0
We have a webapp that uses 'Let's encrypt' certificates (and the nginx webserver).
The certificates are automatically renewed (a cron job runs every day and we get a new cert every 2 or 3 months).
With the first certificate everything worked. But now, that we got a renewed certificate, the Edge browser seems to have a problem.
When we visit the site, it seems that Edge does not recognize/use TLS encryption:
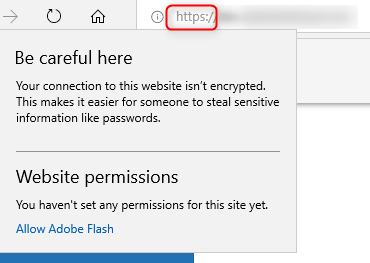
you can see that the URL is https (so I guess the connection is actually encrypted), but the info window (when you click the (i) icon) shows a message, that the connection is not encrypted.
When we press F5 to relaod the page, everything seems okay again:
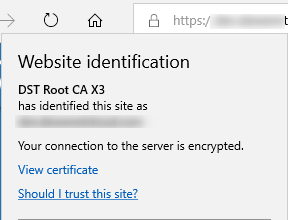
So I guess, that Edge may somehow still have the info about the old (expired) cert and thus shows the wrong info message.
note:
we do have HSTS enabled in the NGINX config - but that should not matter: SO-Ref
How can we avoid this? i.e. we want Edge to automatically use the new cert and not force our users to press F5.
How do other browsers behave? – garethTheRed – 2019-06-13T10:12:15.153
@garethTheRed I am not sure how other browsers behave, because it is tricky to reproduce. After you click F5 once, the issue is gone. However, I think that I did not see the issue in Firefox. In Chrome I also saw a strange issue: it showed the okay-lock icon in the address bar, but the cert detail page showed the expired cert. Also after F5 the issue was gone. – TmTron – 2019-06-13T10:20:28.290
It's going to take a very long time to figure it out if you can only test once every three months. You could look at SChannel's ClientCacheTime - 10 hours by default. It might also be worth creating a lab CA (OpenSSL maybe) with certs that last much shorter in order to speed up the process. – garethTheRed – 2019-06-13T10:38:16.223