. It directly answers requests for records in the root zone and answers other requests by returning a list of the authoritative name servers for the appropriate top-level domain (TLD). The root name servers are a critical part of the Internet infrastructure because they are the first step in translating (resolving) human readable host names into IP addresses that are used in communication between Internet hosts.
A combination of limits in the DNS and certain protocols, namely the practical size of unfragmented User Datagram Protocol (UDP) packets, resulted in a decision to limit the number of root servers to thirteen server addresses.[1][2] The use of anycast addressing permits the actual number of root server instances to be much larger, and is 1,086 as of 2 July 2020.[3]
Root domain
The DNS is a hierarchical naming system for computers, services, or any resource participating in the Internet. The top of that hierarchy is the root domain. The root domain does not have a formal name and its label in the DNS hierarchy is an empty string. All fully qualified domain names (FQDNs) on the Internet can be regarded as ending with this empty string for the root domain, and therefore ending in a full stop character (the label delimiter), e.g., "www.example.com.". This is generally implied rather than explicit, as modern DNS software does not actually require that the terminating dot be included when attempting to translate a domain name to an IP address.
The root domain contains all top-level domains of the Internet. As of July 2015, it contains 1058 TLDs, including 730 generic top-level domains (gTLDs) and 301 country code top-level domains (ccTLDs) in the root domain.[4] In addition, the ARPA domain is used for technical name spaces in the management of Internet addressing and other resources. A TEST domain is used for testing internationalized domain names.
Resolver operation
When a computer on the Internet needs to resolve a domain name, it uses resolver software to perform the lookup. A resolver breaks the name up into its labels from right to left. The first component (TLD) is queried using a root server to obtain the responsible authoritative server. Queries for each label return more specific name servers until a name server returns the answer of the original query.
In practice, most of this information does not change very often over a period of hours and therefore it is cached by intermediate name servers or by a name cache built into the user's application. DNS lookups to the root name servers may therefore be relatively infrequent. A survey in 2003[5] reports that only 2% of all queries to the root servers were legitimate. Incorrect or non-existent caching was responsible for 75% of the queries, 12.5% were for unknown TLDs, 7% were for lookups using IP addresses as if they were domain names, etc. Some misconfigured desktop computers even tried to update the root server records for the TLDs. A similar list of observed problems and recommended fixes has been published in RFC 4697.
Although any local implementation of DNS can implement its own private root name servers, the term "root name server" is generally used to describe the thirteen well-known root name servers that implement the root name space domain for the Internet's official global implementation of the Domain Name System. Resolvers use a small 3 KB root.hints file published by Internic[6] to bootstrap this initial list of root server addresses.
Root server addresses
There are 13 logical root name servers specified, with logical names in the form letter.root-servers.net, where letter ranges from a to m. The choice of thirteen name servers was made because of limitations in the original DNS specification, which specifies a maximum packet size of 512 bytes when using the User Datagram Protocol (UDP).[7] Technically however, fourteen name servers fit into an IPv4 packet. The addition of IPv6 addresses for the root name servers requires more than 512 bytes, which is facilitated by the EDNS0 extension to the DNS standard.[8]
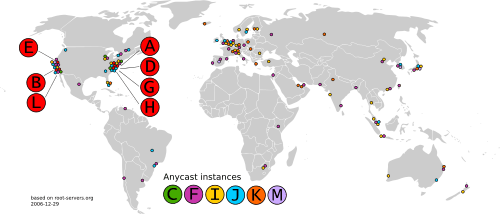
This does not mean that there are only 13 physical servers; each operator uses redundant computer equipment to provide reliable service even if failure of hardware or software occurs. Additionally, all operate in multiple geographical locations using a routing technique called anycast addressing, providing increased performance and even more fault tolerance. An informational homepage exists for every logical server (except G-Root) under the Root Server Technical Operations Association domain with web address in the form http://letter.root-servers.org/, where letter ranges from a to m.
Ten servers were originally in the United States; some are now operated using anycast addressing. Three servers were originally located in Stockholm (I-Root), Amsterdam (K-Root), and Tokyo (M-Root) respectively. Older servers had their own name before the policy of using similar names was established. With anycast, most of the physical root servers are now outside the United States, allowing for high performance worldwide.
| Letter | IPv4 address | IPv6 address | AS-number[9] | Old name | Operator | Location & Nr. of sites (global/local)[10] |
Software |
|---|---|---|---|---|---|---|---|
| A | 198.41.0.4 | 2001:503:ba3e::2:30 | AS19836,[9][note 1] AS36619, AS36620, AS36622, AS36625, AS36631, AS64820[note 2][11] | ns.internic.net | Verisign | Distributed using anycast 5/0 |
NSD and Verisign ATLAS |
| B | 199.9.14.201[note 3][12][13] | 2001:500:200::b[14] | AS394353[15] | ns1.isi.edu | USC-ISI | Distributed using anycast 6/0 |
BIND |
| C | 192.33.4.12 | 2001:500:2::c | AS2149[9][16] | c.psi.net | Cogent Communications | Distributed using anycast 8/0 |
BIND |
| D | 199.7.91.13[note 4][17] | 2001:500:2d::d | AS27[9][18] | terp.umd.edu | University of Maryland | Distributed using anycast 50/67 |
NSD[19] |
| E | 192.203.230.10 | 2001:500:a8::e | AS21556[9][20] | ns.nasa.gov | NASA Ames Research Center | Distributed using anycast 125/141 |
BIND and NSD |
| F | 192.5.5.241 | 2001:500:2f::f | AS3557[9][21] | ns.isc.org | Internet Systems Consortium | Distributed using anycast 57/0 |
BIND[22] |
| G[note 5] | 192.112.36.4[note 6] | 2001:500:12::d0d[note 6] | AS5927[9][23] | ns.nic.ddn.mil | Defense Information Systems Agency | Distributed using anycast 6/0 |
BIND |
| H | 198.97.190.53[note 7][24] | 2001:500:1::53[note 8][24] | AS1508[24][note 9][25] | aos.arl.army.mil | U.S. Army Research Lab | Distributed using anycast 8/0 |
NSD |
| I | 192.36.148.17 | 2001:7fe::53 | AS29216[9][26] | nic.nordu.net | Netnod | Distributed using anycast 58/0 |
BIND |
| J | 192.58.128.30[note 10] | 2001:503:c27::2:30 | AS26415,[9][27] AS36626, AS36628, AS36632[27] | N/A | Verisign | Distributed using anycast 61/13 |
NSD and Verisign ATLAS |
| K | 193.0.14.129 | 2001:7fd::1 | AS25152[9][28][29] | N/A | RIPE NCC | Distributed using anycast 5/23 |
BIND, NSD and Knot DNS[30] |
| L | 199.7.83.42[note 11][31] | 2001:500:9f::42[note 12][32] | AS20144[9][33][34] | N/A | ICANN | Distributed using anycast 161/0 |
NSD and Knot DNS[35] |
| M | 202.12.27.33 | 2001:dc3::35 | AS7500[9][36][37] | N/A | WIDE Project | Distributed using anycast 6/1 |
BIND |
There are also several alternative namespace systems with an alternative DNS root using their own set of root name servers that exist in parallel to the mainstream name servers. The first, AlterNIC, generated a substantial amount of press.
The function of a root name server may also be implemented locally, or on a provider network. Such servers are synchronized with the official root zone file as published by ICANN, and do not constitute an alternate root.
As the root name servers are an important part of the Internet, they have come under attack several times, although none of the attacks have ever been serious enough to severely affect the performance of the Internet.
Root server supervision
The DNS Root Server System Advisory Committee is an ICANN committee. ICANN's bylaws[38] assign authority over the operation of the root name servers of the Domain Name System to the DNS Root Server System Advisory Committee.
Root zone file
The root zone file is a small (about 2 MB) data set[6] whose publication is the primary purpose of root name servers. This is not to be confused with the root.hints file used to bootstrap a resolver.
The root zone file is at the apex of a hierarchical distributed database called the Domain Name System (DNS). This database is used by almost all Internet applications to translate worldwide unique names such as www.wikipedia.org into other identifiers such as IP addresses.
The contents of the root zone file is a list of names and numeric IP addresses of the authoritative DNS servers for all top-level domains (TLDs) such as com, org, edu, and the country code top-level domains. On 12 December 2004, 773 different authoritative servers for the TLDs were listed. Later the number of TLDs increased greatly. As of July 2020, the root zone consisted of 1511 TLDs (that does not include 55 domains that are not assigned, 8 that are retired and 11 test domains). Other name servers forward queries for which they do not have any information about authoritative servers to a root name server. The root name server, using its root zone file, answers with a referral to the authoritative servers for the appropriate TLD or with an indication that no such TLD exists.[39]
See also
Notes
- AS19836 is not listed by the RIPEstat tool, though one can see it in https://stat.ripe.net/AS19836#tabId=at-a-glance
- AS64820 is listed as "private use" in RIPE's RISwhois tool
- Originally it was 128.9.0.107; It was changed to 192.228.79.201 from January 2004 to October 2017.
- Since 3 January 2013; originally was 128.8.10.90.
- Formerly http://www.nic.mil/ (Internet Archive link); unlike all other DNS root servers, G-Root does not implement a homepage under root-servers.org, i.e. http://g.root-servers.org/.
- Unlike all other DNS root servers, G-Root does not respond to pings.
- Since 1 December 2015; originally was 128.63.2.53.
- Since 1 December 2015; originally was 2001:500:1::803f:235.
- Since 1 December 2015; originally was AS13.
- Since November 2002; originally was 198.41.0.10.
- Since 1 November 2007; originally was 198.32.64.12.
- Since 23 March 2016; originally was 2001:500:3::42.
References
- Mark Andrews, ISC (11 November 2011). "Reason for Limited number of Root DNS Servers". bind-users (Mailing list). Retrieved 8 January 2016.
- "DNS root server FAQ". Netnod. Retrieved 18 January 2016.
- "root-servers.org". Retrieved 2 July 2020.
- "Root Zone Database". IANA.
- Duane Wessels, Marina Fomenkov (2003). "Wow, That's a Lot of Packets" (PDF). Retrieved 7 November 2013.CS1 maint: uses authors parameter (link)
- "IANA – Root Files". www.iana.org. Retrieved 10 July 2019.
- RFC 1035 Domain names – implementation and specification
- ICANN: Accommodating IP Version 6 Address Resource Records for the Root of the Domain Name System
- AS-numbers and IP-addresses from Root-servers.org homepage checked 9 January 2014
- Location and sites from Root-servers.org homepage checked 10 October 2014
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. Retrieved 23 January 2014.
- "B-Root's IPv4 address to be renumbered 2017-10-24".
- "New IPv4 address for b.root-servers.net".
- "List of Root Servers".
- "Root Server Technical Operations Assn". root-servers.org. 7 August 2017. Retrieved 7 August 2017.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. 13 October 2013. Retrieved 23 January 2014.
- "D-Root is Changing its IPv4 Address on 3 January 2013". Archived from the original on 10 March 2013. Retrieved 16 December 2012.
- RISwhois, excluding less-specific AS3303 route announcement
- D-root History page
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. Retrieved 30 October 2017.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. Retrieved 23 January 2014.
- F-root | Internet Systems Consortium
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. 18 September 2013. Retrieved 23 January 2014.
- "Advance notice – H-root address change on December 1, 2015". DNSOP. 31 August 2015. Retrieved 19 February 2018.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. 2 January 2014. Retrieved 23 January 2014.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. Retrieved 23 January 2014.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. Retrieved 23 January 2014.
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. 20 June 2013. Retrieved 23 January 2014.
- "Peering Networks Detailed View". Peeringdb.com. 21 October 2013. Retrieved 23 January 2014.
- K-root Homepage
- "Advisory — "L Root" changing IP address on 1 November". ICANN.
- "L-Root IPv6 Renumbering". ICANN. Archived from the original on 22 April 2016.
- , excluding less-specific AS3303 route announcement
- "Peering Networks Detailed View". Peeringdb.com. 15 April 2013. Retrieved 23 January 2014.
- l.root-servers.net
- "RIS – RIPE Network Coordination Centre". Ris.ripe.net. 21 October 2013. Retrieved 23 January 2014.
- "Peering Networks Detailed View". Peeringdb.com. 23 December 2013. Retrieved 23 January 2014.
- "BYLAWS FOR INTERNET CORPORATION FOR ASSIGNED NAMES AND NUMBERS | A California Nonprofit Public-Benefit Corporation – ICANN". www.icann.org. Retrieved 10 July 2019.
- ISOC, DNS Root Name Servers explained for the non-expert, (Available online, accessed 19 March 2010.)
Further reading
- Root Server Technical Operations Association
- List of Root Servers, IANA
- Root Servers' Geographical Locations on Google Maps
- DNS Root Server System Advisory Committee
- DNS Root Name Servers Explained For Non-Experts
- DNS Root Name Servers Frequently Asked Questions
- Location of Root servers in Asia-Pacific
- Bogus Queries received at the Root Servers
- RFC 2826 – IAB Technical Comment on the Unique DNS Root
- RFC 2870 – Root Name Server Operational Requirements
- RFC 4697 – Observed DNS Resolution Misbehavior (from observations on the Root Servers)
- ORSN, Open Root Server Network – an unrelated, competing DNS-based name infrastructure
