0
I configured incoming VPN connections on my Windows 7 machine and I want clients that connect to not be able to access computers and other network resources that are part of the same internal network. How can I do that?
My machine on which I configured incoming vpn connections is assigned the ip address 192.168.1.7. Another computer in the same local network has 192.168.1.2.
How can I make sure vpn clients do not have access to 192.168.1.2?
I already turned off network discovery so the resource such as 192.168.1.2 does not show but I can still ping and reach them. Is there a way to block access?
EDIT: I am aware I can do that via "IPSec Security Policy" but I like to do it on a user level, meaning, I want to block access to said IP address only for a specific user that logs in via vpn.
Thank you
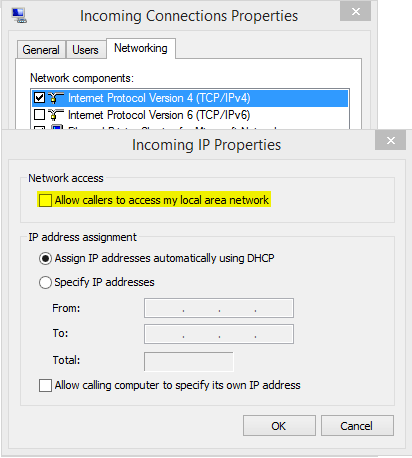
This would probably also disable disable internet access I assume? And it is not on a user level, meaning if an admin wants to gain access via vpn he/she would not be able to access the network...not really what I am looking for. I need restricted access for specific users. – Matthias Wolf – 2015-09-21T13:06:15.160
This will not disable Internet access, just block access to LAN machines. You can configure 2 Incoming connections, with one allowing local access (for admins) and another one - blocking access (for users). – Volodymyr M. – 2015-09-21T13:12:13.150
Good idea regarding 2 different incoming connections. Thanks for that. But the internet connection (my dns and gateway is at 192.168.1.1) is not working on the vpn client side. – Matthias Wolf – 2015-09-21T13:57:39.123
As long as you have firewall enabled and you block everything except wha t you need, users connected via Incoming connection will not be able to access these machines on the network. You can also deny ICMP (ping) traffic. – Volodymyr M. – 2015-09-21T14:37:02.053