2
I'm currently doing some tests with Active Directory Domain Services using a DC (Windows Server 2016) and two clients (both W10) all running on Hyper-V (internal network).
To what I have understood so far, when selecting "Connect" on a VM in Hyper-V, it uses RDP protocol to connect the user to the VM.
Starting on that, I had to create an OU containing both W10 clients, and creating a GPO allowing everyone to connect to these computers through RDP.
I have allowed "Everyone" under the policy :
Computer Configuration/Policies/Windows Settings/Security Settings/Local Policies/User rights assignment/Allow log on through Remote Desktop Services
This is the behavior encountered after applying the policies
- An authorized user attempts to log in
- An error message appears "The requested session access is denied"
- The computer automatically reboots after clicking OK
- The exact same user re-tries to log in
- He successfully access to his session
This occurs every time the VM is restarted.
My question is : is there something I can do to bypass this error screen before a user logs in ?
I'm not real clear on what you are experiencing. When using Hyper-V you connect to a VM and you are presented with a standard windows login screen. Please describe exactly, step by step what you are doing and seeing. 1) when are you trying to login? Do you see the standard windows login screen first? 2) after typing in the username/password on this standard login screen? 3) what computer reboots? The Host? The Guest? If this happens every time the VM is restarted, then how do you ever login, because according to you the computer reboots at step 3 which would put you back at step 1. – Appleoddity – 2017-12-19T04:42:13.073
The exact steps are described in my post. 1) The normal login screen is prompted,the credentials are entered. 2) An error message appears (the requested session is denied). 3) The computer reboots after clicking OK. 4) The user logs in 5) The access is granted – Arthur Attout – 2017-12-19T15:09:31.717
Just to confirm, which version of Windows 10 are these running? Home? Pro? Enterprise? Were they upgraded at any point? – Appleoddity – 2017-12-19T17:19:37.923
Make sure the user you are trying to login with is a member of the "Remote Desktop Users" group on each Win 10 machine. Confirm that there are no errors in the event log during startup that would be impacting communication with the domain controller. – Appleoddity – 2017-12-19T17:22:26.033
Both local policies on client computers allow "Everyone" to open a session using Remote Desktop, so I think this is enough for the first part. For the log error, I ran several trials that unfortunately did not show any error during login startup .. – Arthur Attout – 2017-12-19T20:56:24.200
No. It’s not enough. It is a requirement they be in the Remote Desktop users group. https://support.microsoft.com/en-us/help/954369/error-message-when-you-use-remote-desktop-connection-to-connect-to-a-w
– Appleoddity – 2017-12-19T21:00:13.4901After adding the desired group in Remote Desktop users group, running GPupdate and rebooting clients, the issue still remains – Arthur Attout – 2017-12-19T21:19:57.977
1) How have you confirmed that the VM is rebooting after the first/failed logon attempt? Is event 6006 logged in the System log, confirming the computer actually shut down? 2) To which VMs are you trying to logon from the Hyper-V host? The DC VM? The Windows 10 client VMs? Do the user(s) you're using to logon the DC have Administrative rights (because by default only Admins can logon a DC) 3) Does removing the changes you made to the Local Security Policy resolve the problem? – I say Reinstate Monica – 2017-12-21T16:59:22.820
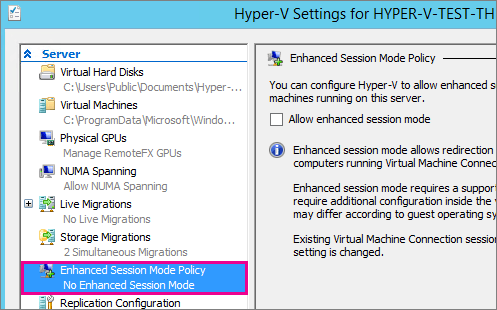
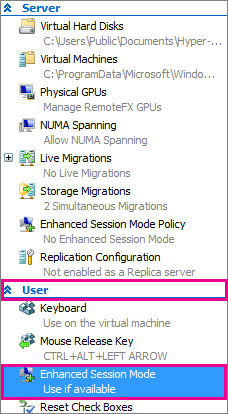
14) What version of Windows is the Hyper-V Host running? 5) What happens if you disable enhanced session mode on the host and VM? (Please be sure to [edit] your question with the responses to commenter's questions, then ping them to let them know you've updated it.) – I say Reinstate Monica – 2017-12-21T17:03:57.107
The issue disappeared after I unchecked the enhanced session mode. If you post it as an answer, I will accept it – Arthur Attout – 2017-12-21T18:58:00.360