2
I want to use my router (A TP-Link WDR3600) running LEDE 17.01.4 as an SFTP server to store my backups created with borg. I already know how to perform backups and set up a USB drive, what I don't know is how to proper setup the SFTP server part for security and maintainability, like:
- Do I have to create a dedicated user?
- If so, how to restrict permissions to that backup user, so that it can't peek into sensitive files in the filesystem?
I am basically looking for the best practices to run a sane SFTP server, but using the limited environment of an embedded system.
If possible, I'd prefer not to use openssh since it's not integrated within the UCI system.
My question might be too wide, please let me know if that's the case.
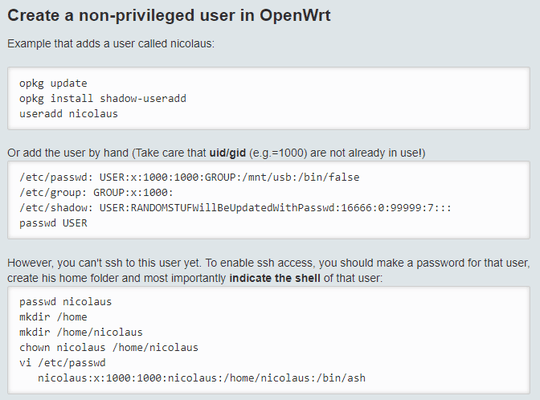
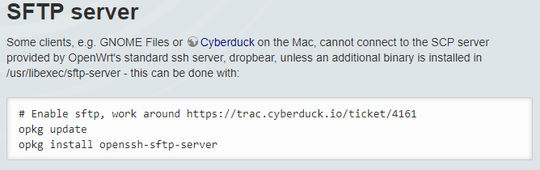
FYI, Borg backup documentation link "BorgBackup (short: Borg) is a deduplicating backup program. Optionally, it supports compression and authenticated encryption." (after searching it thought I'd might as well post it)
– Xen2050 – 2018-03-19T00:58:06.180To be honest, I discovered
borghas to be installed in the remote host to; that's not possible with OpenWrt. I'll to something likerestic. – LivingSilver94 – 2018-03-19T20:57:44.550I remember seeing a link about compiling Borg for OpenWRT, I'm not sure if it was successful but I assumed that's what you were doing. The docs say it doesn't have to be installed on the remote host, just needs ssh, but performance will suffer if it's not installed – Xen2050 – 2018-03-20T14:36:12.453