Control system security
Industrial Control System (ICS) Cybersecurity is the prevention of (intentional or unintentional) interference with the proper operation of industrial automation and control systems. These control systems manage essential services including electricity, petroleum production, water, transportation, manufacturing, and communications. They rely on computers, networks, operating systems, applications, and programmable controllers, each of which could contain security vulnerabilities. The 2010 discovery of the Stuxnet worm demonstrated the vulnerability of these systems to cyber incidents.[1] The United States and other governments have passed cyber-security regulations requiring enhanced protection for control systems operating critical infrastructure.
Control system security is known by several other names such as SCADA security, PCN security, Industrial network security, Industrial control system (ICS) Cybersecurity, Operational Technology (OT) Security and Control System Cyber Security.
Risks
Insecurity of, or vulnerabilities inherent in industrial automation and control systems (IACS) can lead to severe consequences in categories such as safety, loss of life, personal injury, environmental impact, lost production, equipment damage, information theft, and company image. Guidance to assess, evaluate and mitigate these potential risks is provided through the application of many Governmental, regulatory, industry documents and Global Standards, addressed below.
Vulnerability of control systems
Industrial automation and control systems have become far more vulnerable to security incidents due to the following trends that have occurred over the last 10 to 15 years.
- Heavy use of Commercial Off-the Shelf Technology (COTS) and protocols. Integration of technology such as MS Windows, SQL, and Ethernet means that process control systems are now vulnerable to the same viruses, worms and trojans that affect IT systems
- Enterprise integration (using plant, corporate and even public networks) means that process control systems (legacy) are now being subjected to stresses they were not designed for
- Demand for Remote Access - 24/7 access for engineering, operations or technical support means more insecure or rogue connections to control system
- Security Through Obscurity - Using not publicly available protocols or standards is detrimental to system security
The cyber threats and attack strategies on automation systems are changing rapidly. Fortunately, regulation of control system security is rare as regulation is a slow moving process. The United States, for example, only does so for the nuclear power and the chemical industries.[2]
Government efforts
The U.S. Government Computer Emergency Readiness Team (US-CERT) originally instituted a control systems security program (CSSP) now the National Cybersecurity and Communications Integration Center (NCCIC) Industrial Control Systems, which has made available a large set of free National Institute of Standards and Technology (NIST) standards documents regarding control system security.[3]
Industrial Automation & Control System (IACS) Cybersecurity Standards
ISA/IEC-62443 (Formerly ISA-99)
ISA/IEC-62443 is a series of standards, technical reports, and related information that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS). This guidance applies to end-users (i.e. asset owner), system integrators, security practitioners, and control systems manufacturers responsible for manufacturing, designing, implementing, or managing industrial automation and control systems.
These documents were originally referred to as ANSI/ISA-99 or ISA99 standards, as they were created by the International Society for Automation (ISA) 99 committee, accredited by and publicly released as American National Standards Institute (ANSI) documents. In 2010, they were renumbered to be the ANSI/ISA-62443 series. This change was intended to align the ISA and ANSI document numbering with the corresponding International Electrotechnical Commission (IEC) standards.
All ISA work products are now numbered using the convention “ISA-62443-x-y” and previous ISA99 nomenclature is maintained for continuity purposes only.
ISA99 remains the name of the Industrial Automation and Control System Security Committee of the ISA. Since 2002, the committee has been developing a multi-part series of standards and technical reports on the subject of IACS security. These work products are then submitted to the ISA approval and then publishing under ANSI. They are also submitted to IEC for consideration as standards and specifications in the IEC 62443 series following the IEC standards development process.
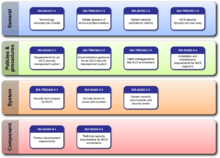
All ISA-62443 standards and technical reports are organized into four general categories called General, Policies and Procedures, System and Component.[4]
- The first (top) category includes common or foundational information such as concepts, models and terminology. Also included are work products that describe security metrics and security life cycles for IACS.
- The second category of work products targets the Asset Owner. These address various aspects of creating and maintaining an effective IACS security program.
- The third category includes work products that describe system design guidance and requirements for the secure integration of control systems. Core in this is the zone and conduit design model.
- The fourth category includes work products that describe the specific product development and technical requirements of control system products. This is primarily intended for control product vendors, but can be used by integrator and asset owners for to assist in the procurement of secure products.
IEC-62443
The IEC-62443 cybersecurity standards are the result of the IEC standards creation process where ANSI/ISA-62443 proposals are submitted to country committees where review is done and comments regarding changes are submitted. The comments are reviewed by various IEC 62443 committees where comments are discussed and changes are made as agreed upon. Many members of the IEC committees are the same persons from the ISA S99 committees. To date, the fundamental concepts from the original ANSI/ISA 62443 documents have been utilized. [5]
These standards are being used by practitioners in several industries to design and evaluate automation systems for cybersecurity resilience. Several of the standards are being used in personnel, engineering process, product, and system cybersecurity certification programs (also called conformity assessment programs).
Certifications are awarded by accredited Certification Bodies (CB) who operate following ISO/IEC 17065 and ISO/IEC 17025. Certification Bodies are accredited to perform the auditing, assessment, and testing work by an Accreditation Body (AB). There is often one national AB in each country. These ABs operate per the requirements of ISO/IEC 17011, a standard that contains requirements for the competence, consistency, and impartiality of accreditation bodies when accrediting conformity assessment bodies. ABs are typically members of the International Accreditation Forum (IAF) for work in management systems, products, services, and personnel accreditation or the International Laboratory Accreditation Cooperation (ILAC) for laboratory accreditation. A Multilateral Recognition Arrangement (MLA) between ABs will ensure global recognition of accredited CBs.
Control system security certification
The ISA Security Compliance Institute (ISCI) IEC 62443 Conformity Assessment Program
ISCI created the first conformity assessment scheme (commonly known as a certification scheme) for the ISA S99 IACS cybersecurity standards. This program certifies Commercial Off-the-shelf (COTS) IACS products and systems, addressing securing the IACS supply chain. exida from the United States was the first organization accredited for the ISCI scheme by the American National Standards Institute (ANSI) followed by the Control Systems Security Center – Certification Laboratory (CSSC-CL) accredited by the Japan Accreditation Board (JAB) and TÜV Rheinland accredited by Deutsche Akkreditierungsstelle (DAkkS). All of these AB organizations are members of the IAF.
ISASecure IEC 62443 Certification Offerings
Two COTS product certifications are available under the ISASecure® brand: ISASecure-CSA (Component Security Assurance) certifying automation products to the 62443-4-1 / 62443-4-2 IACS cybersecurity standards and ISASecure-SSA (System Security Assurance), certifying IACS systems to the IEC 62443-3-3 standard.
A third certification, SDLA (Secure Development Lifecycle Assurance) is available from ISCI which certifies IACS development organizations to the 62443-4-1 cybersecurity standard, providing assurances that a supplier organization has institutionalized cybersecurity into their product development practices.
ISO 17065 and Global Accreditation
The ISASecure 62443 conformity assessment scheme is an ISO 17065 program whose labs (certification bodies or CB) are independently accredited by ANSI/ANAB, JAB and other global ISO 17011 accreditation bodies (AB). The certification labs must also meet ISO 17025 lab accreditation requirements to ensure consistent application of certification requirements and recognized tools.
Through Mutual Recognition Arrangements (MRA) with IAF, ILAC and others, the accreditation of the ISASecure labs by the ISA 17011 accreditation bodies ensures that certificates issued by any of the ISASecure labs are globally recognized.
Test Tool Recognition
The ISASecure scheme includes a process for recognizing test tools to ensure the tools meet functional requirements necessary and sufficient to execute all required product tests and that test results will be consistent among the recognized tools.
Traditional Process industries including Chemicals, Oil and Gas
ISCI development processes include maintenance policies to ensure that the ISASecure certifications remain in alignment with the IEC 62443 standards as they evolve. While the IEC 62443 standards are designed to horizontally address technical cybersecurity requirements of a cross-section of industries, the ISASecure scheme’s certification requirements working groups include subject matter experts from the chemical and oil and gas industries and are reflective of their cybersecurity needs.
Building Management Systems
ISCI published a 2017 study which confirmed applicability of the IEC 62443 standards and ISASecure certification to Building Management Systems. The resulting study, executive summary, and PPT are available for free download from the www.isasecure.org website. ISCI has added leading BMS suppliers to its membership and established a BMS working group to support ongoing expansion of ISASecure certifications for BMS.
IEC 62443 Certification Programs
IEC 62443 certification schemes have also been established by several global Certification Bodies. Each has defined their own scheme based upon the referenced standards and procedures. Programs are being offered globally by several recognized CBs including exida, TÜV Rheinland, TÜV Sud, TÜV Nord, and SGS-TÜV Saar.
References
- Byres, Eric; Cusimano, John (February 2012). "The 7 Steps to ICS Security". Tofino Security and exida Consulting LLC. Archived from the original on January 23, 2013. Retrieved March 3, 2011.
- Gross, Michael Joseph (2011-04-01). "A Declaration of Cyber-War". Vanity Fair. Condé Nast. Archived from the original on 2014-07-13. Retrieved 2017-11-29.
- "Standards and References - NCCIC / ICS-CERT". ics-cert.us-cert.gov/. Archived from the original on 2010-10-26. Retrieved 2010-10-27.
- More information about the activities and plans of the ISA99 committee is available on the committee Wiki site ()
- "Standards and References - IEC-62443". www.iec.ch.
External links
- ISA 99 Standards
- ISA Security Compliance Institute
- NERC Standards (see CIP 002-009)
- NIST webpage NIST
- API 1164 Pipeline SCADA Security
- NERC Critical Infrastructure Protection (CIP) Standards
- ChemITC Guidance Documents
- CPNI Security for Industrial Control Systems Guidance
- International Accreditation Forum
- exida IEC62443 Certification Program
- TUV Certification Program