39
4
My website keeps getting hit by odd requests with the following user-agent string:
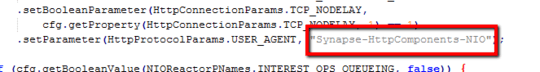
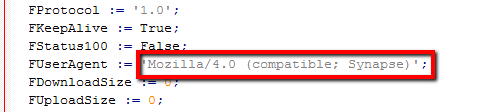
Mozilla/4.0 (compatible; Synapse)
Using our friendly tool Google I was able to determine this is the hallmark calling-card of our friendly neighborhood Apache Synapse. A 'Lightweight ESB (Enterprise Service Bus)'.
Now, based on this information I was able to gather, I still have no clue what this tool is used for. All I can tell is that is has something to do with Web-Services, and supports a variety of protocols. The Info page only leads me to conclude it has something to do with proxies, and web-services.
The problem I've run into is that while normally I wouldn't care, we're getting hit quite a bit by Russian IPs (not that russian's are bad, but our site is pretty regionally specific), and when they do they're shoving wierd (not xss/malicious at least not yet) values into our query string parameters.
Things like &PageNum=-1 or &Brand=25/5/2010 9:04:52 PM.
Before I go ahead and block these ips/useragent from our site, I'd like some help understanding just what is going on.
Any help would be greatly appreciated :)
2
An enterprising user over here (http://goo.gl/baHJn) took a look at the source for Apache Synapse. The UA header it uses doesn't match what your logs show. Further digging on his part turned up Ararat Synapse which DOES use that header.
– Doug Wilson – 2013-03-12T14:35:13.717See related question and commentary on this other stackexchange site, http://security.stackexchange.com/questions/18652/is-this-a-viewstate-attack
– Funka – 2013-04-18T19:02:56.773Whenever I google on this user agent, I come across this post so thought I should share some of my findings in case someone is looking for it. http://www.btpro.net/blog/2013/05/black-revolution-botnet-trojan/ This a mostly a botnet attack and has nothing (or very little) to do with Apache Synapse project.
– Imran Saeed – 2013-09-19T10:06:01.710