As it turns out, this was related to Internet Connection Sharing (ICS).
In the following, I'd like to describe how I got to this conclusion in hope it helps other people with similar problems.
The first step is to identify the service causing trouble. While Windows' own Task Manager has also learned to do this recently, I used Process Hacker which can also edit a service's configuration.
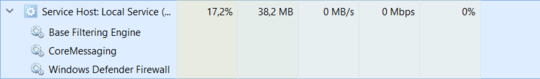
Double-clicking the offending svchost.exe instance and selecting the Service tab shows which services are running inside that process:
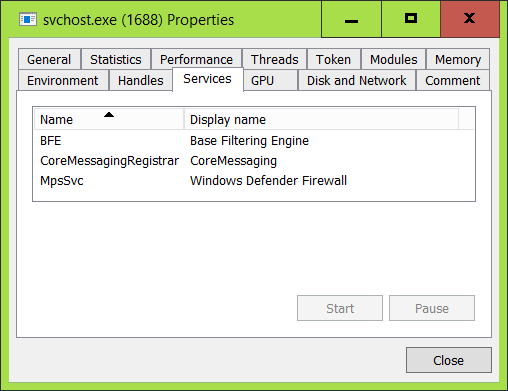
svchost.exe can host many Windows services at the same time, making it hard to identify which service is causing trouble. While recent versions of Windows 10 typically isolate services when enough RAM is available, some services still share a process.
This is such a case, and the easiest way to identify which service is causing problems is to separate them.
Process Hacker can do this. In its main windows' Service tab, we can configure whether a service can share a process:
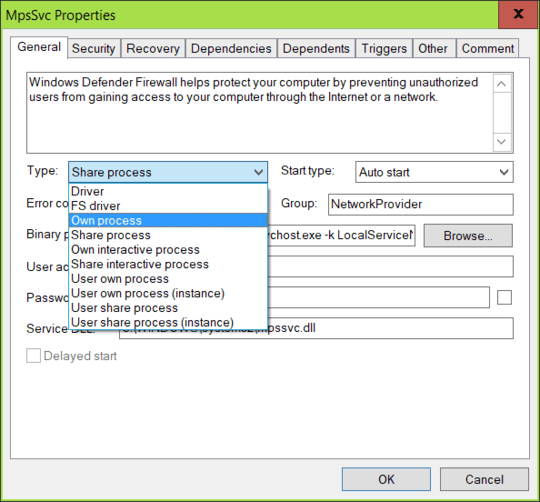
At least two of the three suspect services need to be configured as Own Process to make sure they are separated in the future.
Apparently, Windows Defender doesn't like users meddling with its service's configuration, so to successfully change this setting, I needed to
- grant the Administrators group Full Access on that service,
- disable the service,
- reboot so the service is stopped (it cannot be stopped separately),
- change the service type to Own Process and re-enable the service (set it to Auto Start) and
- reboot one last time to apply these changes.
After that, the offending svchost.exe only hosts a single service, so we do have a suspect:
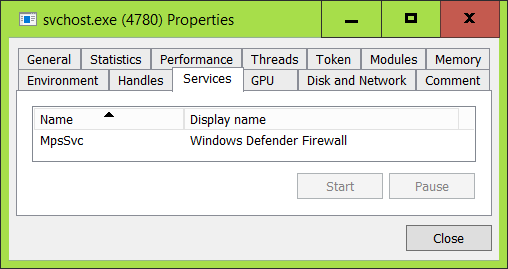
To analyse what's going inside the firewall service, we'll use the Windows Performance Recorder and Windows Performance Analyzer tool, part of the Windows ADK.
We'll begin by recording some data. While the suspect svchost.exe is chucking along in the background, download this file, add it as a profile, set up Windows Performance Recorder like this and start a recording:
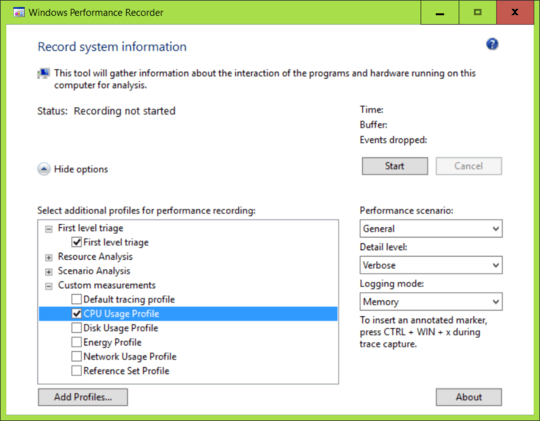
Let the recording run for 30 seconds or so, then save the recording. After saving, click Open in WPA to immediately open it for analysis.
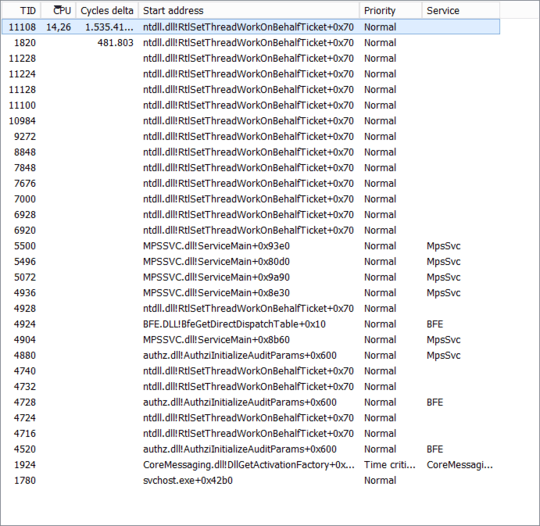
This is where things start to become tricky. In my case, I needed a hint from @magicandre1981 to look in the right place, under System Activity → Generic Events. There, the number of RPC events looked suspiciously high:
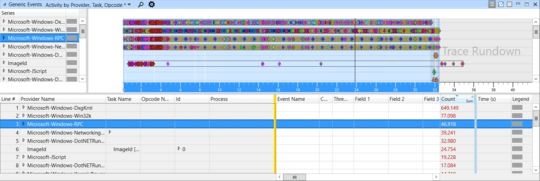
Drilling down, the Windows Defender Firewall's svchost.exe was showing up a lot on the Server side of win:Start and win:Stop events:
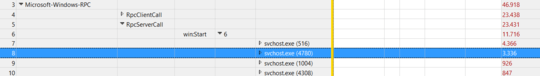
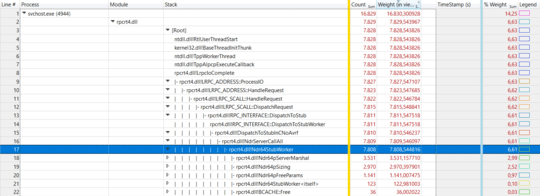
The next step was finding out who sent these RPC calls. By looking in the client side, another svchost.exe instance was looking suspicious:
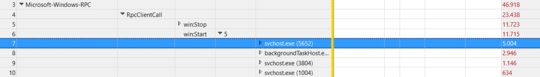
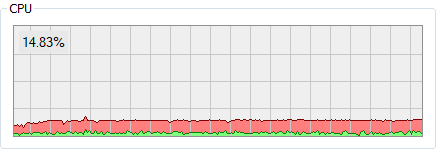
Indeed, Process Hacker couldn't detect a service running inside that process, which also was consistently causing CPU load:
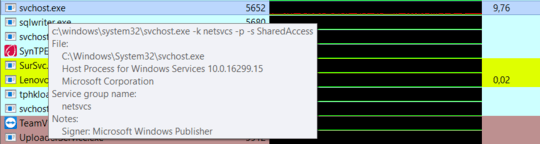
In this case, Windows' Task Manager succeeded in identifying the service:

Indeed, the service was stuck in the Starting state. I've disabled it since I don't need it, and CPU load has returned to normal after the next reboot.
I'd like to express my gratitude towards @HelpingHand and @magicandre1981 whose help in the comments made this possible.
As was later discovered in the TenForums post, resetting Windows Defender Firewall fixes this issue.










1If you run the following 2 commands in an admin prompt and restart; if any, which svchost process is causing the high CPU then:
Sc config BFE type= ownthenSc config MpsSvc type= own– HelpingHand – 2017-10-19T18:56:40.090Running any of these commands returns
[SC] OpenService FAILED 5: Access is denied., despite running in an administrative command prompt. – fefrei – 2017-10-19T19:43:42.0901As you have Process Hacker already, if you find the svchost process that is hosting BFE for example. If you double click on service name in the services tab, then view the security tab, I would have thought Administrators would have modify configuration rights. The above works for me. – HelpingHand – 2017-10-19T20:11:23.760
Interestingly, I able to grant Administrators the rights to modify the service configurations (I thought these were protected services that didn't allow that). After a reboot, the guilty party stood out:
– fefrei – 2017-10-19T20:22:23.793MpsSvc, a.k.a. the Windows Defender Firewall. One step closer, thank you!1Maybe you can now run Process Monitor with it filtered to that PID. See what shows up. – HelpingHand – 2017-10-19T20:50:35.113
That also worked out, and looked pretty repetitive. I've edited the results into my question. – fefrei – 2017-10-19T21:09:17.947
1
It does on my computer as well. TBH, I think your best bet is to install the Windows Performance Toolkit tools - https://docs.microsoft.com/en-us/windows-hardware/test/wpt/. Essentially you'll be using Windows Performance Recorder to capture a trace file and Windows Performance Analyzer to analyze it. https://channel9.msdn.com/Shows/Defrag-Tools has some good shows on these.
– HelpingHand – 2017-10-19T21:39:58.407@fefrei - Instead of including the resolution/answer into your question you should submit an answer. – Ramhound – 2017-10-19T22:21:21.323
@Ramhound This isn’t an answer, just some clues on the way to an answer. The process is still running and eating CPU time. I’ll try to clarify this. – fefrei – 2017-10-20T04:03:19.223
I realized that when the service is started manually, it doesn't start eating up CPU. As a workaround, I've not set the service to be started manually. It still starts automatically (probably because some other service starts it), but this way, it starts late enough not to cause problems. Weird! – fefrei – 2017-10-20T09:47:28.610
1
don't sort by module. remove this column. also trace the RPC events. download this file, run WPRUI.exe, click on add profile, select the downloaded WPRP, select CPU Usage Profile and Network Usage profile under Custom measurements. click on start and capture the usage for 30s. now look which PID has the high cpu usage and in generic events graph/table filter for the exe with the high usage and RPC events and look which rpc action are done
– magicandre1981 – 2017-10-20T14:13:33.0731
More discussion about this high CPU with FCU problem can be found here, https://www.tenforums.com/general-support/95844-fall-update-v-1709-creates-problems-cpu-usage-desktop-wallpaper-4.html.
– Adrian – 2017-10-20T16:26:45.853@Adrian: Thank you for this link! @magicandre1981: Thanks! If I interpret the output correctly,
MpsSvchas thousands ofMicrosoft-Windows-RPC/RpcServerCall/win:Startandwin:Stopevents. The client side of these requests is ansvchost.exeinstance hosting thenetsvcsservice group, according to Process Hacker. Task Manager identifies this as Internet Connection Sharing, which indeed consumes CPU power and is stuck in Starting (hadn't noticed that before). – fefrei – 2017-10-20T17:25:31.8031if you don't use Internet Sharing, set start type of ICS to "on demand" or disabled. – magicandre1981 – 2017-10-20T17:40:43.107
I set it to disabled. After a reboot, that had magically changed to
Manual (Trigger Start), but things did calm down. Hooray! While this isn't the root cause, your hints absolutely answered my question what the service was doing and led to a workaround that works for me. Would you mind posting your hints as an answer so I can accept them? – fefrei – 2017-10-20T17:45:37.5301you discovered 95% on your own. I only gave you a small hint. Post your own find as answer. – magicandre1981 – 2017-10-20T18:03:24.340