58
10
I've never had problems using Gmail with Thunderbird yet, but while trying to use a free software client for Google Talk/Chat/Hangout I've discovered that, according to Google's document on "less secure apps":
Some examples of apps that do not support the latest security standards include [...] Desktop mail clients like Microsoft Outlook and Mozilla Thunderbird.
Google then offers an all-or-nothing secure vs. non secure account switch ("Allow less secure apps").
Why does Google say Thunderbird "does not support the latest security standards"? Is Google trying to say that standard protocols like IMAP, SMTP and POP3 are "less secure" ways to access a mailbox? Are they trying to say that the use users make of that software puts their accounts at risk? Or what?
Secunia's Vulnerability Report: Mozilla Thunderbird 24.x (where is 31?) says «Unpatched 11% (1 of 9 Secunia advisories) [...] The most severe unpatched Secunia advisory affecting Mozilla Thunderbird 24.x, with all vendor patches applied, is rated Highly critical», apparently SA59803.
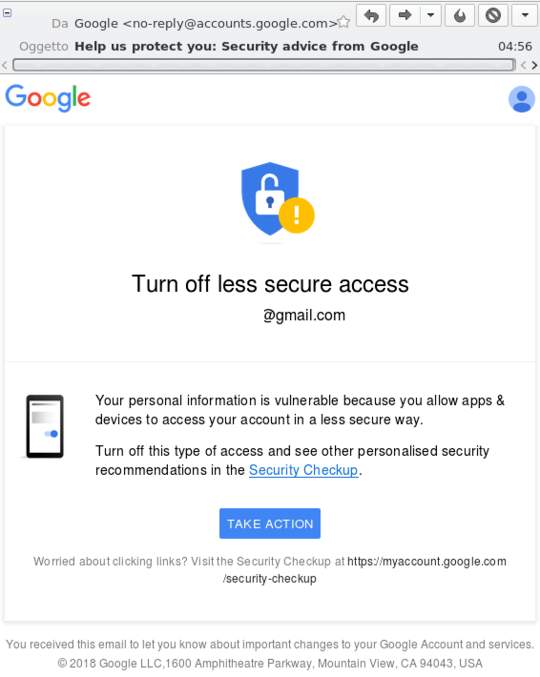
Update 2: as of 2018, Google double downs by sending messages to invite disabling "less secure" access:
Update: OAuth2 is available in Thunderbird 38, with further fixes in later releases, and bug 849540 has been closed. I'm still not clear about the goals of all this circus.
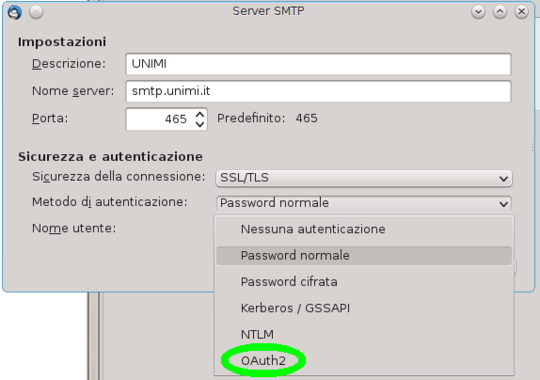
7Relevant Bugzilla issue. – Bob – 2014-12-23T02:56:01.367
2If you have two-factor authentication enabled on the account, you can generate an application-specific password for Thunderbird. – Ry- – 2014-12-23T03:22:46.743
8This really calls for the answer "Because Google is wrong." – Joshua – 2014-12-23T16:18:34.523
4
Related from Security.SE: What are the dangers of allowing “less secure apps” to access my Google account? (I think the practice of letting third parties see your credentials is fairly called "less secure", but it's totally unclear to me what security benefit Google gives by denying authentication after you've already given away your credentials.)
– apsillers – 2014-12-23T17:11:40.290