11
3
I mean if one uses a VPN, can the ISP still see or know what exact URLs one visits or downloads from? By that I mean any URLs we type in our browser or even use URL Links in like jDownloader downloading data over HTTP.
For I think the Connection that the user makes to VPN goes through ISP only like this:
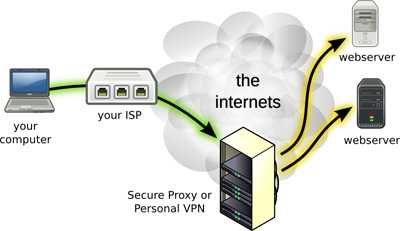
As we know VPN tunnels are encrypted, but how well encrypted are they really?
I read this and I didn't quite exactly understand, What he meant to say by corporate network and split tunnel. And what if one just uses net from home. What exactly did he mean to explain?
Yes the ISP can see your surfing traffic and DNS queries if your VPN is set up as split tunnel (where only traffic going to your corporate network goes over the encrypted VPN tunnel and every thing else goes out the regular internet path)
I also came to read this thing about URLs/IP Blocking:
To block content, all an ISP has to do is check the URL (website address) against a blacklist of banned sites, to decide whether the user should be accessing it. This same technology can be used to track people watching banned content as well. A method used to track the viewing of accessing a blacklisted website would trigger an alert.
So I wanted to know, while if accessing blocked/blacklisted URLs through a VPN, can it trigger an alert at the ISP end? I mean will they be able to see/know, what URLs one has Visited?
5If your ISP could listen in to your VPN traffic they would have called it Virtual Public Network :) – Jack – 2013-06-19T10:25:04.997
3The answer to your question depends on if the connection to the VPN is secure. Just disregard somebody with 11 reputation who offered no additional details, and posted a single response. As for if a VPN connection is encrypted or not encrypted I have not seen any VPN service offered where it does not use encryption. – Ramhound – 2013-06-19T11:40:42.360
@Ramhound Citing anyone's reputation as part of your argument devalues it. You can call it what it is, not helpful, but even that argument is moot because it's a comment and not an answer. – Jack – 2013-06-19T22:53:52.650
@Jack - The quoted text was posted as an answer, without any supporting documentation, I disregard answers like that almost all the time. We really going not agree the quoted text is just wrong? – Ramhound – 2013-06-20T11:32:46.883
I agree the answer is crap, I thought you were referring to my comment :) – Jack – 2013-06-20T12:13:41.570