2
1
If I connect using a DSL line, what advantage do I have in using SSL (for "minor" activities (like banking, to exclude espionage, top-secret-business plans)) ? I assume that most people will not literally wiretap a sing home-user's line.
Once the data gets to ISP (AT&T), there shouldn't be any more danger (There isn't much for AT&T to steal from my bank, yet they can be sued for using data going through their servers).
The Internet backbone should be secure for roughly the same reason - no company will want to break the law through stealing my credit card number (Yes, I know, companies may not always be trusted. Yet, I am only transferring bank/CC#s. The amount they could steal would be incomparably smaller than the amount I can sue them for stealing it).
Same for the server. It is (probably) connected through T1 lines administrated by a large sueable company. Once it gets to the web-server, SSL no longer protects the data (against crackers, etc.)
So, in contrast to the days when the average ISP was a small dialup company who could scam one's bank statements and run, how much more secure is an SSL connection vs. a non secure connection?
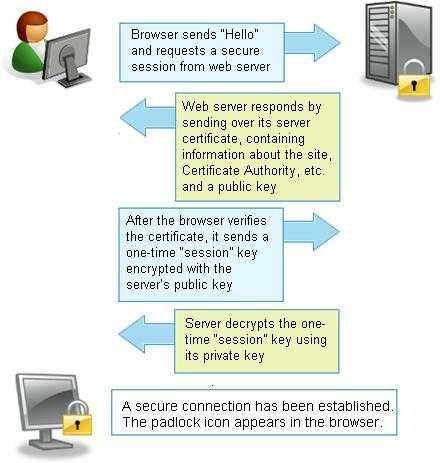
Why do you feel the internet backbone is "secure". Companys, their employees and governments do illegal things all the time - especially if they think they won't get caught. Don't be an easy target. – uSlackr – 2012-04-05T01:02:49.783
1"they can be sued", "I can sue them" - This would be funny if it wasn't so misguided. Suing someone after the fact is not a viable security plan. Criminal hackers do not worry about being sued by you or anyone else. You simply do not have the resources, time or money to find then, take them to court and win. Besides, they may not even be in the same country as you. – sawdust – 2012-04-05T08:28:44.603