7
While using an open port checking tool (Technicians toolbox v1.1.0) I found a strange user name listening on port 139 hiding in PID 4 with a mix of Chinese and other Unicode characters as the user name:
There is no command line or creation date or an executable path or device path listed. Also the program won't let me trace the file path; it comes up with "Error". In Windows Task Manager, PID 4 shows as "System".
The Unicode characters are:
U+548B U+0824 U+428D U+8B0C U+E84A U+C833
U+ACE8 U+F8A9 U+B8FF U+F680 U+7318 U+29E9
U+FBBA U+22FF U+9305 U+0219 U+005C
The Google translator translated the Chinese portion as "Ye Ge mad dog" mixed with some form of Unicode.
According to unicode-table.com there is a mix of Arabic, Korean, Japanese, Latin and Chinese with private code blocks mixes throughout.
I am running my laptop through a Belkin 600 wifi range extender boosting off of a Linksys WRT54GS, both have no security.
Does anyone have any idea what this is? Should I kill this process?

Your post is just of block fo text, it's not easy to read. Please edit your post and format it; easy to read questions are easier to read – Dave – 2015-08-03T07:48:47.933
Port 139 is the port used by Windows file and print sharing. It is normal for it to be open to your internal network (if it isn't your machine can't offer file or print shares to others). It should not be visible to the public internet, i.e. your router should not pass it on, but most ISPs won't route it anyway. What "open port checking tool" did you use? – Jamie Hanrahan – 2015-08-03T08:21:52.893
Technicians toolbox v1.1.0 @JamieHanrahan – Joe Brown – 2015-08-03T08:51:14.903
Let's see more context, please. Less view of the leaves, more of the forest. – Jamie Hanrahan – 2015-08-03T11:01:39.747
1
More to investigate: does the port checking tool also give you the IP address of the client that is connected? If not, then what does something like
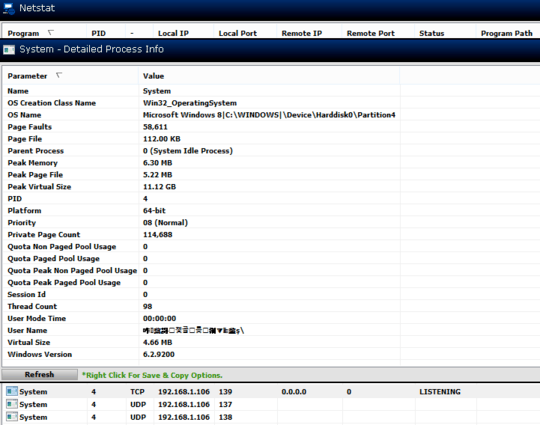
– Arjan – 2015-08-03T11:40:57.917netstat -aon | find "139"give you? Given that IP address, a whois might give you some clue about where they're connecting from, assuming it's not an address in the private ranges for local networks. Also, are you saying your WiFi is not protected? Then it could even be a neighbour (possibly with an infected computer) that is connecting.@Arjan There is no command line or creation date or an executable path or device path listed. Also the program wont let me trace the file path is comes up with "Error". There is no IP address listed. here is a screen shot of the process and its parameters. (http://i.imgur.com/MHiVya2.png) The process is the listening port with the Pid 4 right below the top window.
– Joe Brown – 2015-08-03T12:09:51.6801Ah, my bad: I thought you somehow saw the username of whoever connected, but it's the user name of the Windows process. Then
netstat -aon | find "139"can tell you if anyone is (currently) connected. The very low PID indicates that this is started at a very early stage when Windows is started, I think, but I'm not using Windows so I'm not 100% sure about that. Can you see the same weird user in the list of Windows users, somewhere in Control Panel? Also: the standard Windows Task Manager can show the PIDs too; maybe you can tell which program is related to that then? – Arjan – 2015-08-03T12:17:42.400@Arjan .No I have never come across this in any part of my Laptop and with no IP address and a low PID 4 which is listed as "system" under the task manager details and that I am unable to trace the processes file path is the reason I am here trying to find some answers. The Korean characters mixed with Japanese and Chinese, Latin and Aramaic, characters is that normal in Unicode strings? And as a process user name? Thanks for looking into this bud. – Joe Brown – 2015-08-03T12:30:23.523
"The Korean characters mixed with Japanese and Chinese, Latin and Aramaic, characters is that normal in Unicode strings?" that MIGHT just be an interpretation; if the user name is made out of random bytes, then trying to interpret these bytes as Unicode (more specifically: UTF-8 encoded Unicode) then you might see those funny characters. But if one would interpret them with some other encoding (like, bad but illustrative example: morse code, or music), one might see different things. But I guess it should not be random bytes to start with... – Arjan – 2015-08-03T12:35:50.423
By the way, "with no IP address": not seeing a remote IP address is okay, in this view, I think. The remote IP
0.0.0.0with remote port0indicates anyone COULD connect (if your modem/router allows for that), but I think there's simply no column in that overview to show you WHO is connected, if anyone. – Arjan – 2015-08-03T12:38:38.8171@Arjan No the Pid just list 4 as system along with a host of other process that run under system. And even with the tool I am using I am still unable to trace the file path. I'm at my the end of my know how on this. No other process has the user name written in Unicode on that tool I am using. I am trying to track the file path looking for a browser hijacking virus that slipped in with a game that was downloaded onto the family laptop. So far it's only been hijacking chromium based browsers Opera, Comodo and Google Chrome. Mozilla and IE finally got hit to now I'm using Slim Browser. – Joe Brown – 2015-08-03T12:48:53.743
1Just FYI: in Windows 7 running in Parallels on a Mac, I see user name
SYSTEMin Windows Task Manager. Andnetstat -aon | find "139"also happens to show PID 4 just like for you, andnetstat -abonshows many hits for that PID 4, but also shows no executable for any of those. Like for port 139:TCP 10.211.55.5:139 0.0.0.0:0 LISTENING 4 Can not obtain ownership information. – Arjan – 2015-08-03T12:55:41.1601
Ah, beware: in Task Manager you should see Image Name = System and User = SYSTEM, so make sure to use menu "View" to enable columns if needed. On Windows 7, I see this, including Image Path =
– Arjan – 2015-08-03T13:06:11.230C:\Windows\system32\ntoskrnl.exe, but no value for Command Line.