Why?
- Because they want you to think about what you're doing
- Because it prevents accidental installations
- Because it prevents maliciously triggered installations
How can you maliciously trigger an installation?
Here's an interesting article about race conditions in security dialogs by Jesse Ruderman:
Another form of the attack involves convincing the user to double-click a certain spot on the screen. This spot happens to be the location where the 'Yes' button will appear. The first click triggers the dialog; the second click lands on the 'Yes' button. I made a demo of this attack for Firefox and Mozilla.
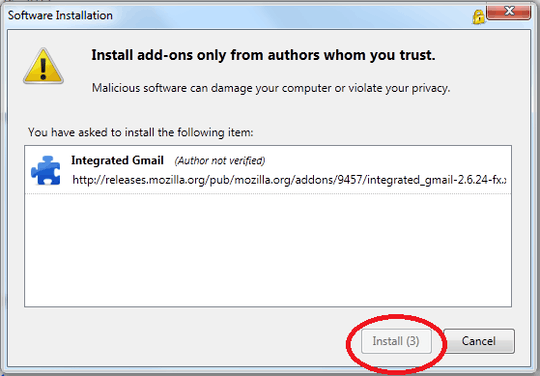
Firefox's solution, from bug 162020, is to delay enabling the "Yes"/"Install" buttons until three seconds after the dialog appears. I believe that this is the only possible fix other than completely denying untrusted content the ability to pose the dialog. Unfortunately, this fix is frustrating for users who install extensions often.
Basically, it all comes down to predicting when a user would click and then intercepting that click within an installation dialog. Ruderman explained a more concise game situation like this in his bug report from Firefox, which ultimately led to the inclusion of the delay period.
To summarize again, his main point was:
If I can control or predict when and where a user will click, I can get them to
install software.
Any alternatives to the delay period?
The delay period was certainly only one way of dealing with this. Another one could have been shuffling the buttons for "Install", "Cancel" every time you would install something. This is something used very often, but it confuses the user more than it helps.
Another idea would be moving the window location randomly for every dialog. This has the same result as shuffling the buttons, namely confusing the user.
Also, introducing randomness is not the ultimate solution. If there are keyboard shortcuts for the buttons, you could intercept keypresses as well. That all being said, it seems more like a legacy feature today, as most plugins are installed from the official Firefox add-on website anyway.
12The question should be "why is Mozilla the only one doing this?". IMHO, every new dialog should enable the buttons 1 sec after showing them because you might accidentally click it (or someone wants you to click it without your consent). I really hate it when I click somewhere and a button spawns there just before I click. It also happens with phones when someone calls you right at the moment you want to tap that 'play' button. – Mike – 2011-08-08T13:31:41.073
4"If you answer this question, please provide references from Firefox mailing lists or commit logs." If this is your requirement, then can't you do your own searching? – kmm – 2011-08-08T17:33:59.213
2Maybe it's not that easy to find, or there are some other things to consider. Maybe somebody here would have had more internal information -- who knows? It's not bad to ask per se @Kevin – slhck – 2011-08-08T18:08:12.770
I tried to look myself, but I couldn't find the information. (I said so in an edit hours ago, which was somehow lost: http://superuser.com/users/68351/aantn?tab=activity#apage_1-afilter_revisions)
– Natan Yellin – 2011-08-08T19:04:18.470@aantn Sorry, I had removed it as it didn't really add necessary information to the question. We generally expect people to search first, so there's no need mentioning it :) – slhck – 2011-08-08T19:10:14.003