2
1
I have installed an OpenVPN server on my OpenWrt 10.03 router [freshly flashed]:
echo "nameserver 8.8.8.8" > /etc/resolv.conf; opkg update; opkg install luci-app-openvpn openvpn openssl-util openssh-sftp-server ntpd
vim /etc/ssl/openssl.cnf # modify a few lines
[ CA_default ]
dir = /etc/openvpn
new_certs_dir = $dir/certs
certificate = $dir/ca.crt
private_key = $dir/ca.key
touch /etc/openvpn/index.txt; touch /etc/openvpn/serial; echo 01 > /etc/openvpn/serial
openssl req -nodes -new -x509 -keyout /etc/openvpn/ca.key -out /etc/openvpn/ca.crt -days 3650 # give a common name, like: vpnserver
openvpn --genkey --secret /etc/openvpn/ta.key
openssl req -nodes -new -keyout /etc/openvpn/server.key -out /etc/openvpn/server.csr # give a common name, like: vpnserver
mkdir -p /etc/openvpn/certs; mkdir -p /etc/openvpn/private
openssl ca -out /etc/openvpn/server.crt -in /etc/openvpn/server.csr
time openssl dhparam -out /etc/openvpn/dh1024.pem 1024 # it could take 10 minutes!
# generate certs for clients [X = client number]
openssl req -nodes -new -keyout /etc/openvpn/clientX.key -out /etc/openvpn/clientX.csr # give a common name! it will be the user name
openssl ca -out /etc/openvpn/clientX.crt -in /etc/openvpn/clientX.csr
# e.g.:
openssl req -nodes -new -keyout /etc/openvpn/client1.key -out /etc/openvpn/client1.csr # give a common name! it will be the user name
openssl ca -out /etc/openvpn/client1.crt -in /etc/openvpn/client1.csr
vim /etc/config/openvpn
config 'openvpn' 'openvpn_server'
option 'enable' '1'
option 'port' '1194'
option 'proto' 'udp'
option 'dev' 'tap'
option 'ca' '/etc/openvpn/ca.crt'
option 'cert' '/etc/openvpn/server.crt'
option 'key' '/etc/openvpn/server.key'
option 'tls_auth' '/etc/openvpn/ta.key 0' # server: 0
option 'dh' '/etc/openvpn/dh1024.pem'
option 'comp_lzo' '1'
option 'server' '10.20.30.0 255.255.255.0'
option 'keepalive' '10 120'
option 'persist_key' '1'
option 'persist_tun' '1'
option 'mute' '20'
option 'verb' '3'
option 'client_to_client' '1'
list 'push' 'dhcp-option DNS 10.20.30.1'
/etc/init.d/openvpn enable
/etc/init.d/openvpn start
ifconfig -a | less
ping 10.20.30.1
# here comes the firewall part
vim /etc/config/firewall # modify it
config 'include'
option 'path' '/etc/firewall.user'
config 'redirect'
option 'src' 'wan'
option 'proto' 'udp'
option 'src_dport' '1194'
option 'dest_port' '1194'
option '_name' 'OpenVPN'
vim /etc/firewall.user # modify it
iptables -t nat -A prerouting_rule -i $WAN -p udp --dport 11194 -j ACCEPT
iptables -A input_rule -i $WAN -p udp --dport 11194 -j ACCEPT
iptables -A forwarding_rule -i tap+ -o br-lan -j ACCEPT
iptables -A forwarding_rule -i br-lan -o tap+ -j ACCEPT
iptables -A input_rule -i tap+ -j ACCEPT
iptables -A output_rule -o tap -j ACCEPT
/etc/init.d/firewall restart
# tar the files that goes to the client1
mkdir -p /root/client1
cp /etc/openvpn/ca.crt /root/client1/; cp /etc/openvpn/client1.crt /root/client1/; cp /etc/openvpn/client1.key /root/client1/; cp /etc/openvpn/ta.key /root/client1/
cd /root/; tar -cf client1.tar client1
It seems "ok".
I connect my pc to the lan port of the router, and i want to try it out. I'm using Fedora 14 with GNOME. In the NetworkManager applet i set these things:
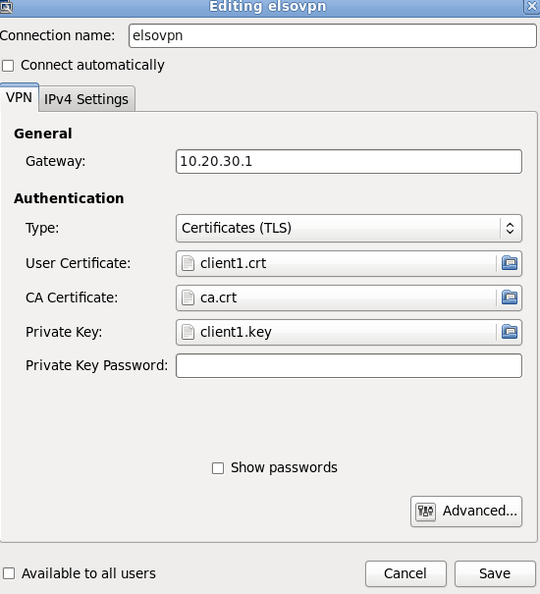
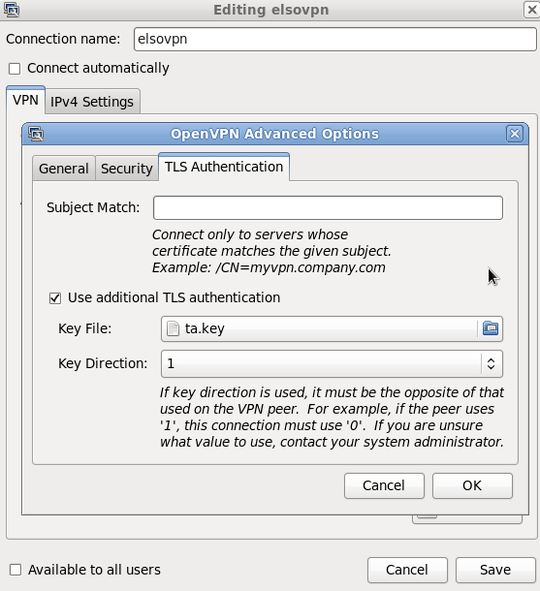
I try to connect, but it fails. Here are the logs:
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> Starting VPN service 'openvpn'...
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN service 'openvpn' started (org.freedesktop.NetworkManager.openvpn), PID 23552
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN service 'openvpn' appeared; activating connections
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN plugin state changed: 1
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN plugin state changed: 3
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN connection 'elsovpn' (Connect) reply received.
Mar 7 15:42:43 ASDF nm-openvpn[23554]: OpenVPN 2.1.1 i686-redhat-linux-gnu [SSL] [LZO2] [EPOLL] [PKCS11] built on Jan 5 2010
Mar 7 15:42:43 ASDF nm-openvpn[23554]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Mar 7 15:42:43 ASDF nm-openvpn[23554]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Mar 7 15:42:43 ASDF nm-openvpn[23554]: Cannot load certificate file /home/g/Desktop/client1/client1.crt: error:0200100D:system library:fopen:Permission denied: error:20074002:BIO routines:FILE_CTRL:system lib: error:140AD002:SSL routines:SSL_CTX_use_certificate_file:system lib
Mar 7 15:42:43 ASDF nm-openvpn[23554]: Exiting
Mar 7 15:42:43 ASDF kernel: [55630.235164] type=1400 audit(1299508963.340:23608): avc: denied { read } for pid=23554 comm="openvpn" name="client1.crt" dev=dm-1 ino=3019385 scontext=system_u:system_r:openvpn_t:s0 tcontext=unconfined_u:object_r:user_home_t:s0 tclass=file
Mar 7 15:42:43 ASDF NetworkManager[1458]: <warn> VPN plugin failed: 1
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN plugin state changed: 6
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> VPN plugin state change reason: 0
Mar 7 15:42:43 ASDF NetworkManager[1458]: <warn> error disconnecting VPN: Could not process the request because no VPN connection was active.
Mar 7 15:42:43 ASDF NetworkManager[1458]: <info> Policy set 'Auto Ethernet' (eth0) as default for IPv4 routing and DNS.
Mar 7 15:42:49 ASDF NetworkManager[1458]: <info> VPN service 'openvpn' disappeared
one important thing: my routers [the one with the openvpn server] ip address is 192.168.1.2, and i didn't had to write it nowhere. so how could the networkmanager applet know the ip address of my openvpn server? i think this is the problem, but i just can't find where to write 192.168.1.2
I tried to search Google for: "No server certificate verification method has been enabled." but i didn't find a thing, and i'm trying for hours now... :\
p.s.: if i [on the router]:
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables -t nat -P PREROUTING ACCEPT
iptables -t nat -P POSTROUTING ACCEPT
iptables -t nat -P OUTPUT ACCEPT
iptables -t mangle -P PREROUTING ACCEPT
iptables -t mangle -P OUTPUT ACCEPT
And stat tcpdump, and try to connect from my pc, nothing happens!.. so the bug is in the networkmanager applet!?
again, p.s.: if i:
$ telnet 192.168.1.2 1197
Trying 192.168.1.2...
telnet: connect to address 192.168.1.2: Connection refused
$connbsp;
Are there any good howtos about setting this kind of openvpn [as in the pastebin link, on an openwrt router..]?
Is it worth finding another openvpn client program? [other then the networkmanager applet]
i started the openvpn daemon via terminal, and when i wanted to log in via vpn, then the terminal connection got broken, the openvpn daemon stopped, and that's why i couldn't connect. – LanceBaynes – 2011-12-18T13:42:57.763