I wanted a native 'app' that I can run at logon (and keep running/hidden) to enable Split Tunnel routing, similar to a function of Locamatic. Perhaps I'll fork Locamatic at some point and play with it. I may also upload this AppleScript to Github. I didn't want to mess with a daemon as this answer suggests.
This script assumes VPN has default VPN (Cisco IPSec) name and VPN route is 10.10.10.1/22 > 10.10.20.10. These will need to be changed/additional routes added. Run terminal > netstat -rn when VPN is connected (prior to enabling this script) to see VPN-added routes.
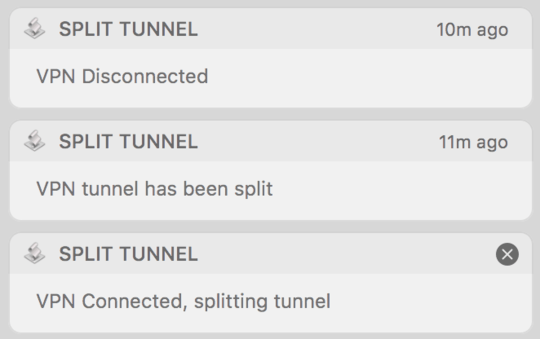
This script also generates growl-style notifications in Notification Center :)
I ran into some issues with Mark E. Haase's answer as my Cisco VPN modifies the existing gateway from a UCSc to a UGScI (en0 interface specific) route and adds the VPN gateway as a UCS route, necessitating the deletion of two default gateways and adding back the original UGSc default gateway
Thank goodness for StackExchange/google, this is my first AppleScript and I wouldn't have been able to put it together without a few hours of googling.
Suggestions/corrections/optimizations welcome!
AppleScript (GitHubGist):
global done
set done to 0
on idle
set status to do shell script "scutil --nc status "VPN (Cisco IPSec)" | sed -n 1p"
# do shell script "scutil --nc start "VPN (Cisco IPSec)"
if status is "Connected" then
if done is not 1 then
display notification "VPN Connected, splitting tunnel"
set gateway to do shell script "( netstat -rn | awk '/default/ {if ( index($6, \"en\") > 0 ){print $2} }' ) # gets non-VPN default gateway"
do shell script "sudo route delete default" # deletes VPN-assigned global (UCS) default gateway
do shell script "sudo route delete default -ifscope en0" # deletes en0 interface-specific (UGScI) LOCAL non-vpn gateway that prevents it being re-added as global default gateway
do shell script "sudo route add default " & gateway # re-adds LOCAL non-vpn gateway (from get command above) as global default gateway
do shell script "sudo route add 10.10.10.1/22 10.10.20.10" # adds VPN route
display notification "VPN tunnel has been split"
set done to 1
end if
else
if done is not 2 then
display notification "VPN Disconnected"
set done to 2
end if
end if
return 5
end idle
save as an app:
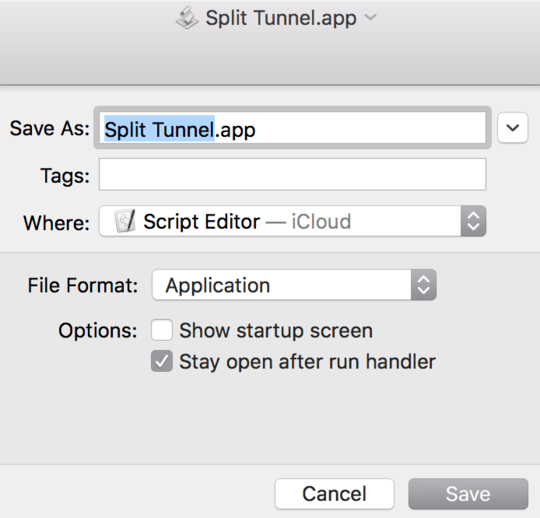
right click>show package contents, add the following to info.plist (this hides the app icon from dock, necessitating the use of Activity Monitor or terminal > pkill -f 'Split Tunnel' to quit the app, omit if you WANT a dock icon:
<key>LSBackgroundOnly</key>
<string>1</string>
create a new one-line routeNOPASSWD file (no extension) using the following code EXACTLY (this can prevent sudo access if done incorrectly, google visudo for more info - this allows the sudo commands in the AppleScript to run WITHOUT a password prompt, omit if you WANT a password prompt when the routing table needs to be changed):
%admin ALL = (ALL) NOPASSWD: /sbin/route
copy this file to /etc/sudoers.d
run the following commands in terminal (second command will prompt for password - this allows the sudo route commands in the AppleScript to run WITHOUT prompting for password, omit if a password prompt is desired when script is changing routing table)
chmod 440 /private/etc/sudoers.d/routeNOPASSWD
sudo chown root /private/etc/sudoers.d/routeNOPASSWD
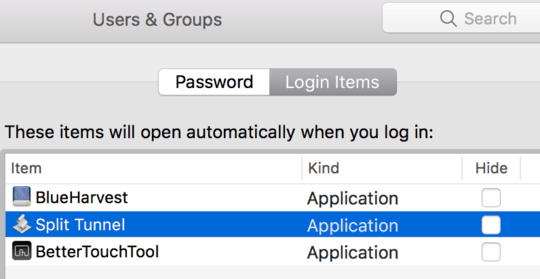
finally add the app to System Prefs > Users and Groups > login items



1Sadly this does not work on my Cisco AnyConnect client. – jeremyjjbrown – 2015-06-23T06:40:24.177
Curiosity: MacOS IPSec client creates a "link#24" and UCS gateway on connection, which persists through my 'change' command: route change default x.x.x.x gives me a default "Gateway" of "Link#8" (my en0) and flags of UCS, and is unusable. Route delete/add gives me a gateway of x.x.x.x and flags of UGSc - this works well. Any ideas? I'd like to use the 'change' command if possible, but I'd like to understand what the issue is. Can I change flags with route change? – goofology – 2018-04-12T00:34:46.407
1Can you explain more a bit for me? my ifconfig returns utun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1280 inet 192.168.5.102 --> 192.168.5.102 netmask 0xffffffff . Also I don't understand what should i replace with the number 10 above. Thank you. – Tuan Anh Tran – 2012-04-17T05:39:50.487
@TuanAnhTran: I updated my answer. Please let me know if that helps. – Mark E. Haase – 2012-04-18T03:47:53.600
For the latest version, I have /Applications/VPNClient.app installed and I don't see utun0 listed by ifconfig. I see gif0, stf0 and fw0 adapters. How do I determine which is the right adapter? I don't see any difference in ifconfig output with and without vpn connected (except for MTU value of en1). – haridsv – 2012-12-09T10:12:37.133
My instructions above were for the built-in client, not the official Cisco client. But gif0 is the adapter you want. See: http://superuser.com/questions/267660/mac-os-x-please-explain-ifconfig-output
– Mark E. Haase – 2012-12-11T17:00:45.6731
For those not familiar with LaunchDaemons, I wrote a guide in my answer here describing how to call a script to run every time you connect to VPN. (By the way, +1 excellent answer, but I needed a little more to get the gist working).
– dr jimbob – 2014-04-07T05:59:51.160