9
3
When I first open Firefox, I always get this notification from my firewall within about 30 seconds-ish. It does not matter if I'm yet browsing the web, I could just have a blank page up, or I could be using a local network website; I always get a message saying that Firefox is attempting to connect to safebrowsing.google.com.
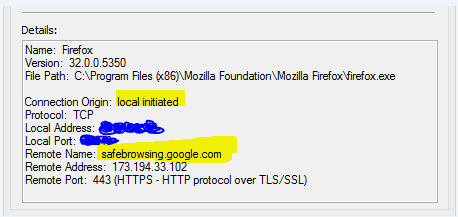
As you can see in the firewall prompt picture, this connection is started by my computer, more specifically Firefox.
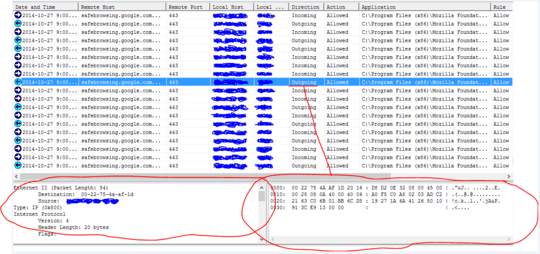
As you can see in the picture of my firewall's packet log, there are repeated inbound/outbound connections to that address with the browser just sitting open, and not doing anything.
System Details:
- Firefox 32.0.0.5350
- Windows 8
Firefox Details:
- Options/Advanced/Update/Firefox updates:
Never check for updates - Options/Advanced/Update/Automatically update:
Search Enginesis unchecked. - Options/Advanced/Data Choices/Telemetry:
Telemetryis unchecked. - Options/Advanced/Data Choices/Firefox Health Report:
Enable Firefox Health Reportis unchecked. - Options/Advanced/Data Choices/Crash Reporter:
Enable Crash Reporteris unchecked. - Options/General/Startup:
When Firefox Startsis set toShow my home page. - Options/General/Startup:
Home Pageis set toabout:newtab. - Manage Search Engine List:
Googleis set at the top of my list, andShow search suggestionsis enabled.
If I manually attempt to visit safebrowsing.google.com in Firefox it just redirects to Google.ca. According to Wikipedia:
The Google Chrome, Apple Safari and Mozilla Firefox web browsers use the lists from the Google Safe Browsing service for checking pages against potential threats.
However, I don't see what Firefox could possibly be looking up when I'm not even browsing the web.
As mentioned in this answer, shouldn't it only be looking things up if I perform a search, or type a URL in the address bar?
I would like to know why this connection is occuring, and what is being sent/recieved over it? This will help me decide whether to leave it alone, create a custom firewall rule blocking it, or ditch Firefox for a more respectful browser; I have low tolerance for non-user-initiated internet/network use by any application, even if it is intended to be helpful.
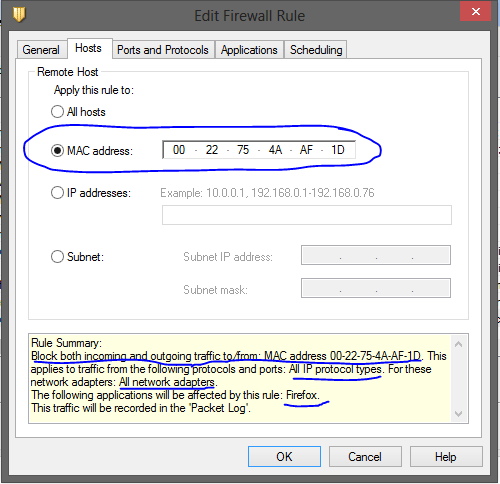
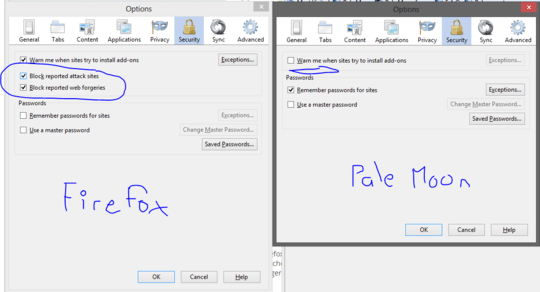
1
It might be just updating the list of safe sites. This might be worth reading: https://support.mozilla.org/fr/questions/922449
– rink.attendant.6 – 2014-10-28T05:44:53.503