11
6
I have multiple dllhost.exe processes running on my Windows 7 computer:
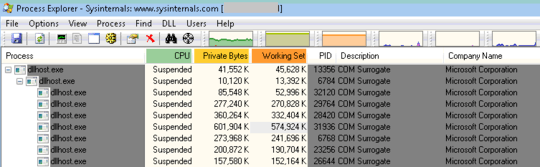
Every one of these image's command line is missing (what I am thinking is) the requisite /ProcessID:{000000000-0000-0000-0000-0000000000000} command line option:
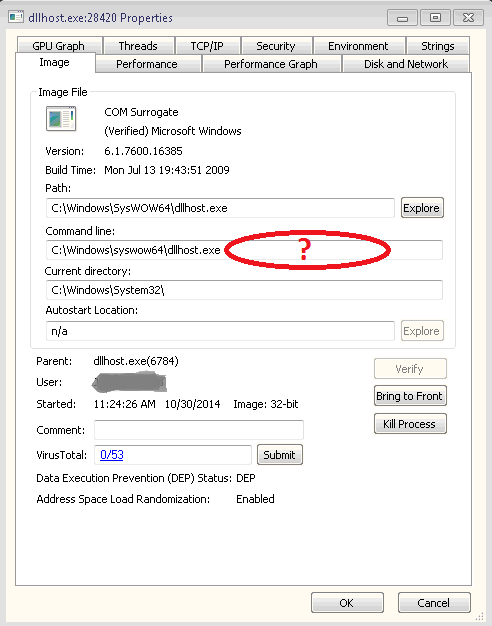
Question: How can I determine what's actually running in this process?
It's my belief that if I can identify the actual application doing the work inside these dllhost.exe processes I'll be able to determine if my system is infected or not (see below).
Why I'm Asking/What I've Tried:
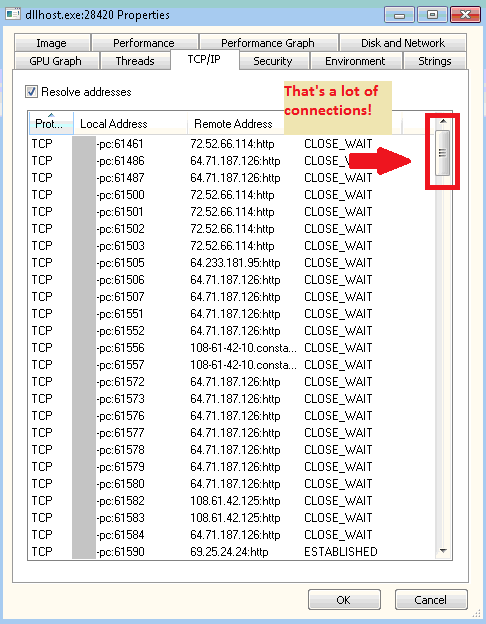
These DLLHOST.EXE instances look suspicious to me. For example, several of them have a lot of open TCP/IP connections:
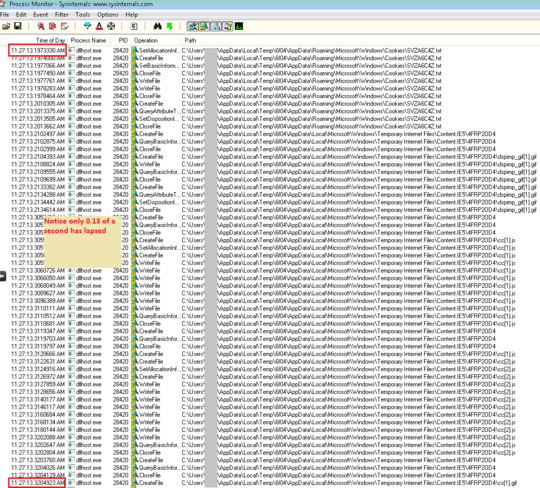
Process Monitor shows and absurd amount of activity. Just one of these processes generated 124,390 events in under 3 minutes. To make matters worse, several of these dllhost.exe processes are writing approximately 280 MB of data per minute to the user's TEMP and Temporary Internet Files folders in the form of folders and files with random four character names. Some of these are in use and cannot be deleted. Here's a filtered sample:
I know this is probably malicious. Unfortunately, blasting the system from orbit must only be done after exhausting all other options. To that point, I've done:
- Malwarebytes full scan
- Microsoft Security Essentials full scan
- Thoroughly reviewed Autoruns and submitted files I don't recognize to VirusTotal.com
- Thoroughly reviewed HijackThis
- TDSSKiller scan
- Reviewed this SuperUser question
- Followed these instructions: How To Determine Which Application Is Running Within a COM+ or Transaction Server Package
- For each of the
DLLHOST.EXEprocesses, I've reviewed the DLLs and Handles view in Process Explorer for any.exe,.dllor other application-type files for anything suspicious. Everything checked out though. - Ran ESET Online scanner
- Ran Microsoft Safety Scanner
- Booted to Safe Mode. The command switch-less
dllhost.exeinstance is still running.
And aside from a few minor adware detections, nothing malicious is popping up!
Update 1
<<Removed as irrelevant>>
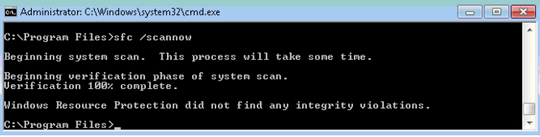
Update 2
Results of SFC /SCANNOW:
1
ask this Gov Maharaj from Microsoft via the posted emai, so that he can answer this in his show: http://channel9.msdn.com/Shows/The-Defrag-Show/
– magicandre1981 – 2014-10-31T08:09:21.297@harrymc Mine shows 7/13/2009 and 7168 bytes. File version 6.1.7600.16385. – I say Reinstate Monica – 2014-11-05T19:49:39.580
If your Windows is 64-bit then I would guess that the problem is coming from a 32-bit installed product. – harrymc – 2014-11-05T20:08:47.433
What's on the strings tab? Anything interesting? – Jon Kloske – 2014-11-10T05:01:50.800
Could be worthwhile to know what of services the
dllhost.exeprocess makes use of? Start from command linewmic path Win32_Service Where "ProcessId = 28420"– JosefZ – 2014-11-10T09:31:38.907