Fast flux
Fast flux is a DNS technique used by botnets to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies. It can also refer to the combination of peer-to-peer networking, distributed command and control, web-based load balancing and proxy redirection used to make malware networks more resistant to discovery and counter-measures. The Storm Worm (2007) is one of the first malware variants to make use of this technique.
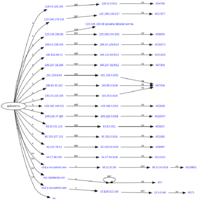
The basic idea behind Fast flux is to have numerous IP addresses associated with a single fully qualified domain name, where the IP addresses are swapped in and out with extremely high frequency, through changing DNS records.[1]
Internet users may see fast flux used in phishing attacks linked to criminal organizations, including attacks on social network services.
While security researchers have been aware of the technique since at least November 2006, the technique only received wider attention in the security trade press starting from July 2007.
Single-flux and double-flux
The simplest type of fast flux, named "single-flux", is characterized by multiple individual nodes within the network registering and de-registering their addresses as part of the DNS A (address) record list for a single DNS name. This combines round robin DNS with very short—usually less than five minutes (300s)[2] -- TTL (time to live) values to create a constantly changing list of destination addresses for that single DNS name. The list can be hundreds or thousands of entries long.
A more sophisticated type of fast flux, referred to itself as "double-flux",[3] is characterized by multiple nodes within the network registering and de-registering their addresses as part of the DNS Name Server record list for the DNS zone. This provides an additional layer of redundancy and survivability within the malware network.
Within a malware attack, the DNS records will normally point to a compromised system that will act as a proxy server. This method prevents some of the traditionally best defense mechanisms from working — e.g., IP-based access control lists (ACLs). The method can also mask the systems of attackers, which will exploit the network through a series of proxies and make it much more difficult to identify the attackers' network. The record will normally point to an IP where bots go for registration, to receive instructions, or to activate attacks. Because the IPs are proxified, it is possible to disguise the originating source of these instructions, increasing the survival rate as IP-based block lists are put in place.
The most effective measure against fast flux is to take down the domain name it uses. Registrars are, however, reluctant to do so because domain owners are legitimate customers for them and there's no worldwide-enforced policy of what constitutes an abuse. In addition to this, cybersquatters, including fast flux operators (who typically register new names on demand), are their main source of income. Security experts keep working on measures to ease this process.
Other measures can be taken by local network administrators. A network admin can force endpoints within their network to only be able to use local DNS servers by blocking all egress DNS traffic, and then blackhole requests for malicious domains at the DNS level. Alternatively, administrators with network devices capable of doing layer 7 inspection and intervention can set up policies that reset connections that attempt to resolve or make HTTP requests involving malicious domains.
See also
- Avalanche (phishing group) - implemented double fast flux on 800,000 domains
- Domain generation algorithm - A malware control technique where multiple domain names are generated by victim hosts.
References
- Danford; Salusky (2007). "The Honeynet Project: How Fast-Flux Service Networks Work". Retrieved 2010-08-23.
- "The Spamhaus Project - Frequently Asked Questions (FAQ)". www.spamhaus.org.
- Shateel A. Chowdhury, "MALICIOUS USES OF FAST-FLUX SERVICE NETWORKS (FFSN)", Hackers Terminal, Apr 29, 2019
Sources
- Spamhaus explanation of Fast Flux hosting
- Phishing by proxy SANS Internet Storm Center diary from 2006-11-28 describes use of compromised hosts within botnets making use of fast flux techniques to deliver malware.
- MySpace Phish and Drive-by attack vector propagating Fast Flux network growth SANS Internet Storm Center diary from 2007-06-26 with technical details on FluxBot and fast flux techniques (note: contains links to malicious code).
- Know Your Enemy: Fast-Flux Service Networks; An Ever Changing Enemy honeynet.org technical article from July 2007 and additional information on fast flux, including "single-flux" and "double-flux" techniques.
- Measuring and Detecting Fast-Flux Service Networks article by Holz et al. from February 2008 with empirical measurement results on fast flux.
- Fast flux foils bot-net takedown SecurityFocus article from 2007-07-09 describing impact of fast flux on botnet counter-measures.
- Attackers Hide in Fast Flux darkreading article from 2007-07-17 on the use of fast flux by criminal organizations behind malware.
- CRYPTO-GRAM October 15, 2007 issue Bruce Schneier mentions fast flux as a DNS technique utilized by the Storm Worm.
- ATLAS Summary Report - Real-time global report of fast flux activity.
- SAC 025 SSAC Advisory on Fast Flux Hosting and DNS
- GNSO Issues Report on Fast Flux Hosting
- FluXOR project from Computer and Network Security Lab (LaSeR) @ Università degli Studi di Milano (down as 07/27/2012)