Peter A. H. Peterson at UCLA wrote a proof of concept technology and developed the theory for securely running your system with encrypted RAM, and the solution is expressly designed to prevent cold boot attacks. The name of his paper is Cryptkeeper. I don't know if he makes the software available for download or if it is possible to license it from UCLA. However, it is apparently possible, at least in principle, to design a cryptosystem for RAM that is secure even if the entire contents of RAM is disclosed.
The measured performance impact of this solution is between a 9% overhead and a slowdown by a factor of 9, depending on how "pathological" the scenario is. The 9% figure is cited as applying to browsing the web with Firefox, but they didn't state what use case would slow down the performance by a factor of 9.
Peterson's solution does not "wipe" the RAM as you suggest. Rather, it uses a "secure key-hiding mechanism" to prevent the decryption key from being disclosed just by virtue of obtaining the contents of RAM. I am not sure of the details of the implementation, but I assume it is explained in the paper.
The paper was published in 2010.
It is available for purchase on IEEE's ieeexplore website. It is also available for direct download as a PDF without charge from someone's website; it is up there on the google search results for "cryptkeeper RAM"... but I'm not sure how long that result will stay up there.
I was tempted to make this a comment rather than an answer, because this solution does not "wipe" RAM as you asked. However, I believe that if Peterson's research is technically correct, this will have the same practical effect -- or possibly even a "better" effect -- than wiping the RAM. The reason is that a skilled physical attacker could probably interrupt your system program's attempt to wipe the RAM if they were expecting such an operation to occur -- for example, pulling the battery out of the unit or holding down the power button before the operation can complete. Peterson's solution is more secure because it is not based upon a necessary time window under which the computer is permitted to continue executing instructions in order to complete the wipe. Instead, memory is constantly protected, even if the CPU itself is instantaneously killed by some incredible feat of technology before you even have a chance to react to the attacker.
And by "incredible feat of technology" I mean something like Stuxnet.
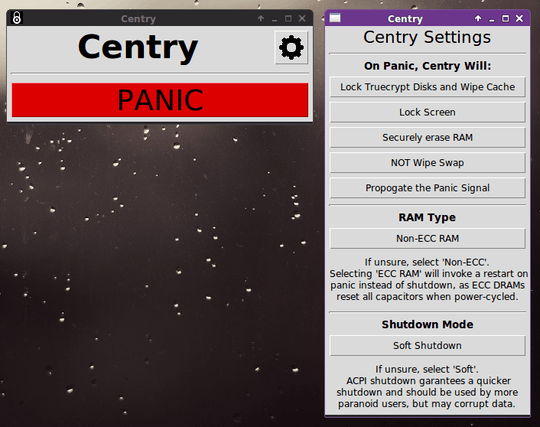
6How do you intend to detect the "shutdown"? The power is simply gone, not much you can do about that in software. And since the attacker has physical access, relying on an USV is problematic. To quote the wikipedia article you linkes: "To execute the attack, the machine is cold-booted. Cold-booting refers to when power is cycled “off” and then “on” without letting a computer shut down cleanly, or, if available, pressing the “reset” button. " – CodesInChaos – 2012-08-21T09:51:16.257
1Detect shutdown? User clicks "shutdown" or clicks a panic button. I'll add the clarification to the question. – James Mitch – 2012-08-21T11:05:03.077
Here is the only way I know how to prevent a "Cold Boot Attack" you sit at your desk for 5 minutes after you shut your computer down. Your question still makes no sense, for instance, "Can you port please ..." makes no sense. – Ramhound – 2012-08-21T11:15:49.690
1It makes a lot sense. If it wouldn't make sense, Tails and Liberte Linux wouldn't feature it. It's just a logical step to use it also for desktop operating systems, which are not Live CDs. – James Mitch – 2012-08-21T11:21:31.313
2Use case: it knocks on the door. Current situation: you can shut down but it takes 5 minutes until encryption goes effective (risk of cold boot attack). With a RAM wipe script: press the panic button and everything is almost instantly secure. When the script is ready it could easily be expanded, go active when removing an USB drive. That could even work if someone robs a notebook, if the victim is fast enough to remove the USB drive. – James Mitch – 2012-08-21T11:25:47.297
The "can you port" has now a different formulation. – James Mitch – 2012-08-21T11:27:19.883
Surely you wouldn't need to reboot into a new kernel in order to do this but instead have a kernel module that runs as the last item in the shutdown. IIRC when Linux is shutting down it basically unmounts all disks and surely just after that it is easy to allocate all the system memory, write 0's to it and finish shutting down. Better yet I would have thought this should be a part of the encrypting filesystem, after it gets unmounted and prior to unloading it can easily wipe its keys as it knows where they are stored... Anything more sounds like an extreme case of paranoia. – Mokubai – 2012-08-21T12:27:55.337
4Tell us if you have a RAM DDR2 or DDR3. DDR3 are immune to Cold Boot Attack. They only keep voltage for couple of seconds after forced power off. If you here knocking then pull the plug. If you have older RAM - i would enable TWO things in BIOS - 1. AutoStart after Power loss to last known state. 2. Ram size Check at each boot. This will allow you to Pull the plug, plug it back and go to door while your BIOS will clear the RAM for you and load System after that. This is quicker then you will ever need. – mnmnc – 2012-08-21T13:56:28.380
4It's 2012. There is no Cold Boot Attack anymore unless you are using 10 year old laptop. If i would want to get to your encrypted data i would exploit the system security hole or send you a trojan horse to get your data for me. The same would be done by State agencies. Breaching the door and attempting CBA is too risky in light of currently available encryption algorithms. It would be enough to have a not common screws in your box and anyone attempting CBA would leave empty handed after you pulling the plug. – mnmnc – 2012-08-21T14:19:54.287
@Mokubai that a kernel module or the encryption software wipes the keys is a good start. For good privacy, everything else should be wiped as well. – James Mitch – 2012-08-21T16:52:17.163
@mnmnc my BIOS does not have such options. And if it had, it wouldn't be a safe method unless the researched tested that it will really wipe the RAM. – James Mitch – 2012-08-21T16:55:10.437
@mnmnc About your 2012 / DDR3 RAM answer... Commented on it below your answer below. – James Mitch – 2012-08-21T16:58:14.397
6You know, this degree of paranoia will only make the black helicopter guys that much more interested in you. – Daniel R Hicks – 2012-08-21T17:43:19.220
1@DanH More likely fat guys in an NSA datacenter with sunglasses and a 'I 0x3C 0x33 AES' t-shirt – mnmnc – 2012-08-21T17:49:07.960