0
One of my .dll files is unsigned, and every single time I run the program that uses it, it pops up with this warning:
I've tried to edit the following registry key to include both .exe and .dll files HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Associations\LowRiskFileTypes, but it still gives me the warning. How can I get rid of this? I don't mind if I have to disable the warning globally or anything, I'm just sick of seeing it. And to be clear, this file is not on a network share or anything--it's just on my hard drive.
I'm running the latest build (not Insider) of Windows 10 Home by the way.
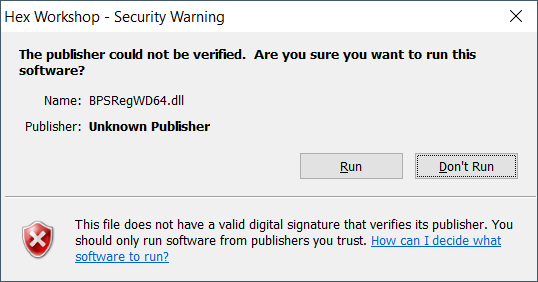
1
Possible duplicate of https://superuser.com/questions/341091/how-to-get-rid-of-the-publisher-cannot-be-verified-on-network-files and https://superuser.com/questions/853171/windows-security-warning-on-all-files-on-local-drives and https://superuser.com/questions/1256560/we-cant-verify-who-created-this-file/1256574#1256574
– Ramhound – 2020-01-12T14:53:48.607Relevant with regards to the last duplicate https://superuser.com/questions/1018145/windows-starter-edition-home-and-home-premium-do-not-include-gpedit-how-do-i-i
– Ramhound – 2020-01-12T15:00:03.497@Ramhound All group policy editor does is provide a GUI for changing registry values, right? I don't think it would help because I don't have 10 Pro so it just doesn't look for those keys (unless I'm mistaken). – Kurausukun – 2020-01-13T22:10:34.750
The duplicates are more than just that single key you modified. – Ramhound – 2020-01-13T22:11:57.027
@Ramhound The answers either refer to accessing files on network shares or using the exact registry key that I mentioned. As I said, the registry key does not work for me, and I am not accessing files over a network, so neither of these apply to me and I still do not have a solution. – Kurausukun – 2020-01-13T22:16:12.237
1"am not accessing files over a network" - Your question does mention this fact. Could you provide the relevant information from the Security and General tab on the properties of the file in question? – Ramhound – 2020-01-13T22:17:39.730
Sorry, I thought the lack of mentioning it made it clear it was not happening, especially since there are multiple other questions relating to this issue for files over a network--sadly I would have fixed this by now if that were the issue. I'm not sure what information you need, but everyone has read and execute permission for it, and the owner is SYSTEM. – Kurausukun – 2020-01-13T22:19:28.003
Does this answer your question? How to get rid of "the publisher cannot be verified" on network files?
– Burgi – 2020-01-21T15:02:27.370