2
There were many tools like mimikatz which extracts passwords from memory and display as plain text [working at windows 10 too :(] ,
is it there any reliable way to hide passwords from tools which fetch dumps from memory,
Preventing execution of such tools were one kind of solutions other than that any other configuration way ?
Before asking over here : the following work i did for studying how it extracts :
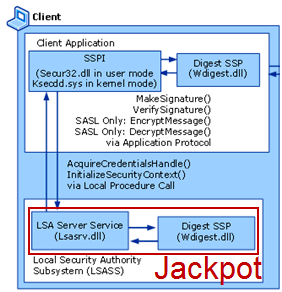
The key feature of this tool that sets it apart from other tools is its ability to pull plain-text passwords from the system instead of just password hashes. If your intention is to stay within the Windows environment and pass the hash this may not be that big of a deal. However, if you are exploring the curious case of password reuse across different environments—the plain-text password can be quite useful The architecture was as follows :
is it possible to detect mimikatz while executing ?or any other machine side tweak to prevent this kind of attacks?
OTP, One time passwords expire after each use and in seconds so it limits your exposure. That limits risk quite a bit. Yubikey and others offer solutions. – StackAbstraction – 2015-09-11T05:21:43.887
@StackAbstraction but otp cant be set for user accounts,is it there any way to set otp for windows accounts,even if we set the otp its extracting from memory ,so there were less chances of securing it right?kindly correct me if my statement was wrong – BlueBerry - Vignesh4303 – 2015-09-11T05:24:23.730
Yes you can Yubikey and google authenticator are supported Google Authenticator OTP for Windows Login Rohos paid Other options available if you search
– StackAbstraction – 2015-09-11T05:27:52.790