Software Encryption
TrueCrypt 7.1a is just fine for use on SSDs, but note that it will likely reduce IOPs performance by a considerable amount, though the drive will still perform more than 10 times better IOPs than HDD. So if you cannot make use of the options listed in Magician, TrueCrypt is an option for encrypting the drive, but it reportedly does not function very well with Windows 8 and later file systems. For this reason, BitLocker with full disk encryption is a better option for these operating systems.
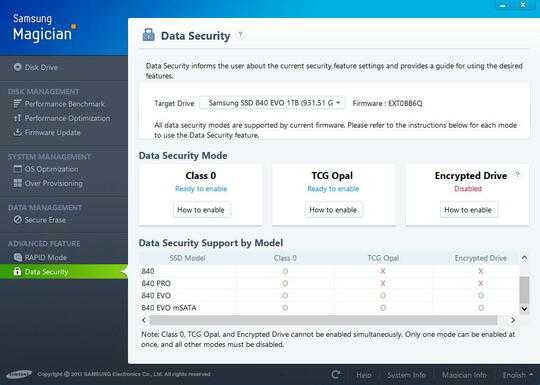
TCG Opal
TCG Opal is basically a standard which allows for a sort of mini operating system to be installed to a reserved part of the drive that is only for the purpose of allowing the drive to boot and present the user with a password for granting access to the drive. There are various tools available for installing this feature, including some reportedly stable open source projects, but Windows 8 and later BitLocker should support this feature.
I do not have Windows 8 or later, so I cannot provide instruction on how to set this up, but my reading indicates that this is only available when installing Windows, and not after it is installed. Experienced users feel free to correct me.
ATA Password
The ATA password locking is an optional feature of the ATA standard supported by the Samsung 840 and later series drives, as well as thousands of others. This standard is not related to a BIOS and can be accessed through any number of methods. I do not recommend using a BIOS for setting or managing the ATA password as the BIOS may not be properly conforming to the ATA standard. I have experience with my own hardware appearing to support the feature, but actually not being in compliance.
Note that searching on this feature will produce a lot of discussion claiming that the ATA lock feature should not be considered safe for protecting data. This is generally only correct for HDDs that are not also Self Encrypting Drives (SED). Since the Samsung 840 and later series drives are SSDs and SEDs, these discussions are simply not applicable. The ATA password locked Samsung 840 series and later should be secure enough for your usage, as described in this question.
The best way to be sure your BIOS can support unlocking an ATA password locked drive is to lock a drive, install it into the computer, then boot the computer and see if it asks for a password and if the password entered can unlock the drive.
This test should not be performed on a drive with data you do not want to lose.
Fortunately, the test drive does not have to be the Samsung drive, as it can be any drive that supports the ATA standard security set and can be installed in the target computer.
The best way I have found for accessing the ATA features of a drive are with the Linux command line utility hdparm. Even if you don't have a computer with Linux, there are many distributions whose install disk image also supports running the OS 'live' from the install media. Ubuntu 16.04 LTS, for example, should easily and quickly install to the vast majority of computers and the same image can also be written to flash media for running on systems without optical drives.
Detailed instructions on how to enable ATA password security are beyond the scope of this question, but I found this tutorial to be one of the best for this task.
Enabling ATA Security on a Self-Encrypting SSD
Note that the maximum password length is 32 characters. I recommend doing the test with a 32-character password to be sure that the BIOS supports the standard correctly.
With the target computer powered down and the drive ATA password locked, install the drive and boot the system. If the BIOS does not ask for a password to unlock the drive, then the BIOS does not support ATA password unlock. Also, if it seems like you are entering the password completely correctly, but it is not unlocking the drive, it may be that the BIOS does not properly support the ATA standard, and thus should not be trusted.
It may be a good idea to have some way to verify that the system is properly reading the unlocked drive, such as by having an operating system installed and loading properly, or installing along side an OS drive that loads and can mount the test drive and read and write files without issue.
If the test is successful and you feel confident in repeating the steps, enabling the ATA password on a drive, including one with an OS installed, will not change anything in the data portion of the drive, so it should boot up normally after entering the password in the BIOS.
Encrypting SSDs is problematic due to wear leveling. I don't know all the specifics to it, but you might find a related question at Security.SE helpful. (Note that this is from a security perspective rather than implementation.)
– Jonathan Garber – 11 years agoPlease read the comments on my post on SSD encryption: http://vxlabs.com/2012/12/22/ssds-with-usable-built-in-hardware-based-full-disk-encryption/ -- it has become a discussion board for people interested in SSD FDEs. I think TCG Opal that you show might be interesting.
– Charl Botha – 11 years agoThat's a good discussion Charl, I will keep an eye on it. Looks like none of your visitors have cracked this yet. WinMagic SecureDoc Standalone for Windows is mentioned which is new to me... but I'm not sure I want to pay $100 just for the privilege of setting a password! – Stephen Kennedy – 11 years ago