0
Running Kubuntu 13.04
I have read this tutorial about only allowing torrent traffic with GUFW but it seems this is not working for the browser. My torrent application is working but I cant browse any website as soon as I switch outgoing to Reject. Why is the rule not working, do I need to change the anywhere to my local lan ip address or something? I am not sure if my torrent download + upload work but my browser wont connect to site, I can only connect to my localhost server.
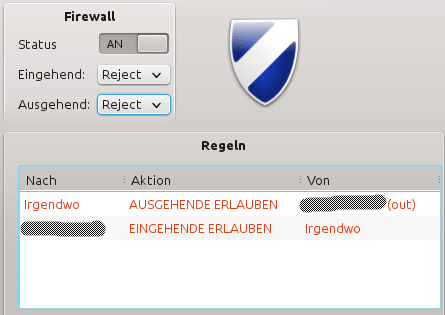
The censored is my current internet IP i got from my VPN Provider
eingehend = Incoming
irgendwo = anywhere
I just made a pingtest, while connected to the VPN, its interresting, when I allow all incoming connections the ip get resolved when I reject it is only showing the ip, but the connection is there. Maybe this helps, looks like some DNS issues but this is not my area of expertise.
ping google.de
PING google.de (173.194.113.119) 56(84) bytes of data.
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=1 ttl=55 time=53.8 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=2 ttl=55 time=47.2 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=3 ttl=53 time=58.6 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=4 ttl=55 time=64.7 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=5 ttl=53 time=69.7 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=6 ttl=53 time=72.5 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=7 ttl=55 time=58.1 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=8 ttl=53 time=54.3 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=9 ttl=55 time=78.6 ms
64 bytes from fra02s22-in-f23.1e100.net (173.194.113.119): icmp_req=10 ttl=53 time=84.1 ms
!!!!!! HERE I SWITCHED ALL OUTGOING TO REJECT !!!!!!!!!!!!
64 bytes from 173.194.113.119: icmp_req=11 ttl=53 time=81.4 ms
64 bytes from 173.194.113.119: icmp_req=12 ttl=53 time=51.9 ms
64 bytes from 173.194.113.119: icmp_req=13 ttl=55 time=106 ms
64 bytes from 173.194.113.119: icmp_req=14 ttl=55 time=47.0 ms
64 bytes from 173.194.113.119: icmp_req=15 ttl=55 time=85.0 ms
64 bytes from 173.194.113.119: icmp_req=16 ttl=53 time=47.7 ms
64 bytes from 173.194.113.119: icmp_req=17 ttl=55 time=57.1 ms
// edit
I now set up my inet connection this way, I entered the 2 DNS servers from my VPN and it's still not working as soon as I turn on the Firewall
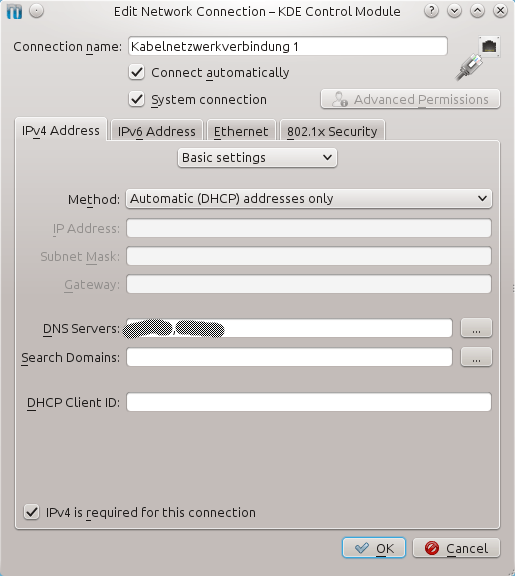
After reading over the tutorial you posted, I suspect there is a good chance that the current DNS server(s) you're device is configured to use (or received from your provider via DHCP) may have a preferred route via your default gateway (an not through the VPN), which happens to be traffic that is blocked by the UFW. – one.time – 2013-08-28T14:56:05.013
@one.time If so, how to deal with it? My DHCP gives 192.168.0.1 as DNS Server and not the actual one I guess. At least I did only set it up this way back in the days when I not used DHCP. – Wayne's World – 2013-08-28T15:09:22.517
In that case you're using your SOHO device (wireless router, provider all-in-one device, etc.) for DNS queries, which is forwarding those queries on to the DNS addresses learned from your provider. You can statically set your DNS address(es) on your 'computer' to a trusted public DNS of your choice. You're VPN provider may have a list of their own recommended or hosted DNS servers to chose from. – one.time – 2013-08-28T15:19:55.017