1
Please, help me figure out which implementation path to take for the following task:
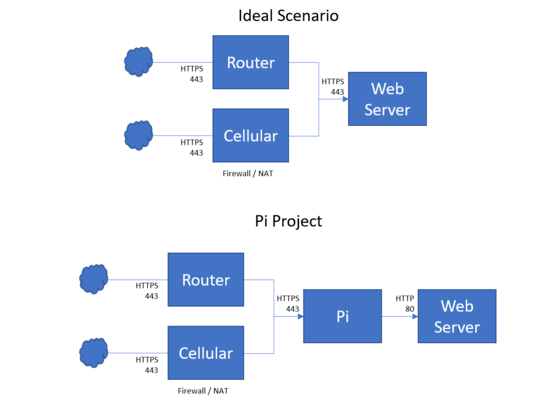
I have a blackbox device that acts as a webserver (I can connect to it locally by typing its IP address in the browser's address field.) The box does not implement any security measures except simple user name and a password. This is certainly fine when this server is on an isolated network, but I wish to have the access to it from the internet - that is from anywhere in the world. With this, I wish to use TLS security for data encryption.
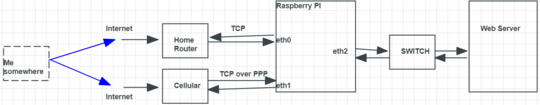
Having a Rasbperry PI available (and openVPN software), I thought it would fit this application. There are many different tutorials on how to implement VPN, bridge, router and firewall using Raspberry PI, but I can not figure out which one out of the four functionalities is suitable for my application. The conceptual diagram is shown below:
The Raspberry Pi will have two network interfaces for internet access: one through ground ethernet (eth0), the other - using cellular internet (eth1) - which ever is available favoring the ground internet connection. The IP addresses for both interfaces will be known. The third ethernet interface (eth2) will be connected to the local network through the switch. The server will be also connected to the switch. I have no control over the server (it's a black box) - I only know its IP address.
The idea is to have Raspberry PI to act as a middleman between me and the server, so I could securely connect to its web application using my web browser. But which functionality Raspberry Pi must implement: a VPN, router, bridge or firewall?
EDIT:
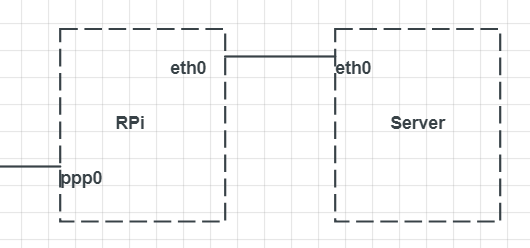
The task that I stated above was too steep for me (lack of competence) and I decided to simplify the setup to start with. I did not want to remove the top part of the question just in case someone will find it and its corresponding answers useful. Instead, my new (simplified) setup would look as follows:
The RP would be connected to the cellular internet through the ppp0 interface and route all traffic to eth0 interface which would be directly connected to the server:
1. dynamic ppp0 IP address (given by cell service provider)
2. static eth0 IP address (assigned by me)
3. non-secure internet connection
4. RP is connected to the server directly (no switch needed)
I found several solutions like this and this, but they do not clearly explain why things are done that way. They also provide command line directives which I will not know how to undo. Instead, I wish someone would reference the actual system/config files which I could edit and revert if needed.
Currently, when I connect RPi to the webserver, I can browse it from the web browser. The goal is to be able to access the webserver from the internet through RPi. Could someone provide an educational tutorial on how to properly setup routing, taking into consideration that ppp0 interface would go UP and DOWN depending on the cellular connectivity as well as its IP address would be different and unknown every time.
What's the use-case? How do you see yourself connecting remotely to the web server? What's the "cellular" device? What are its capabilities? – Robear – 2018-06-09T00:36:48.440