9
1
I'm dealing with a Windows 7 that has got a virus that starts immediately on startup, locking the screen. It also runs in safemode (even with command prompt only). Only option is to switch the computer off by press and holding the power button.
The computer also has an Ubuntu installation, so Linux access is easy. I have been searching for a way to edit windows startup applications from Ubuntu, but with no success.
Is such a thing possible? I.e., how can I edit windows registry from Linux? If not possible, what other option do I have?
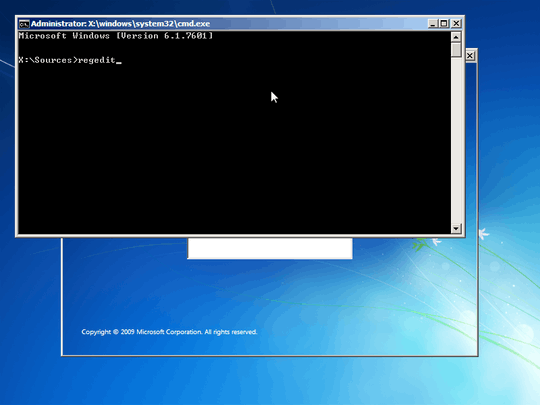
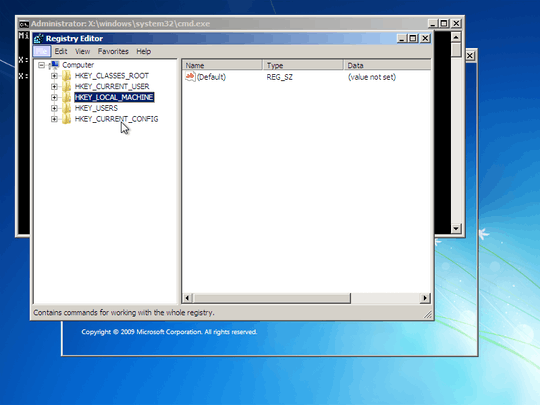
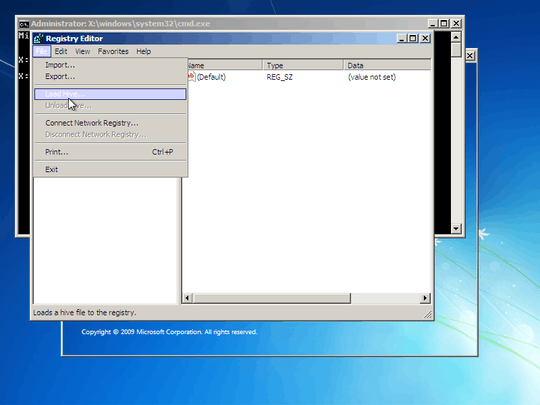

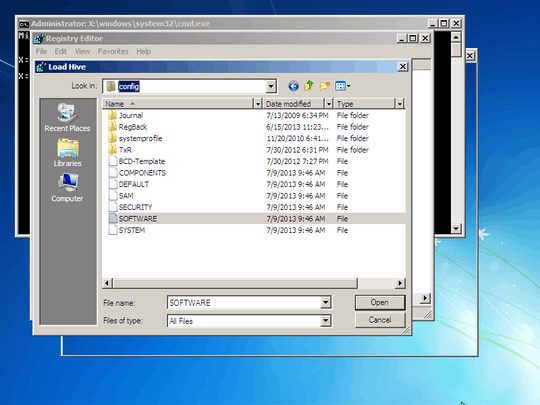
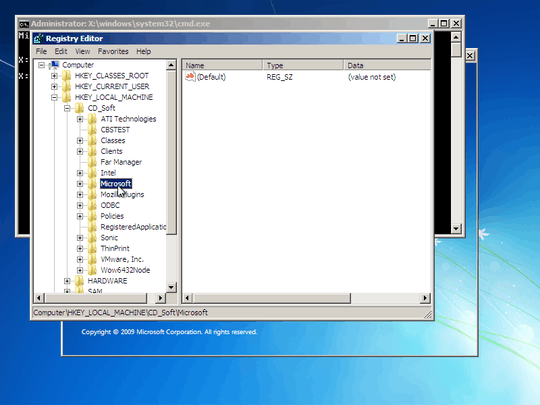
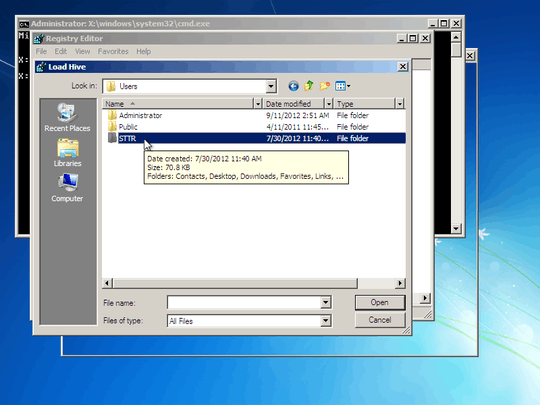
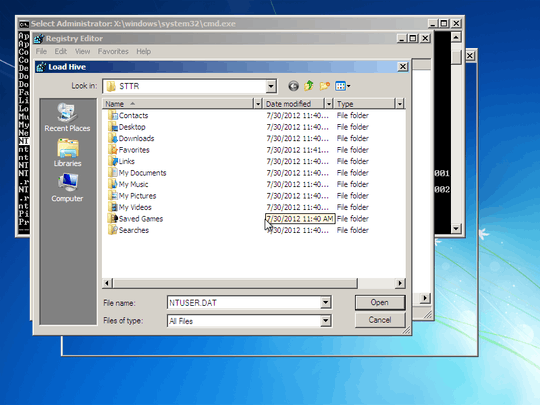
1Both answers don't indicate you should not be out right deleting those keys, just specific enteries, malicous enteries within them. – Ramhound – 2013-07-09T19:27:40.053
I was just pointing to the places where the information is stored. I never mentioned to delete the keys, only to 'edit' them. – Atari911 – 2013-07-09T22:24:56.443