1
1
 I have a postgresql 9.3 database running in a RHEL 6.2 kvm virtual machine. It's part of the application I support for work, and I cannot make any configuration changes to the contents of the VM itself. In production it would be deployed to bare metal, this vm is just for my own testing needs. On my Windows work computer, I can successfully connect to the database on a similar vm using SQL Developer.
I have a postgresql 9.3 database running in a RHEL 6.2 kvm virtual machine. It's part of the application I support for work, and I cannot make any configuration changes to the contents of the VM itself. In production it would be deployed to bare metal, this vm is just for my own testing needs. On my Windows work computer, I can successfully connect to the database on a similar vm using SQL Developer.
I have confirmed that I can successfully connect to the database from the vm host via psql on command line. selinux has been disabled temporarily on the vm for testing purposes.
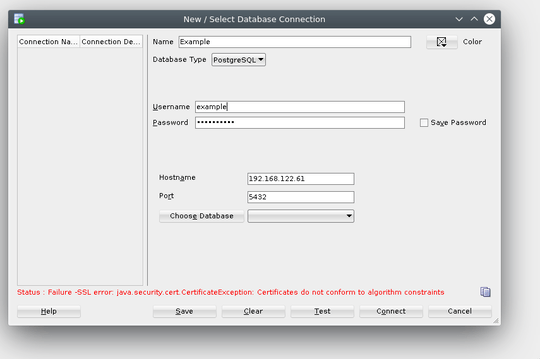
After installing SQL Developer, openjdk, openjfx, and passing the path of my openjdk installation as requested by SQL Developer, loading the postgresql JDBC driver, and attempting to connect to the database, I get this error:
Status : Failure -SSL error: java.security.cert.CertificateException: Certificates do not conform to algorithm constraints
I'm kind of at a loss as to how to get around this. I'm not a java developer and I don't really know how to correct this. After much Googling for similar errors the the best solution I could come up with was to add the following to /opt/sqldeveloper/sqldeveloper/bin/sqldeveloper.conf, which did not fix the problem or change the error:
AddVMOption -Djdk.certpath.disabledAlgorithms=MD2
I suspect this is still the right direction, but I don't know what should go in place of MD2, or if this is really even the correct solution.
Running openssl s_client -connect 192.168.122.63:5432 returns the following:
[user@hostname ~]$ openssl s_client -connect 192.168.122.63:5432
CONNECTED(00000003)
write:errno=0
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 303 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
How do I get around this?
Would be helpful to share the certificate here. Knowing how the cert is built may shine a light on this. Especially of use would be: signature algorithm but if you dump the whole thing that might save some back and forth here. – Ram – 2019-12-28T22:59:39.733
@Ram I wouldn't know where to look to even find it. That goes a little beyond my normal work - is there some standard place I would find it, or is it totally dependent on whoever built it in the first place? – Kefka – 2019-12-30T16:03:59.210
openssl s_client -connect host:portwill print out the certs. Find the BEGIN and END CERTIFICATE stuff and copy and paste the cert into a file.crt. Then runopenssl x509 -in file.crt -text -nooutand you will see the thing parsed out into something a bit more readable. Add the output to your question so we can hopefully see what's up. – Ram – 2019-12-30T18:57:49.270@Ram Sorry for the delay. I've added the requested output, which seems to show no certificates at all, assuming I ran the command correctly. 192.168.122.63 being the ip of the db vm, and 5432 being the port the database is listening on. – Kefka – 2019-12-31T17:04:52.470