You seem to be correct in your suspicions: according to the error message, your proxy certificate uses a SHA-1 signature algorithm, which has a serious known weakness. The validity time is not the issue; the bad algorithm is.
The process to deprecate the SHA-1 algorithm started years ago: with Chrome it started in 2014, as it started to flag end-entity certificates that were using SHA-1 and were valid past January 1, 2017 as "secure, but with minor errors". As time passed and new ways to exploit the weakness were discovered, the flagging was extended in steps to all SHA-1 non-root certificates and made more strict: by now, any up-to-date web browser will mark a site with a SHA-1 certificate anywhere in its certificate chain as unequivocally bad.
Certification authorities compliant with CAB/F baseline requirements stopped issuing any new SHA-1 certificates at the start of year 2016.
Microsoft also went through the process to deprecate SHA-1 certificates in 2017.
If your firewall/proxy still uses a certificate with a SHA-1 signing algorithm, it looks like you've been sort of asleep at the wheel for a while. It became apparent only now probably because of some recent security patch that finally made the SHA-1 algorithm as categorically distrusted everywhere.
You should make sure your proxy can use certificates with better algorithms (if it is up to date and can handle modern TLS on websites, it probably already can), and create a new SSL proxy default authority certificate that uses SHA256 instead of SHA-1. You'll need to distribute it to all the clients whose SSL/TLS traffic you wish to monitor. Once distributed, you can switch your proxy to use the new certificate.
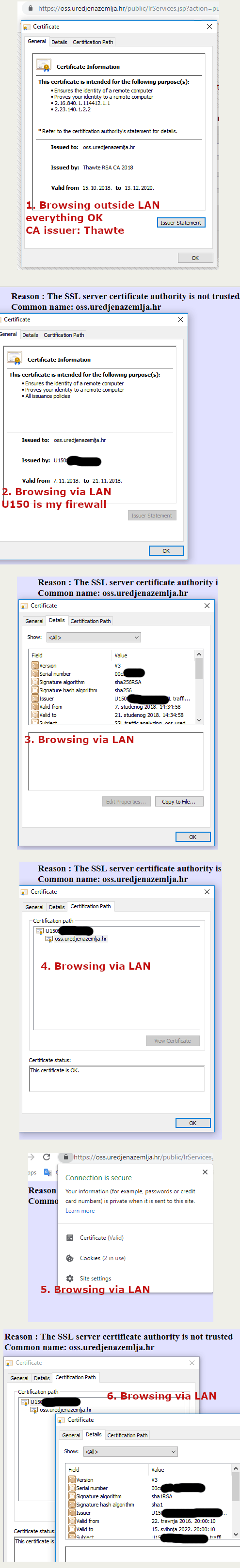
With the screenshots added, it look like the browser actually is mostly happy with the certificate it is getting, as there is a good padlock icon in the address bar. The actual error message is shown instead of the page content, which makes me think this is the proxy's way of telling about a certificate validation failure on the connection between the proxy and the target site.
In the first screenshot, you're browsing outside the LAN and the actual certificate of the site can be seen. Note that it's been renewed recently, as its validity time started on 15.10.2018. The CA certificate used to certify the site is "Thawte RSA CA 2018", so even the CA certificate is at most one year old.
You might actually have a combination of two problems:
- the browser was unhappy about the proxy's certificate with the deprecated SHA-1 algorithm, but for the time being, it still considers that a forgivable thing.
- and the proxy was unhappy because it does not have either the "Thawte RSA CA 2018" intermediate certificate or its parent, the "DigiCert Global Root CA" certificate in its own store of trusted CA certificates, and so it cannot verify the site's recently-updated actual certificate.
At the time of this writing, the relevant Thawte CA & intermediate certificates seem to be available here.
Its a problem the server owner must fix. They may not even be aware of the problem though. Especially government services sites usually have to hear it from their clients first that there is a problem before they attempt to fix it, then after they hear it, it will take some time before things get fixed. – LPChip – 2018-11-14T10:54:40.433
One way to be absolutely sure its not on your end: try with different browsers and try with different devices (pc, laptop, smartphone, etc) – LPChip – 2018-11-14T10:56:15.813
From my LAN, over my firewall it doesn't work with different devices. It works from outside of my LAN, if I go with my phone with my mobile internet provider connection. – Hrvoje T – 2018-11-14T11:01:54.770
What if you use your phone using your Wifi? Does it then work? Mobile browsers are different than pc browsers and possibly are less secure. In order to make sure you experience the same, test using the Chrome app on your phone and Chome desktop version on your pc. I estimate that both will fail the site regardless on what network you are. – LPChip – 2018-11-14T11:28:17.377
Using my WiFi over phone also fails to load a site. It's Android 8 with lastest Chrome. – Hrvoje T – 2018-11-14T11:31:35.337
So... if your phone using WiFi does not load the site in Chrome, but going to mobile carrier does work on Chrome, then the problem is on your end. Please edit your post to include this information, its crucial, because it invalidates the answer. – LPChip – 2018-11-14T11:43:25.700
Ok, but I said I have the firewall with proxy certificate. – Hrvoje T – 2018-11-14T11:50:45.487