When using an unsecured network HTTPS offers no protection against a knowledgeable attacker, and especially for websites that use both HTTP and HTTPS.
Here is one example : When you type facebook.com in the address bar, you are actually starting an HTTP connection. The site then redirects you to an HTTPS page. However, an attacker, who is suitably placed between you and facebook.com, can modify this HTTPS redirection into an HTTP redirection
and steal your passwords,
or even inject malware into the website's response and infect your computer.
What you can do to avoid this situation is type in https://www.facebook.com instead of facebook.com. Another thing you can do is to keep the HTTPS page of facebook.com bookmarked and use that instead of typing.
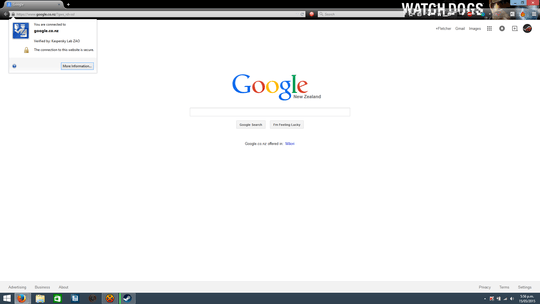
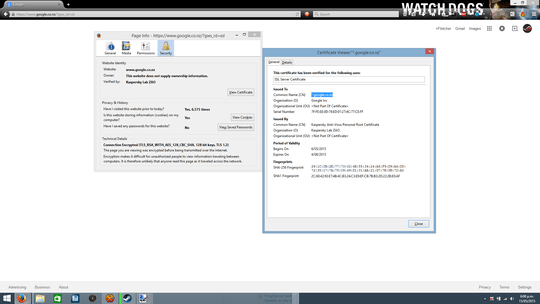
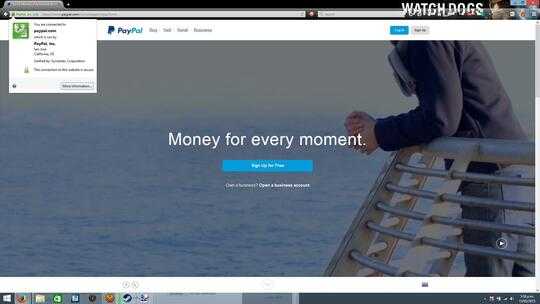
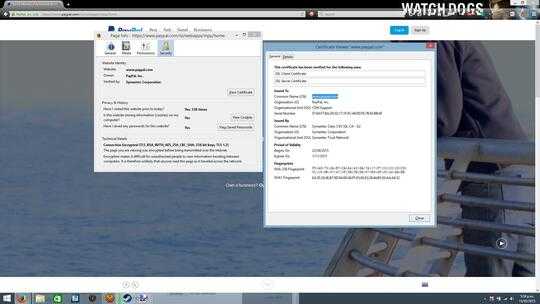
Using the browser to check the site's credentials is a very good test,
but many popular websites have lately seen their credentials stolen or
falsified.
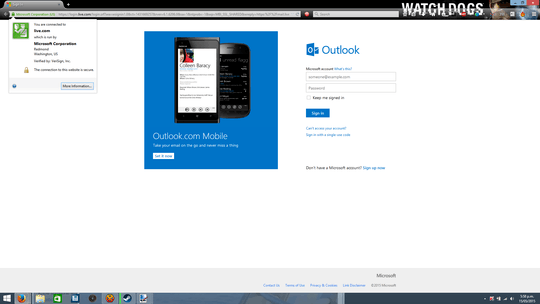
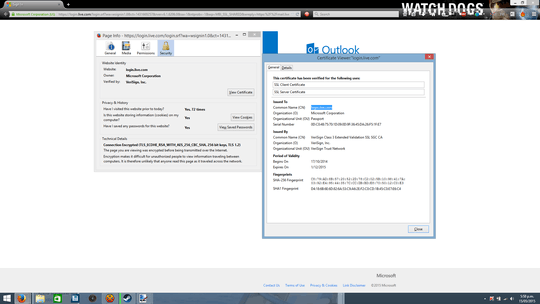
Hackers can also use credentials for website names that are very similar to the names of the websites one is trying to reach, that a casual inspection
will not detect.
Even pure HTTPS traffic can be attacked and cracked.
An entire pantheon of hacks was introduced over the past few years that bear names such as CRIME, BEAST, Lucky 13, SSLStrip and BREACH.
Using what's known as an oracle technique, attackers can use compression to gain crucial clues about the contents of an encrypted message. That's because many forms of encryption, including those found in HTTPS, do little or nothing to stop attackers from seeing the size of the encrypted payload. Compression oracle techniques are particularly effective at ferreting out small chunks of text in the encrypted data stream, such as passwords (!).
It is important to understand that the attacker only needs
to observe the HTTPS packets as they pass through the network,
which he can easily do on an unsecured network by installing a sniffer.
While none of the attacks have completely undermined the security afforded by HTTPS, they highlight the fragility of the two-decade-old SSL and TLS protocols,
and even of the software libraries that are used for HTTPS encryption.
Using VPN offers better protection, but as long as an attacker can observe
the traffic passing between your computer and the network,
you are not absolutely secure.
While each of the measures I have outlined above does improve security,
there is no guarantee of protection against an attacker who is resourceful
enough or could even use an as yet unknown attack method.
Security experts and browsers are always one step behind the hackers.
The best practice is not to enter sensitive information such as passwords
on an unsecured network. Even when the credentials are passed as cookies,
as is the case when a website offers the option of "remembering" the logon,
an attacker that intercepts the network message can easily extract these cookies.
One tool that can detect when HTTPS is intercepted and prevent you in time from
entering your credentials, is the Firefox Perspectives add-on.
It cannot however protect from having the HTTPS decrypted via a sniffer.
Perspectives is described as :
Perspectives is a new, decentralized approach to securely identifying
Internet servers. It automatically builds a database of server
identities using lightweight probing by "network notaries" - servers
located at multiple vantage points across the Internet. Each time you
connect to a secure website Perspectives compares the site's
certificate with network notary data, and warns if there is a
mismatch. This way you know if a certificate should be trusted! Using
Perspectives prevents "man-in-the-middle" attacks, lets you use
self-signed certificates, and helps you trust that your connections
really are secure.
SSL can be spoofed on a wireless system you do not manage, I suggest you use a VPN service and tunnel out to the internet. – Moab – 2015-05-17T19:01:23.427