8
2
I'm trying to track down WHY I can write in a folder that, by my best estimation, I should not be able to write. The folder is shared with "Everyone" has "Full Control", with the files being more restrictive. My best guess is there's some sort of sub-group membership that's allowing me to write, but the nesting of groups that exists in our Active Directory is pretty extensive.
Is there a tool, that will tell me which of the ACL entries allowed or disallowed my writing a file in a folder?
The Effective Permissions dialog is marginally helpful, but what I need is something like a "NTFS ACL Trace Tool", if such a thing exists.
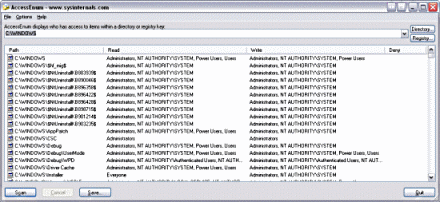
Once you give a large group (like Everyone) permissive settings, smaller groups can only restrict that by using DENY permissions. You could be a member of a group that has few permissions, but unless you specifically DENIED a privilege, your de facto membership in the EVERYONE group will allow you to have access. – Joel Coehoorn – 2012-10-24T16:41:33.743
I don't quite remember what led me to ask this in the first place. But if I'm right, I think it was something silly like "OurDomain\All Users" were added to the Local "Users" group. something, for some reason group policy wouldn't let me (lowly developer) alter. – hometoast – 2012-10-24T16:55:16.437