This is MIPS port which is present in SerComm manufactured, routers and home gateways devices (Linksys, Netgear, Cisco) used for firmware upgrades.
This is managed by scfgmgr process which is listening on port 32764.
When accessed via telnet, data prefixed by ScMM or MMcS (depending on the system's endianess) seems to be returned.
It's very simple binary protocol with header (0xC bytes) followed by a payload.
Header structure:
typedef struct scfgmgr_header_s {
unsigned long magic;
int cmd;
unsigned long len;
} scfgmgr_header;
This is based on Cisco GPL sources (e.g. wap4410n_v2.0.1.0_gpl.tgz at decommissioned ftp-eng.cisco.com).
For actual info, see elvanderb's description and sample Python code.
Currently it's famous for heap based buffer overflow which can give you full access to the device (a backdoor). This was discovered by Eloi Vanderbeken in Christmas 2013, however it was probably known by Chinese hackers back in 2008 (cgi file).
Here is how to works.
Heap based buffer overflow:
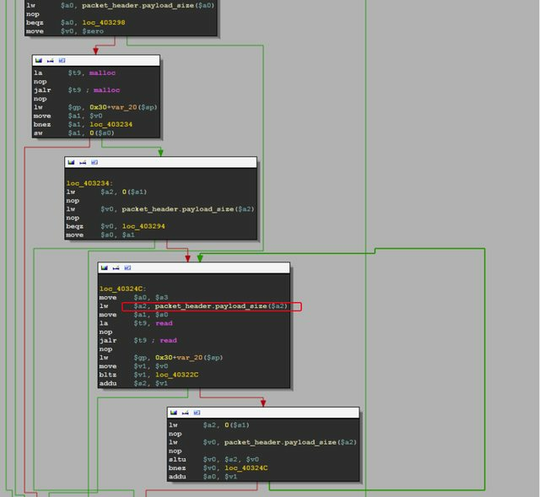
Messages:
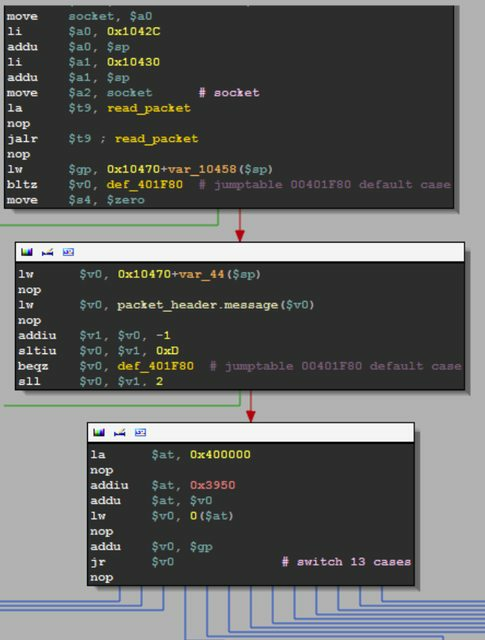
So using simple overflowing message can give a lot of interesting details:
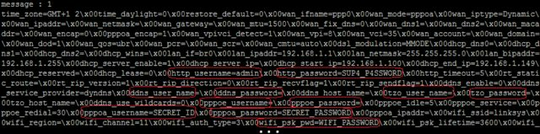
However this could cause the configuration to be reset, so don't do it at home.
Here are few reversed commands performed by the router executed via this port.
nvram - Dump configuration.
get var - Get configuration var
possible stack based buffer overflow (if variable is controlled by the user)
set var - Set configuration var
stack based buffer overflow, output buffer (size ≈ 0x10000) is on the stack.
commit nvram - Read nvram /dev/mtdblock/3 from /tmp/nvram and check CRC
set nvram (/dev/mtdblock/3) from /tmp/nvram ; check CRC
Set bridge mode ON (not sure, I didn’t have the time to test it)
nvram_set(“wan_mode”, bridgedonly)
nvram_set(“wan_encap”, 0)
nvram_set(“wan_vpi”, 8)
nvram_set(“wan_vci”, 81)
system(“/usr/bin/killall br2684ctl”)
system(“/usr/bin/killall udhcpd”)
system(“/usr/bin/killall -9 atm_monitor”)
system(“/usr/sbin/rc wan stop >/dev/null 2>&1”)
system(“/usr/sbin/atm_monitor&”)
Show measured internet speed (download/upload)
cmd (yep, it’s a shell…)
special commands:
- exit, bye, quit -> quit... (alive = 0)
- cd : change directory (a little bit WTF)
other commands:
- integer overflow in stdout handling (?) not exploitable but still ...
- buffer overflow on cmd output (same buffer again)…
write file
- file name in payload
- root dir = /tmp
- directory traversal might be possible (not tested but it’s an open(sprintf(“/tmp/%s”, payload))… )
return version
return modem router ip
restore default settings
- nvram_set(“restore_default”, 1)
- nvram_commit
read /dev/mtdblock/0 [-4:-2]
- dunno what it is, I didn’t have the time to test it
dump nvram on disk (/tmp/nvram) and commit
Source: (slide show) How Linksys saved my Christmas!
Normally that kind of ports should be officially by IANA.
This is what unSpawn replied at LinuxQuestions in 2007 related to this port:
If it's an officially IANA-assigned port (with a number between 0 and roughly 30000) then its number should correspond with a service in /etc/services ('getent services portnumber'), the services file of a scanner like Nmap or an online database like Sans' ISC.
Note that ephemeral port usage can be configured locally using the /proc/sys/net/ipv4/ip_local_port_range sysctl. An old default was 1024-5000, for servers a value of 32768-61000 is used and some applications want something like 1025-65535.
Also note these are static number-to-service mappings and while for instance /etc/services will say TCP/22 matches SSH that doesn't have to be the case in a particular situation,
Else if it's a port of which you don't know which process did bind to it then if you have access to the host you can interrogate it using netstat -anp, lsof -w -n -i protocol:portnumber or fuser -n protocol portnumber. This is the most accurate method,
Else if you do not have access to the host you could interrogate it by for instance telnet'ting to it. This is not an accurate method and in the case of a compromised host you may alert the intruder you're on her case.
See also:



What telnet client are you using? When I use Putty all I get with my netgear router is "MMcSÿÿ"... – Mokubai – 2010-07-22T22:15:07.460
1A y with double dots over it is hexadecimal 0xff, you're getting the same as me. – Dentrasi – 2010-07-23T21:00:31.693
Just to add to this because I came across this recently, here's the output now: SF-Port32764-TCP:V=5.61TEST4%I=7%D=5/8%Time=4FA9A45B%P=i686-pc-linux-gnu%r SF:(GenericLines,C,"MMcS\xff\xff\xff\xff\0\0\0\0")%r(Help,C,"MMcS\xff\xff
SF:xff\xff\0\0\0\0")%r(X11Probe,C,"MMcS\xff\xff\xff\xff\0\0\0\0")%r(LPDStr SF:ing,C,"MMcS\xff\xff\xff\xff\0\0\0\0")%r(TerminalServer,C,"MMcS\xff\xff
SF:xff\xff\0\0\0\0"); Any more insight as to why this port is open by default would be nice. – None – 2012-05-08T22:57:04.367
3https://github.com/elvanderb/TCP-32764 – mpontillo – 2014-01-03T04:28:03.720
Since this device belong to you and you are on a LAN, Maybe you can try
nmap -sV --version-all the_device_hostname. – user2284570 – 2014-01-04T01:52:59.117Possibly a TR-069 thing. – Tom O'Connor – 2014-04-11T05:54:03.337