155
106
How do I set up SSH so I don't have to type my password when connecting to a host?
155
106
How do I set up SSH so I don't have to type my password when connecting to a host?
167
If you happen to use GNOME, the seahorse application ("Passwords and Encryption Keys") can do it for you: File -> New -> Secure Shell Key.
If you prefer terminal, run ssh-keygen -t <type> to generate a keypair. Valid keypair types are:
The program will ask you for a passphrase and a location where to save the new key. Using the suggested default path is recommended because all other tools will look for it there.
Again, seahorse can often do that for you - in My Personal Keys, right-click on your SSH key and choose Configure key for secure shell.
Or, ssh-copy-id -i ~/.ssh/id_rsa.pub remote-user@remote-host in the terminal.
Or, completely manually step-by-step:
.ssh in the home directory of the remote user on the remote host.authorized_keys (if it doesn't exist already).umask is more liberal than usual, make the file not group-writable: chmod go-w ~/.ssh ~/.ssh/authorized_keys.~/.ssh/id_rsa.pub) into the remote ~/.ssh/authorized_keys file.If you load your private key into a ssh agent, it will hold the decrypted key in memory. We want this to avoid re-entering the password whenever we shell into a server.
First, the agent must be started or the path of a launched communication socket be loaded into a variable. Running ssh-agent on a terminal will generate commands for assigning and setting the agent variables. These commands can be saved in a file for use in a different terminal. Alternatively, one could run these commands and forget about re-using the same agent in another terminal. e.g: eval $(ssh-agent).
Loading the key is a simple matter of executing ssh-add and giving it the pass phrase.
If you are using GNOME, gnome-keyring-daemon usually provides the same SSH agent functionality as ssh-agent, so you should not need to start anything. GNOME will automatically load and unlock the key on login, too.
If everything was done correctly, using ssh user@server will not prompt you for a password. If something is wrong with the agent and not the key, you will be asked to type in the pass phrase for the key, and not the password for the user account.
Anything that uses ssh for communication will work without entering the user account password when the correct key is loaded in the agent. Programs such as scp, sftp and rsync make use of this.
id_dsa instead of id_rsa, and ECDSA will have id_ecdsa. authorized_keys2 - but it is really unlikely you'll find anything older than 5.0 in use.lsh, ssh.com, and other (Unix and not) SSH servers are not included in this tutorial.Copying the public key to a remote host:
ssh-copy-id -i ~/.ssh/id_rsa.pub myaccount@remotehost # this
cat ~/.ssh/id_rsa.pub | ssh myaccount@remotehost \
'mkdir -p ~/.ssh ; cat >> ~/.ssh/authorized_keys' # or this
ssh-agent > ~/.ssh/cross-terminal-agent . ~/.ssh/cross-terminal-agent
4there's a command ssh-copy-id that copies the public key to the target host and sets permissions automatically. – hasen – 2009-07-25T04:54:45.907
1Worth mentioning that once you've set up SSH keys you should consider disabling password authentication over SSH, by setting PasswordAuthentication no in /etc/sshd_config. – dimo414 – 2015-05-19T07:15:21.177
As a note: GNOME seahorse does not yet support keys using ed25519 in its ssh-agent socket (nor does it allow creating ed25519 keys). You need the official OpenSSH ssh-agent for that. Details and instructions here
1One liner: ssh-keygen -f ~/.ssh/id_rsa -N "";ssh-copy-id -i ~/.ssh/id_rsa username@server-ip-or-address (just replace username@server-ip-or-address). – totymedli – 2017-12-28T09:03:58.680
1but now I'm asked to insert the SSH password every time I login – João Pimentel Ferreira – 2018-01-06T19:03:42.147
Great tutorial! Works like charm – George Chalhoub – 2018-07-27T18:19:27.807
1Great answer! It is missing a bit about the file permissions of the key files - I just had a problem relating to that today. The private key file should only be accessible by me, and the public key file should only be writable by me. – ripper234 – 2010-10-28T08:42:33.963
Not working for me unfortunately. Also, I'd like to be able to use GIT PULL for example on a remote server and pull stuff from Github/Bitbucket private repos without reentering passwords. – trainoasis – 2019-08-07T09:09:39.157
run "ssh-add -l" : I did this and it says "The agent has no identities"... now what? – Jason S – 2009-07-18T18:44:06.003
7ah, you have to say "ssh-add {path-to-private-key-file}" and then it will ask you for your passphrase. Please make this more explicit in your post. You should also add "Fourth, run ssh". Part of the problem with the documentation with this stuff is that it glosses over seemingly obvious steps that are NOT obvious for someone new to the process who has no idea what's going on and how these programs work together. – Jason S – 2009-07-18T18:47:09.287
1Jason: ssh-add -l is to check if an agent is running. ssh-add without arguments will add the key from the default location (which is ~/.ssh/id_rsa). Anyway, updated. – user1686 – 2009-07-18T19:05:56.187
22
You didn't specify what Unix you're on, what Unix you're connecting to, what shell you're using, what SSH variant you're using, etc. So some of this might need to be adjusted slightly; this is based on reasonably recent versions of OpenSSH, which is used on a lot of unix variants.
This is all from your local desktop system.
ssh-keygen
Make sure to use the default for the keyname. I suggest that you do set a passphrase on that key, otherwise it's a security problem. "-t rsa" wouldn't be a bad idea, but probably isn't needed.
ssh-copy-id username@server
That will ask you for the password you'd use to log in, and sets up the authorized_keys stuff for you. (no need to do it by hand)
Then, this:
`ssh-agent`
or maybe this:
exec ssh-agent sh
or:
exec ssh-agent bash
That will start up an SSH agent that can hold your key. On many modern Unix variants, if you're logged in graphically, this will already have taken place. The first variant (with the backticks) puts an ssh-agent into the background and sets up the environment variables to talk to it. The second two have the agent run a shell for you, so that when you exit the shell, the agent exits.
Many modern Unix variants will already have an agent running for you, especially if you logged in graphically. You might try "ps aux | grep ssh-agent" or "ps -ef | grep ssh-agent"; if something is already running, use that.
Then, finally:
ssh-add
It will ask for a passphrase; give it the one you gave ssh-keygen. There's also ways to make it ask graphically. And you can put the ssh-agent and ssh-add stuff into your login scripts (setup is different depending on shell you use) to automate this, but some Unix variants (current Ubuntu Linux, for instance) do most of that automatically, so that all you really need to do is create a key and use ssh-copy-id to set it up on the remote host.
Now, "ssh username@server" should work without asking for any authentication. Behind the scenes, it's using a key that the ssh-agent is holding, and asking the agent to do the magic signing tricks for it.
11
It's possible to do this in PuTTY on Windows as well.
Once you have the public/private key pair all set up (as other answers here show) run PuttyGen. In there, load the existing private key that you've already set up, and then save it as a PuTTY private key (ppk).
Then in PuTTY, just click on the saved session you want to auto-login to and click Load. From here go into Connection -> Data in the left pane, and in "Auto-login username" type in the username for that remote server:
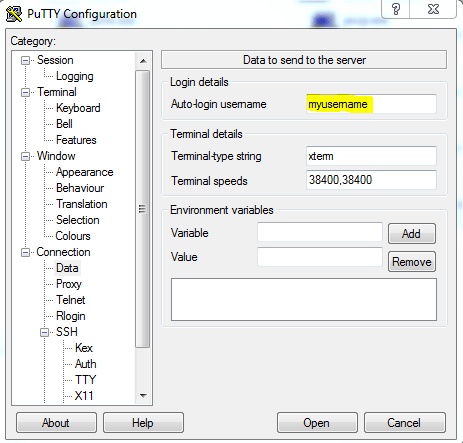
After that go into Connection -> SSH -> Auth, and browse for the ppk you made in PuttyGen:
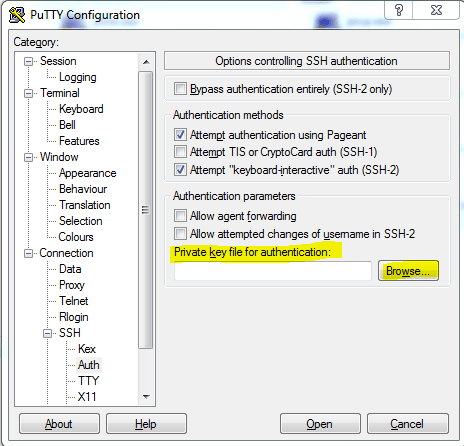
Then go back to the session page and save the session you loaded earlier.
The first image link, "PuTTY username entry", seems to be broken. – Peter Mortensen – 2009-08-20T22:24:55.530
2PuTTY includes its own version of ssh-agent; it's called Pageant. It runs in the system tray and holds your key for you. You do not need to ever run ssh-agent, just check "Allow agent forwarding" in PuTTY's options under the Auth section, and Pageant's connection will be forwarded to the remote end to make your key agent available to it. – Kevin Panko – 2009-08-20T22:48:07.200
3
From a very similar question on ServerFault, I'd recommend using ssh-copy-id, which does all the steps involved with setting up authentication keys for you:
ssh-copy-id is a script that uses ssh to log into a remote machine (presumably using a login password, so password authentication should be enabled, unless you've done some clever use of multiple identities)
It also changes the permissions of the remote user's home, ~/.ssh, and ~/.ssh/authorized_keys to remove group writability (which would otherwise prevent you from logging in, if the remote sshd has StrictModes set in its configuration).
If the -i option is given then the identity file (defaults to ~/.ssh/identity.pub) is used, regardless of whether there are any keys in your ssh-agent.
All you need to do is simply this:
ssh-copy-id user@host
Type in your password once, and you're good to go!
3
Apart from all already been told on how to set ssh keys, I recommend Keychain as a ssh-agent console frontend which allows you to handle one only per system process instead of per login.
I know there are already GNOME and KDE tools that do the same but if you are the console junkie type this is great (and can be used on most Unix systems).
To use it, simply append the following to your ~/.bashrc (similar for other shells):
if type keychain >/dev/null 2>/dev/null; then
keychain --nogui -q <all your SSH/PGP keys>
[ -f ~/.keychain/${HOSTNAME}-sh ] && . ~/.keychain/${HOSTNAME}-sh
[ -f ~/.keychain/${HOSTNAME}-sh-gpg ] && . ~/.keychain/${HOSTNAME}-sh-gpg
fi
2
Putty has a -pw option that let's you create a shortcut on desktop like this:
"C:\Program Files\PuTTY\putty.exe" -ssh user@192.168.2.2 -pw your_password
2
I wrote this very very short tutorial after getting REALLY REALLY frustrated with REALLY REALLY long tutorials cos really it's so simple :)
test -f ~/.ssh/id_rsa.pub || ssh-keygen -t rsa #press enter twice if given prompts, then "ssh-add"
scp ~/.ssh/id_rsa.pub destID@destMachine:/tmp/ #type password
ssh destID@destMachine #type password
cat /tmp/id_rsa.pub >> ~/.ssh/authorized_keys
rm /tmp/id_rsa.pub
2
http://linuxproblem.org/art_9.html
Your aim
You want to use Linux and OpenSSH to automize your tasks. Therefore you need an automatic login from host A / user a to Host B / user b. You don't want to enter any passwords, because you want to call ssh from a within a shell script.
1The downvote wasn't mine, but I wouldn't mind people deleting their answer if they noticed someone else posted an almost similar reply a few moments earlier. – Arjan – 2009-07-18T18:31:30.260
2Arjan: For the most part I agree with you, but when the posts are only separated by several seconds I don't necessarily think it is fair to punish the person in 2nd place. I'm not saying you have to reward them by upvoting, but downvoting gives the impression that the answer is wrong, instead of not in time – TheTXI – 2009-07-18T19:05:56.903
1
ssh-keygen. (If it tells you you have to specify a type, do ssh-keygen -t rsa.) When it asks you for a file location, take the default. When it asks you for a passphrase, hit enter for no passphrase.cat ~/.ssh/id_rsa.pub (or whatever the default file location in ssh-keygen was, though you'd have to have a really old ssh install for it to be different); copy the output to your clipboard.~/.ssh/authorized_keys (if ~/.ssh doesn't exist, slogin to someplace; this is the simple, easy way to get it created with the right permissions). Paste your clipboard (containing the id_rsa.pub from the other host) into this file.3-1 for suggesting to add no passphrase. Without a passphrase, anyone reading the file can now pose as the legitimate user. – bortzmeyer – 2009-07-18T17:30:30.877
2First, he asked to not have to type his password; I didn't really think that having to type a passphrase instead of his password would be an improvement. Second, you're wrong; that's why there's a public key and a private key, so the public key can be out in the world. – chaos – 2009-07-18T17:34:12.490
The password in question is typed during key generation, not every time you connect. Correct? – Richard Hoskins – 2009-07-18T19:42:18.563
No. Keys generated with a passphrase require the passphrase to be entered every time the key is used. – chaos – 2009-07-18T20:58:59.673
2Wrong. With ssh-agent (see the accepted answer), you type the password only once per session. – bortzmeyer – 2009-07-18T21:29:05.530
0
If you want to do it all in the terminal in Linux:
On the host
cd ~/.ssh/
ssh-keygen -t {rsa|dsa} -b {1024|2048|4096} -C "some comment text if you want" -f id_ArbitraryName
The items in the {} are options, use rsa or dsa and choose the bit size (bigger is more secure)
Then you need to add the permissions to the authorized_keys and authorized_keys2 files.
cat id_ArbitraryName.pub >> authorized_keys
cat id_AribtraryName.pub >> authorized_keys2
Then download the id_AribtraryName file to the box you want to ssh from. If the connecting box is unix based, a config file may be necessary (in putty, someone above covered that).
On the Connecting Box
In your config file - vim ~/.ssh/config
Host example.host.com # or your computer name
User username
IdentityFile ~/.ssh/id_ArbitraryName
The config file needs permissions of 600. The SSh folder needs 700.
Hope that helps if you run into the config issue that is omitted a lot.
On the latest Cygwin with the latest SSH, I was being re-prompted because I needed to make a change to my
~/.ssh/configthat is now requiredPubkeyAcceptedKeyTypes ssh-rsa*,ssh-dss*– HDave – 2015-11-03T16:02:07.720One might argue if using such keys does not require a password. To avoid that anyone who gets hold of your private key can actually abuse it, one can protect the key by a password of itself. Of course, one can leave that password blank, but there's many cases where that wouldn't be recommended. – Arjan – 2009-07-18T17:06:48.937