For an organisation then a password policy is both a good and bad idea. Any system of generating passwords will cause a smaller set than a truly randomly generated password. To help with that things like the XKCD story system work quite well as they avoid personal items about the user which could be known or discovered.
As an example suggesting that users use their name, with voles substituted for numbers (a=1,b=2,etc) will generate something that looks random to the average person but is easy to break. Incorporating another word like job title, department or mothers maiden name will add to the abstration but you still basically have something that a disctionary attack should pick up. All be it that now you have increased the dictionary attack time from Proper Nouns in (western?) culture + Proper Nouns with vowel subs.
ThomasSoftwareEngineer becomes Th4m1sS4ftw1r22g3n22r
Looks random but is not very random to a software program. Certainly not to one that know the user is a Software Engineer called Thomas.
If you add to the above a collection of stores that people could incorporate, some memorable but obscure things might be:
- Childhood memories
- Secret crushes
- Nemesis
- First Cars
- Car number plates
- Narratives from a book they like
This could create something a little more lengthy and for passwords longer is almost always better. Thomas had a Astra as his first car and he drove it into a ford in a river.
ThomasAstrafordriver
Again that is is only 4 dictionary words but it starts to be memorable. I could increase the entropy by including the year I got the car or that I broke it.
ThomasAstra2005fordriver2006
I could further up the entropy by choosing some symbol to use as a space, _ and - are well known but they are better than nothing and anything that is permitted could be chosen.
Thomas#Astra#2005#for#driver#2006
Now that is memorable, has a high entropy and should take someone a little time to guess. As with all good passwords it will take me some time to learn to type it fast but if you can easily type a password it is probably not a good one.
Now I would not recommend you use or type a password you really care about into any browser so you might want to use similar ones rather than actual one but...
https://www.grc.com/haystack.htm
The above website provides a nice was to see the size of the search space for a password. It does not measure strength but it gives you an idea that length is important as is using caps, numbers & symbols:
Password Search Space Size
ThomasSoftwareEngineer 5.76 x 10^37
Th4m1sS4ftw1r22g3n22r 4.44 x 10^37
ThomasAstrafordriver 2.13 x 10^34
ThomasAstra2005fordriver2006 1.56 x 10^50
Thomas#Astra#2005#for#driver#2006 1.86 x 10^65
Other things I have heard recommended is that you take users passwords and run them through a local, secure, powerful server with a password cracking tool doing dictionary and brute force attacks. If you can crack the password in a week then so can someone else. When you crack it expire the password and ask the user to make a new one, possibly providing them hits.
--endit to answer the question or "How much less secure than truly random"---
I had put this as a comment but it fits better as an addition to the answr. Carrying on from my above examples:
How secure these multiple word passwords are compared to truly random character passwords depends how you want to treat dictionary words. If we use entropy calcs as explained here:
[http://blog.shay.co/password-entropy][1]
H=Llog2N where L is the length of the password and N is the size of the alphabet
We can do things in two ways. If we chose to treat each dictionary word as one symbol in the alphabet then ThomasSoftwareEngineer is only L = 3 but what is N? Well Google and OED say there are about 200,000 words in the English language so we get:
H = 3*log[base2]*200,000 = 52.83
Which is Similar to a 9-alpha-numeric char password.
If you then allow the substitution of some vowels with numbers you double your alphabet size to about 400,000 so it becomes
H = 3*log[base2]*400,000 = 55.83
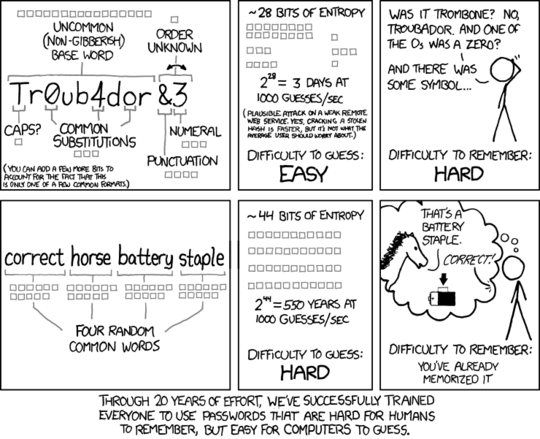
The XKCD comic uses 4 dictionary words instead of 3, these takes us from an Entropy of 52.8 for 3 words (no numerics) to:
H = 4*log[base2]*200,000 = 70.44
70.4 is about the same entropy as a 12 character Alphanumeric password ( H = 12*log[base2]*62 = 71.45) so the question is can you remember 12 random numbers and letters as well as you can remember 4 non-related English words? Obviously a longer password (more words) is always going to be better and you should avoid short words (as 4 * 3-letter words is only 12 alpha characters which is an entropy of 68.4).
So here is the entropies you get for each style of password:
Numeric Passwords (N = 10)
Entropy (H) Length (L) Alphabet Size (N)
9.965784285 3 10
13.28771238 4 10
16.60964047 5 10
Case Insensitive Alphabetic Passwords (N = 24)
13.7548875 3 24
18.33985 4 24
22.9248125 5 24
Case Sensitive Alphabetic Passwords (N = 52)
17.10131915 3 52
22.80175887 4 52
28.50219859 5 52
Case Sensitive Alpha-Numeric Passwords (N = 62)
17.86258893 3 62
23.81678524 4 62
29.77098155 5 62
Case Sensitive Alpha-Numeric Passwords with symbols on a QWERTY keyboard (N = 94)
19.66376656 3 94
26.21835541 4 94
32.77294426 5 94
Passwords formed using a random selection of 200,000 words from the English Language (N=200000)
52.82892142 3 200000
70.4385619 4 200000
88.04820237 5 200000
As above but assuming you know 20,000 words (N=20,000)
42.86313714 3 20000
57.15084952 4 20000
71.4385619 5 20000
Note: 20,000 words is the estimated number an educated English user will know so it is perhaps a better choice as a guess of what people will chose. Still it shows that 3 common words makes a password that is better than a 5-char totally random password from a QWERTY keyboard.
Wait,
getRandomNumberis bad? – ta.speot.is – 2012-08-31T10:32:24.710Unfortunately most sites have length limits to prevent the technique, but better than a "password" is a "passphrase" such as "oldmotherhubbard" or "ahottimeintheoldtowntonight". These are more characters to type but they flow more naturally from the fingers and are easier to remember. – Daniel R Hicks – 2013-01-04T13:30:54.897