Very nice Erik Bitemo! I was thinking of adding a variable for the path then I realized you already have that although it was not defined. So the code I reused was:
$nets = netstat -ano |select-string LISTENING;
foreach ($n in $nets)
{
# make split easier PLUS make it a string instead of a match object
$p = $n -replace ' +',' ';
# make it an array
$nar = $p.Split(' ')
# pick last item...
$pname = $(Get-Process -id $nar[-1]).ProcessName
$ppath = $(Get-Process -id $nar[-1]).Path;
# print the modified line with processname instead of PID
$n -replace "$($nar[-1])","$($ppath) $($pname)" | where {$pname -like "*GMSVP*"}
}
I was trying to find the processes and services for an application where I used a somewhat different 2 liner.
Get-Service | select status,name,displayname,servicename | where {($_.DisplayName -like "myserv*") -or ($_.servicename -like "post*")} | ft -auto
Get-Process | select id, processname,cpu,path,description | where {$_.path -like "*myserv*"} | ft -auto
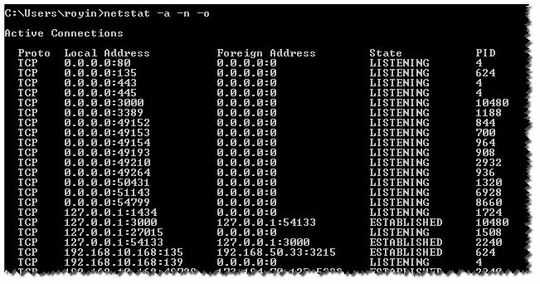
netstat -b as admin, e.g. netstat -abon. And the name of the exe is below – barlop – 2016-05-13T05:03:23.357