90
25
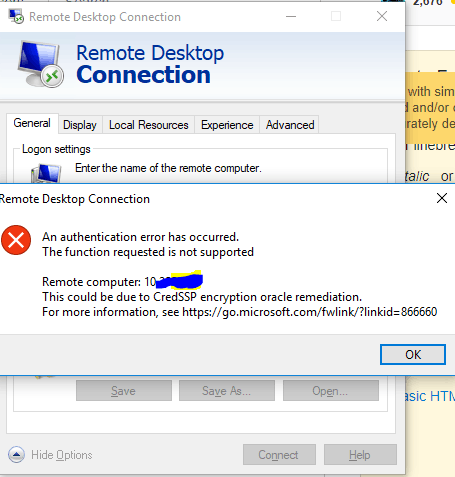
After Windows Update, I get this error when trying to connect to a server using Remote Desktop Connection.
When read the link provided by error message, it seems because of an update at 2018/05/08:
May 8, 2018
An update to change the default setting from Vulnerable to Mitigated.
Related Microsoft Knowledge Base numbers are listed in CVE-2018-0886.
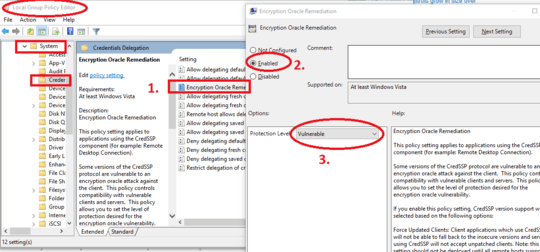
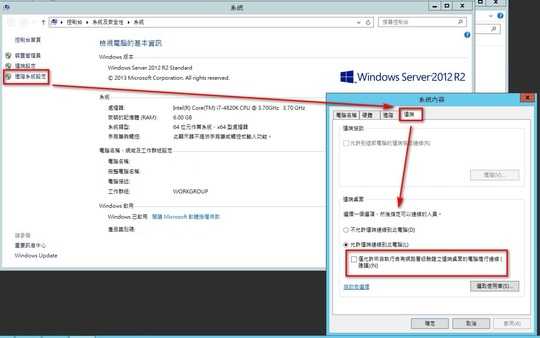
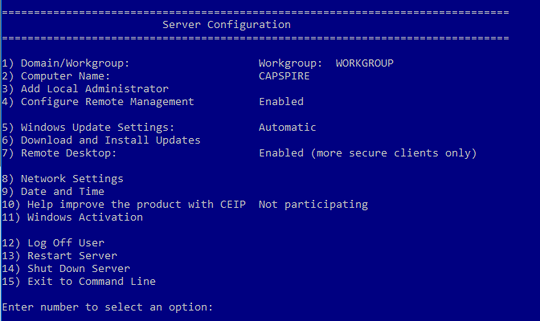
Is there a solution for this?
1(Meta: updates go at the end of posts, to ensure they are still understandable for new readers, and answers go in the answer space, not merged into questions. Thanks). – halfer – 2018-05-10T09:46:24.917