0
Google is in the process of removing CNNIC as a trusted root.
I wanted to make sure i don't have them in my certificate store anyway. So i check certmgr.msc, and look for them. They are neither in my:
- Trusted Root Certificate Authorities, nor
- Third-party Root Certification Authorites

Then i browse to their site
Then i browse to https://www.cnnic.cn/, to confirm that their certificate is invalid. And while there are the usual warnings about css and images being unsecure (and warnings about using weak encryption), the certificate itself is valid!:
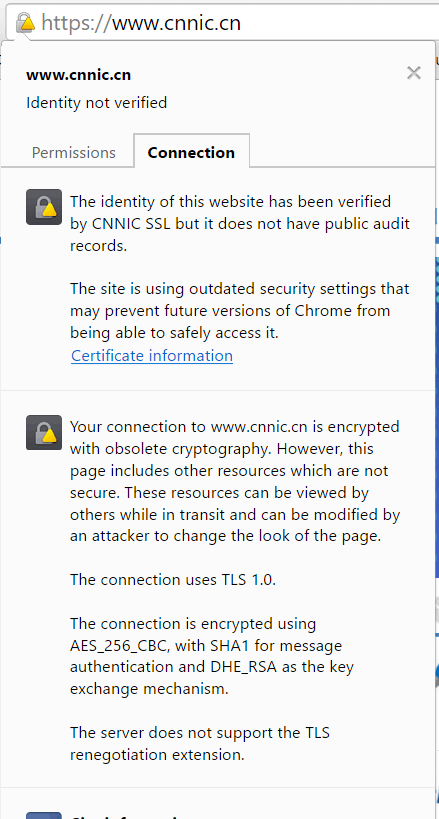
So I decide to view the certificate, so I can see its certification chain. Surely they must chain back to a trusted root that my computer does consider valid.
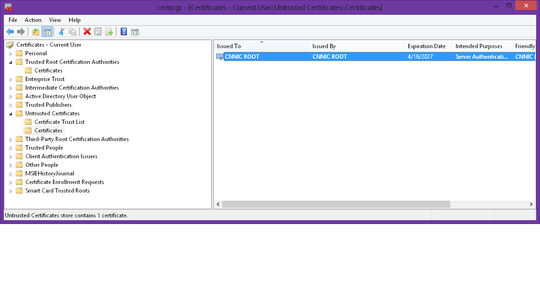
But the very act of viewing the certificate causes it to be added to my Trusted Root store:
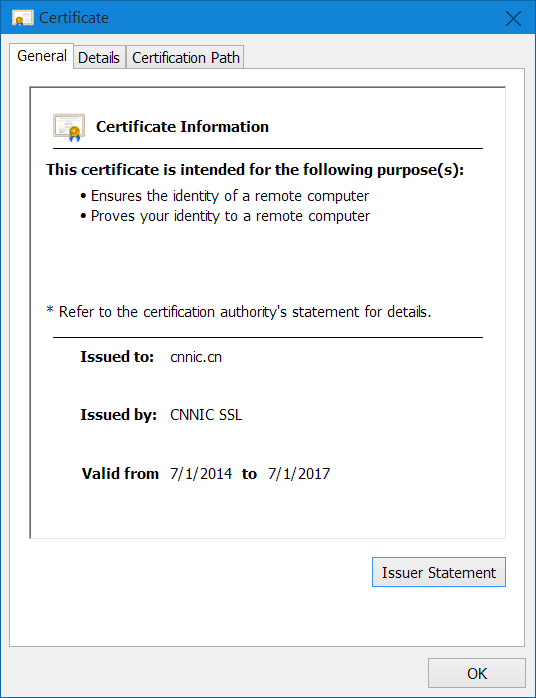
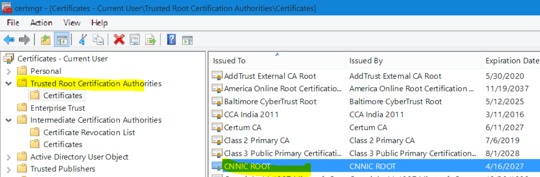
I'm fairly certain that they're not hacking Chrome on-the-fly like that. So how is this certificate ending up in my trusted roots list without my permission?
This also leads to the larger question:
- how do i prevent trusted root certificates from being added to my trusted root certificates list without my permission
- how do i locally revoke, or "untrust", a certificate
Bonus Chatter
China Internet Network Information Center
- Subject: CNNIC ROOT
- Issuer: CNNIC ROOT (it's a self-signed of course)
- Valid From: Monday, April 16, 2007 3:09:14 AM
- Valid To: Friday, April 16, 2027 3:09:14 AM
- Thumbprint (sha):
8b af 4c 9b 1d f0 2a 92 f7 da 12 8e b9 1b ac f4 98 60 4b 6f


I don't believe you understand what Chrome is going to do. Chrome does not "respect" certification revocation. Chrome has the capability to mark a certification has bad through its curl updates. Unless the operating system stops trusting the certification Chrome will trust it UNLESS Google by itself tells Chrome to stop trusting it. – Ramhound – 2015-04-03T00:45:45.093
there is actually malware that installs cnnic certs if missing. I', guessing thats not your issue, but, just for cursoities sake: http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=BrowserModifier:Win32/CNNIC http://www.exterminate-it.com/malpedia/remove-cnnic-update
– Frank Thomas – 2015-04-03T00:56:08.290Chrome has not stop trusting this certificate. Microsoft has not blacklisted this root certificate either. Which means on a domain you have some options if you want to stop trusting it entirely. its very likely Google will work CNNIC to avoid their certificate from being blacklisted by Chrome. – Ramhound – 2015-04-03T01:02:11.683
You’re using the user store, by the way. All default trusted root certificates are present in the computer store, instead. – Daniel B – 2015-04-03T01:04:11.397
@DanielB - Figured it out. – Ramhound – 2015-04-03T01:18:10.723
Related: Could merely visiting a web site push a root CA as trusted onto my PC? Spoiler: YES. And not just for Internet Explorer, but also for Chrome.
– Arjan – 2016-01-25T09:38:30.507