1
I used hardware encryption on my Samsung EVO 850 on a laptop that recently died. The laptop used to ask for a password from the UEFI, before I was able to boot. I still have the password in a password safe, but not the encryption key.
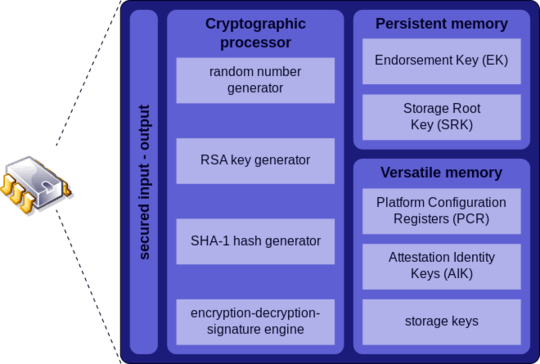
I would expect the encryption key to be stored on the disk, not on some chip of my motherboard. However, I can't figure this out when I plug my disk in another machine. I also found this schema on Wikipedia listing all types on key storage on a TPM chip in the motherboard.
Question: Can I decrypt my disk with another machine, or do I really need to original motherboard to do so?
That doesn't sound like TPM-based encryption. More likely to be OPAL (internal to the SSD). TPM would still be software – just with a hardware-based auto-unlock – and it wouldn't have asked for a password. – user1686 – 2019-12-01T12:04:24.550
There are multiple possible encryption schemes. Not all firmware supports all (or any) of them. // Are you sure the dead laptop was booting in UEFI mode? Are you sure the password prompt was provided by the firmware and not, say, Bitlocker? – Daniel B – 2019-12-01T13:32:29.357
Are you trying to boot from the recovered disk, or are you trying to attach it as a data disk to another Windows system? If it's the latter, can you show what the disk looks like in
diskmgmt.msc? – user1686 – 2019-12-01T13:49:55.193My apologies, I missed to mention something. I use Linux, and no bitlocker. So I would guess it's all UEFI? Does the brand of disk or the brand of the UEFI use dof encryption matter with regards for supported other disks? It's a bootable disk, but I don't mind mounting it as a data disk. Both are fine. Is there a Linux command to access or operate hardware encryption? – Herbert – 2019-12-01T16:22:06.073
If you were using Linux, it could also be regular LUKS-based software encryption. // Do you perhaps remember what you did to enable encryption in the first place? – Daniel B – 2019-12-01T17:39:24.307
I encrypted it from the UEFI, I actually reinstalled linux a few times and never had to worry about encryption, the UEFI just asks for a password first thing I turn it on and as far as I understand, the disk simply acts as a normal disk as far as linux can see. I think the disk was even encrypted before the parition table level. I could make and resize partitions without encryption software. The entire operating system, including /boot and /sys, was on this disk. – Herbert – 2019-12-02T08:29:48.663
I will try the
diskmgmt.msc, sorry for not doing so before, I'd need to attach the disk to some machine first :) – Herbert – 2019-12-02T08:38:45.383In that case post a
lsblk -fandfdisk -lof the disk, and provide details of how you activated this "hardware encryption" in the first place. – user1686 – 2019-12-02T16:03:47.073As a heads up, I'm still trying to figure this out, but I'm bad with anything hardware related, so it takes me more time to wrap my walnut around which machines to use, whether I can connect my disk per USB, etc. From other SE posts I've read, it seems the encryption key is stored on the disk, and the encryption is not TPM but uses a harddisk password that is passed to the disk to unlock in whatever way it wants. So this sounds like good news for my case, I am keeping my fingers crossed I can just unlock it with a Linux command and don't need a specific UEFI. – Herbert – 2019-12-13T15:06:40.647