13
5
Background
Most installation toolkits have the ability to launch, automatically or otherwise, external programs after installation. This is often appears in the installer via such options as "Show readme", or "Start program".
Issue
The problem is, many of these installers are poorly coded, and do not drop permissions appropriately. For example, starting the application automatically, or opening the application's homepage in the browser, often results in launching the application or browser with the installer's Administrative privileges, or a "High" UAC integrity level!
This has the potential to open up security breaches, by opening up the installed application, or a web page (and possibly browser add-ons), that are now running with elevated permissions.
(This is the reason I strongly recommend never choosing auto-launch options when installing software.)
Question
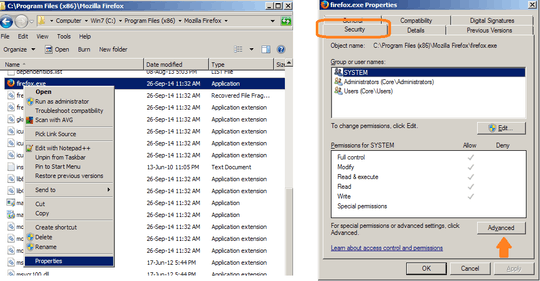
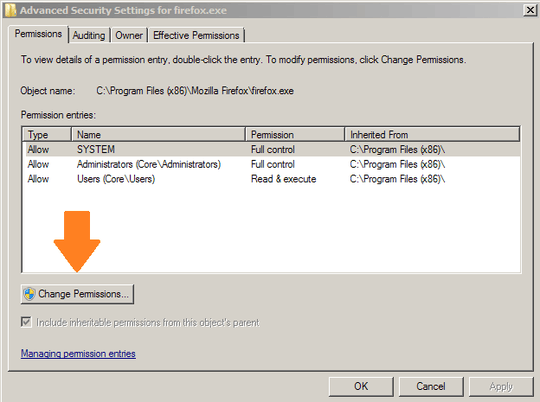
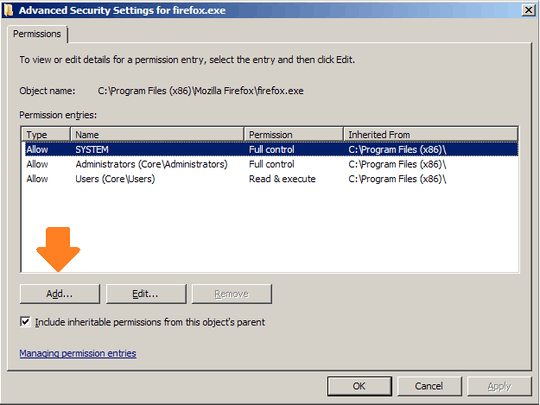
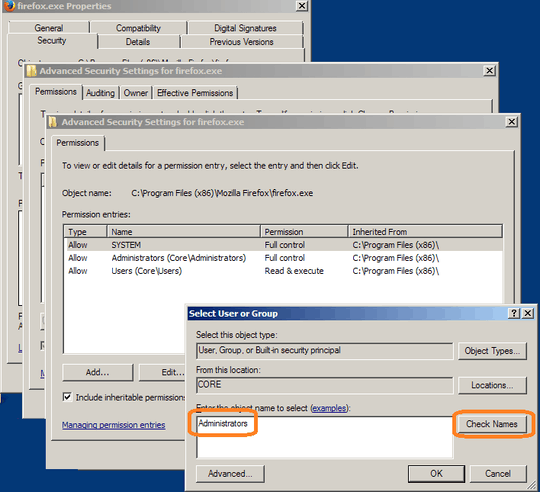
Is there a way to prevent certain applications (such as a web browser) from ever being launched with Administrative privileges, i.e., an automatic drop-privilege based on process name?
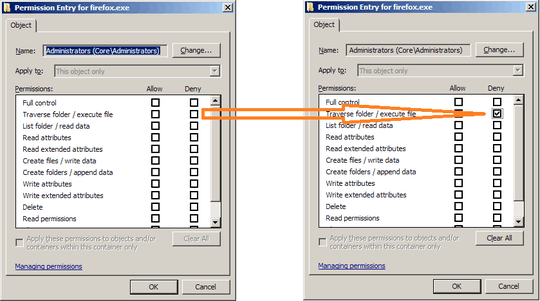
2I really like this question. There are products to raise rights for processes based on path, hash, etc. I'd love to see something that drops rights automatically for, say, iexplore.exe, firefox.exe, chrome.exe, etc. – Patrick Seymour – 2012-09-09T21:44:52.567
1If the spawning program has admin rights, couldn't it just undo whatever you come up with and run it anyway? :) – Ƭᴇcʜιᴇ007 – 2012-09-09T21:56:07.887
1I guess it could, but I would be surprised if an installer was like, "Hey, you're gonna browse our home page as administrator, buddy!" and continually enforced those permissions. I don't think I'd buy software from a company like that, provided I could find out about it. – Patrick Seymour – 2012-09-09T22:09:20.727