Ian, you do not understand how protected mode works. Simon Capewell's solution is a valid way to increase the security of Firefox. You example, asserting that his solution somehow disables the entirety of the protection of low integrity level is completely false. Chrome and IE use the same methods, as downloads are written to the download folder even under protected mode IE. Otherwise, you would be unable to download anything. Although IE may use a wrapper of sorts, thus isolating the main process from those that process untrusted data for added security as Chrome does, this is moot as in the above described methods, all components of Firefox are isolated from tampering with the system. Whereas, in Chrome, the main process runs at Medium integrity and the rendering processes at Low integrity.
Configuring Firefox in this way protects Windows and Program Files from modification, thus isolating Firefox from the rest of your machine. Firefox is prevented from dropping malware into your Startup folder, for example, or adding a registry entry which automatically starts malware dropped into your downloads folder (which firefox is allowed to write to) at startup. Additionally, running Firefox as low integrity level protects against Firefox attempting to bypass the ACLs enforced upon it by methods such as creating a thread in a remote process in order to run code in the security context of that process. Firefox is still allowed to drop files into Temporary Folders, and potentially executables, as are Chrome and IE. Thus, integrity levels must be combined with SRP or AppLocker, in order to prevent the execution of any executables dropped into the directories which Firefox is allowed to write to. This requirement is also present with IE and Chrome.
Once done, Firefox will be hardened against drive-by downloads and be protected more so than IE, as Protected Mode IE does not, when not combined with SRP or Applocker, provide sufficient protection. In no way is allowing Firefox to write to its own directory and temporary folders any different from what Protected Mode Chrome and Protected Mode IE are allowed to do.
The only pitfall from this solution: I have a bad habit of leaving executables inside my Downloads folder, which I later run. These executables could potentially be tampered if Firefox is exploited after they are downloaded. Thus, after downloading a file, move it out of the Downloads folder. There is also a very small risk of a vulnerability in Firefox being exploited in order to modify a temporary file in the allowed temporary folder which then exploits a vulnerability in a higher integrity level process when it uses that temporary file. However, this will never happen and is only a theoretical vulnerability.
Further reading/Sources:
Windows 7 SRP (works on Home Premium, although you do not have AppLocker):
http://www.wilderssecurity.com/showthread.php?t=262686
Integrity Levels:
http://www.symantec.com/connect/articles/introduction-windows-integrity-control
Protected Mode IE:
http://msdn.microsoft.com/en-us/library/bb250462(VS.85).aspx
Basic Information about "Drive-by Downloads":
http://www.wilderssecurity.com/showthread.php?t=241732
Details of Chrome on Windows Sandboxing (its more than just integrity levels):
http://www.chromium.org/developers/design-documents/sandbox
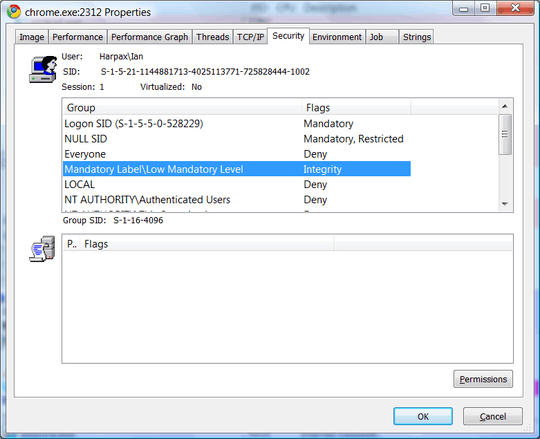
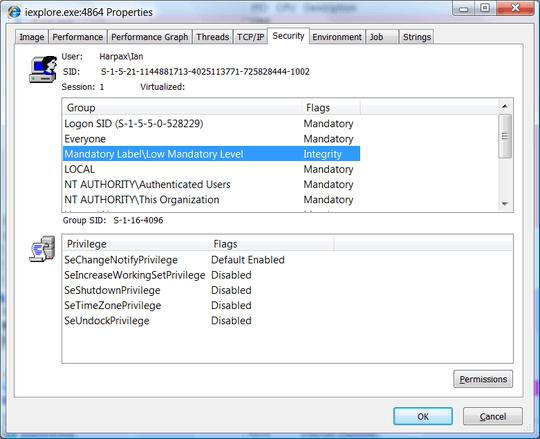
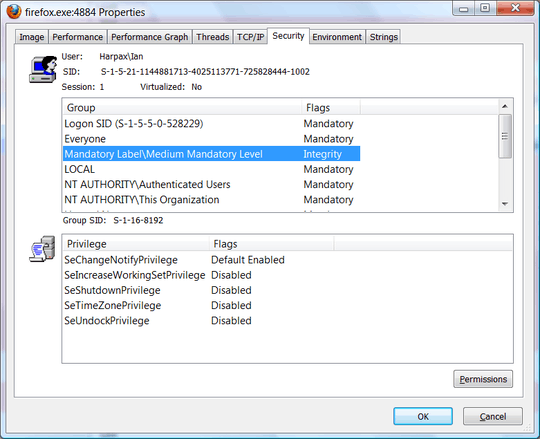
Jeez, why does IE get the "bad security" rap? – Mark Sowul – 2013-11-30T18:43:34.007