134
24
When I visit https://1.1.1.1, any web browser I use considers the URL to be secure.
This is what Google Chrome shows:
Normally, when I try to visit an HTTPS site via its IP address, I get a security warning like this:
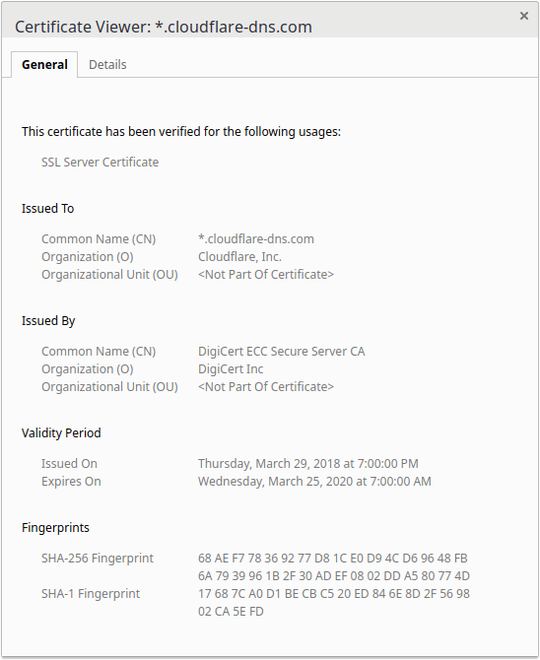
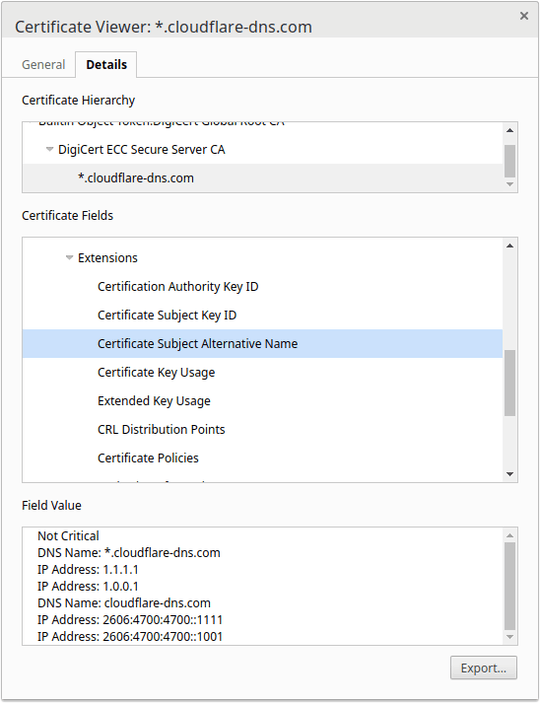
From my understanding, the site certificate needs to match the domain, but the Google Chrome Certificate Viewer does not show 1.1.1.1:
GoDaddy's knowledgebase article "Can I request a certificate for an intranet name or IP address?" says:
No - we no longer accept certificate requests for either intranet names or IP addresses. This is an industry-wide standard, not one specific to GoDaddy.
(emphasis mine)
And also:
As a result, effective October 1, 2016, Certification Authorities (CAs) must revoke SSL certificates that use intranet names or IP addresses.
(emphasis mine)
And:
Instead of securing IP addresses and intranet names, you should reconfigure servers to use Fully Qualified Domain Names (FQDNs), such as www.coolexample.com.
(emphasis mine)
It's well after the mandatory revocation date 01 October 2016, yet the certificate for 1.1.1.1 was issued on 29 March 2018 (shown in the screenshot above).
How is it possible that all the major browsers think that https://1.1.1.1 is a trusted HTTPS website?
10Worth pointing out there is a huge difference between 192.168.0.2 and 1.1.1.1. One
192.168.0.2doesn't exist outside of your intranet. If you created your own self-signed certificate192.168.0.2would be trusted, and you could use the same approach for the SAN, on a domain likefake.domain. Worth pointing out that1.1.1.1isn't a reserved IP address, so it appears, any CA would have issued the certificate. – Ramhound – 2018-04-12T04:54:30.62312https://blog.cloudflare.com/announcing-1111/ "We're excited today to take another step toward that mission with the launch of 1.1.1.1 — the Internet's fastest, privacy-first consumer DNS service. " – None – 2018-04-12T06:14:20.633
11I think you bracketet the sentence wrong. They probably meant 'must revoke SSL certificates that use intranet (names or IP addresses)' not ''must revoke SSL certificates that use (intranet names) or IP addresses'. – Maciej Piechotka – 2018-04-12T07:47:19.800
1@MaciejPiechotka is correct, this means "must revoke SSL certificates that use intranet names or intranet IP addresses" – Ben – 2018-04-12T11:53:43.080
1@MaciejPiechotka: The article also has a sentence beginning with “Instead of securing IP addresses and intranet names,” which can only be bracketed as “Instead of securing (IP addresses) and (intranet names).” – Deltik – 2018-04-12T12:52:42.580
1
This was covered in a recent episode of podcast Security Now by Steve Gibson, episode 557. Transcript. MP3 file
– Peter Mortensen – 2018-04-12T18:00:34.7301@Deltik "Instead of securing cats and dogs and other domestic pets". Does this imply that cats and dogs are not domestic? Even if you cannot "bracket" it in that way, semantically you still can. Natural language is incredibly ambiguous sometimes. – Bakuriu – 2018-04-13T20:10:56.533
2BTW...there's no such thing as a mandatory revocation. Literally no organization on Earth has that kind of power. The closest you get is a bunch of CAs agreeing to do a thing. – cHao – 2018-04-13T21:39:04.240
You're confusing yourself and others by claiming that
– Vlastimil Ovčáčík – 2018-04-18T13:42:45.880the certificate for 1.1.1.1 was issued. Clearly not true as the certificate is issued to*.cloudflare-dns.comand not an IP address. The only thing left to answer is whether the browser is performing reverse DNS lookup (1dot1dot1dot1.cloudflare-dns.com) or is it reading the IP from Subject Alternative Name in the certificate.@curiousguy that would be wrong conclusion drawn from what I said, especially because I literally state that the IP address is listed in certificate's SAN. – Vlastimil Ovčáčík – 2018-06-23T08:37:19.823
@VlastimilOvčáčík OK I was confused by the phrase "not true as the certificate is issued to *.cloudflare-dns.com and not an IP address". I read that as saying "the certificate is not issued to 1.1.1.1". I'm still NOT sure what that means. – curiousguy – 2018-06-23T08:54:36.627