157
52
This is the second time I've had a drive-by executable installed on my machine using the following:
- Google Chrome 6 (latest)
- Windows 7, UAC on
This happened while I was browsing for images to add to a gaming.se post; one of the sites I visited (to get an image of a transfer cable) must have had drive-by browser exploit code running.
UAC alerted me that a weird temporary executable wanted to run, and I declined, but I still got the fake antivirus executable running on my machine. Sigh..
I do have Java installed because I upload stuff monthly to clearbits.net and their uploader is a Java plugin. So my best guess is, websites are doing drive-by installs using the massive numbers of zero-day vulnerabilities in the Java browser plugins.
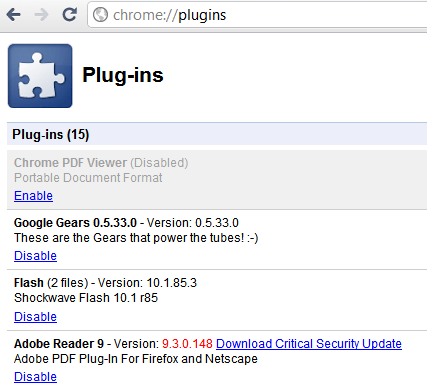
For now, I have uninstalled Java, which works. But I wondered if I could disable the Java plugin in Google Chrome instead.
So, how do you disable these vulnerable plugins in Google Chrome? I can't find the UI.

8How did you detect this drive-by executable ? – Leonel – 2010-10-20T19:00:39.797
@leonel first, UAC triggered (I declined). Then it somehow ran anyway and started begging me to install some kind of fake antivirus in the system tray.. – Jeff Atwood – 2010-10-20T19:11:43.910
5
You can always see if your plug-ins need to be updated here: http://www.mozilla.com/en-US/plugincheck/
– travis – 2010-10-20T19:16:01.467I have a Windows XP Virtual Machine set up with Java just for that reason. @Jeff Curiously, how did you go about getting rid of it? – Chad Levy – 2010-10-20T22:58:05.870
3
@paper I used http://www.microsoft.com/security_essentials/
– Jeff Atwood – 2010-11-09T00:03:07.830Thanks for the wonderful article https://stackoverflow.blog/2011/07/01/its-ok-to-ask-and-answer-your-own-questions/ .
– neverMind9 – 2019-03-14T09:43:21.6071I got a similar thing from a PDF the other day... and to top things off, if I had only remembered that I hadn't meant to open one, I could have avoided it! – SamB – 2010-12-10T22:07:39.947
1How do you know it was a vulnerability in Java and not a vulnerability in webkit? – BlueRaja - Danny Pflughoeft – 2011-06-28T04:57:28.397
@blue my Chrome is constantly updated (by Chrome itself..), but Java was massively out of date. Do the math.. – Jeff Atwood – 2011-06-28T05:00:36.540
Sorry, didn't know; but, doesn't Java come with an auto-updater? – BlueRaja - Danny Pflughoeft – 2011-06-28T16:38:42.513
I can't find it, but I know one was using a glitch in the print spooler to get around UAC, then TDSSv4/aluron started using it to inject it's rootkit. If you got the fake AV, its probably a variant of the TDSS virus that downloaded it in the background. YOU SHOULD DO A ROOTKIT SCAN RIGHT NOW! https://www.securelist.com/en/blog/337/TDL4_Starts_Using_0_Day_Vulnerability
The TDSS viruses are insanely complex, they actually have code in them that innoculates the pc to other viruses and rootkits, and run completey encrypted in hidden sections on the hardrive.
You really should do a post on it.