10
4
My VPN connection forces all internet traffic through the tunnel, and that's very slow. I want to be able to tunnel only certain IP addresses, and to do that at my side (client-side).
I'm connecting to a VPN with FortiSSL Client, the route table looks like this before a connection is established:
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.0.1 192.168.0.101 40
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.0.0 255.255.255.0 On-link 192.168.0.101 276
192.168.0.101 255.255.255.255 On-link 192.168.0.101 276
192.168.0.255 255.255.255.255 On-link 192.168.0.101 276
192.168.119.0 255.255.255.0 On-link 192.168.119.1 276
192.168.119.1 255.255.255.255 On-link 192.168.119.1 276
192.168.119.255 255.255.255.255 On-link 192.168.119.1 276
192.168.221.0 255.255.255.0 On-link 192.168.221.1 276
192.168.221.1 255.255.255.255 On-link 192.168.221.1 276
192.168.221.255 255.255.255.255 On-link 192.168.221.1 276
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.119.1 276
224.0.0.0 240.0.0.0 On-link 192.168.221.1 276
224.0.0.0 240.0.0.0 On-link 192.168.0.101 276
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.119.1 276
255.255.255.255 255.255.255.255 On-link 192.168.221.1 276
255.255.255.255 255.255.255.255 On-link 192.168.0.101 276
After connecting it looks like this:
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.0.1 192.168.0.101 4265
0.0.0.0 0.0.0.0 On-link 172.16.0.1 21
127.0.0.0 255.0.0.0 On-link 127.0.0.1 4531
127.0.0.1 255.255.255.255 On-link 127.0.0.1 4531
127.255.255.255 255.255.255.255 On-link 127.0.0.1 4531
172.16.0.1 255.255.255.255 On-link 172.16.0.1 276
192.168.0.0 255.255.255.0 On-link 192.168.0.101 4501
192.168.0.101 255.255.255.255 On-link 192.168.0.101 4501
192.168.0.255 255.255.255.255 On-link 192.168.0.101 4501
192.168.119.0 255.255.255.0 On-link 192.168.119.1 4501
192.168.119.1 255.255.255.255 On-link 192.168.119.1 4501
192.168.119.255 255.255.255.255 On-link 192.168.119.1 4501
192.168.221.0 255.255.255.0 On-link 192.168.221.1 4501
192.168.221.1 255.255.255.255 On-link 192.168.221.1 4501
192.168.221.255 255.255.255.255 On-link 192.168.221.1 4501
200.250.246.74 255.255.255.255 192.168.0.1 192.168.0.101 4245
224.0.0.0 240.0.0.0 On-link 127.0.0.1 4531
224.0.0.0 240.0.0.0 On-link 192.168.119.1 4502
224.0.0.0 240.0.0.0 On-link 192.168.221.1 4502
224.0.0.0 240.0.0.0 On-link 192.168.0.101 4502
224.0.0.0 240.0.0.0 On-link 172.16.0.1 21
255.255.255.255 255.255.255.255 On-link 127.0.0.1 4531
255.255.255.255 255.255.255.255 On-link 192.168.119.1 4501
255.255.255.255 255.255.255.255 On-link 192.168.221.1 4501
255.255.255.255 255.255.255.255 On-link 192.168.0.101 4501
255.255.255.255 255.255.255.255 On-link 172.16.0.1 276
The VPN client puts a catch-all route with a lower metric than all of my other routes and this routes all internet traffic through the tunnel. I tried changing my default internet route's metric to a lower value:
C:\Windows\system32>route change 0.0.0.0 mask 0.0.0.0 192.168.0.1 metric 10 if 13
OK!
But nothing changed.
Then I tried deleting the VPN's "catch-all" route, the one with metric 21 above:
C:\Windows\system32>route delete 0.0.0.0 mask 0.0.0.0 if 50
OK!
And it broke everything:
C:\Windows\system32>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
PING: transmit failed. General failure.
I tried changing the metric on the adapters as well, but the FortiSSL Client overrides all settings when it connects, so it didn't help.
The fix must come from my side, as the folk on the other side take days to respond.
I'm running Windows 7 x64 if that helps.
-- UPDATE (2013-12-24) --
Thanks to mbrownnyc's tip, I examined the issue with Rohitab and found out FortiSSL Client watches the routes table with the NotifyRouteChange IP Helper API call.
I set a breakpoint before NotifyRouteChange calls and used the option "Skip Call" to sucessfully prevent FortiSSL from resetting route metrics, and I now have:
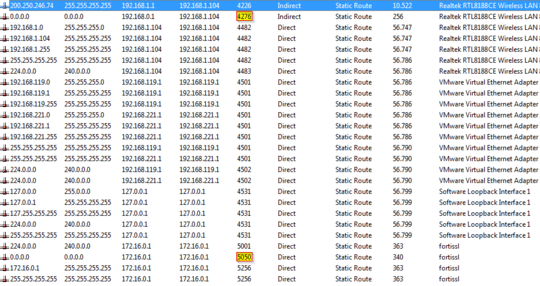
Yet when I run tracert my route still goes out through the VPN:
C:\Windows\system32>tracert www.google.com
Tracing route to www.google.com [173.194.118.83]
over a maximum of 30 hops:
1 45 ms 47 ms 45 ms Jurema [172.16.0.1]
Is there any aspect of windows networking I'm not aware of that can favor a certain route even if route print's metrics say otherwise?
Juliano, were you able to use the Rohitab tool to get this working? I have the same issue, and am trying to use the API Monitor, but cannot get to the screen you show. And is your issue solved? – Daniel Williams – 2017-08-31T04:39:44.193
@DanielWilliams couldn't solve it. Last progress I made is what's on the update in the question. Rohitab helped me prevent FortiSSL from undoing my route changes, but they never took effect. I was never sure if FortiSSL was doing something else behind the scenes to prevent my routes from taking effect, or if I was misunderstanding some networking concept while setting them up. – Juliano – 2017-09-01T05:00:32.233
Isn't it kind of the point for your VPN client to enforce that policy? The company probably has a security policy that requires you to not use split-tunneling, and circumventing that policy would be a security risk. – Ryan Ries – 2013-12-16T18:20:37.620
Quite the contrary. I now have access to this company's partners' IP-restricted webservices, since my web traffic goes out through their internet IP address. It's a very a lazy configuration on their part, as in "I'll tunnel everything through the VPN so I'll never have to add another IP or subnet to the route table". – None – 2013-12-16T19:09:49.210
@Juliano The point of avoiding split tunneling is to prevent users from coming in one tunnel and then having access to the data on the other tunnel. I would expect you to have the same access to the network you are tunneling to, that you would have if you were on the network. However, you don't want to use a split tunnel to grant that access to the world. – BillThor – 2013-12-17T00:02:01.023
2Actually if I were on that network I'd be able to setup my routes and metrics to give priority to the internet connection I desired (3g/4g ie.). I'd have that option because I wouldn't be subject to a ridiculously restrictive VPN client. Preventing split tunneling sounds OK in theory, but it limits me WAY more than if I was actually physically on that network. You guys are justifying a security implementation that's hurting me instead of helping me find a way out, which is the question at hand. How do I bypass this? – None – 2013-12-17T11:32:18.687
There is also interface metrics:
– mbrownnyc – 2013-12-26T13:57:40.923ncpa.cpl> NIC properties> IP v4 stack entry properties> General tab/Advanced> Automatic Metric. Look there on both interfaces. Also see this blog post about multihomed Windows.