0
We have a small VPC with three subnets (WAN (public), LAN (private), DMZ (private)). I'm tasked with setting up a central firewall in the WAN subnet, that monitors all traffic both to the outside world as well as the traffic between subents.
My problem is monitoring the traffic between LAN and DMZ. I've associated each subnet with a routing table, directing all outbound traffic to the firewall and this works fine. Unfortunately, AWS prevents me from adding routes for the traffic between the subnets. Adding routing rules 'inside' the VMs would only partially solve the problem, since LAN contains appliances that don't allow this kind of configuration. Also I feel, this might cause more problems in the long run ... I think making WAN, LAN and DMZ each a VPC instead of a subnet might lead to a solution, but that seems to me a horrible misues of VPCs.
What's the canoical AWS solution to this problem?
Edit 1: I'm trying to set up the classic 'three zones plus central firewall' network. The firewall is supposed to monitor and secure the traffic between the subnets and the individual instances and also from the outside. This includes:
- Watch for unusual connecions and report them. (i.e. the wiki has no business to access the hornetq server and any such connection could indicate that the wiki VM has been compromised)
- Rate limit network traffic. (i.e. the database server is allowed to send reporting emails, but if it starts sending hundreds of emails per second, I'd like to get an alert)
- Detect DDOs.
- ... more security stuff ...
I'm not sure all of this can done with AWS native methods and the central firewall concept just feels more natural to me.
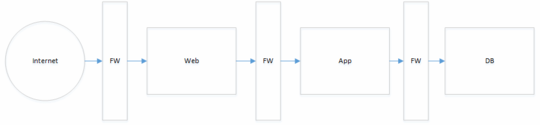
Edit 2: Crude and simplified diagram of the network setup
Network Security Groups and ACLs allow me to properly separate the subnets and control the connections between the instances. But I don't see the possibility to do advanced stuff (i.e. rate limiting, ...). My idea is to completely cut traffic between LAN/DMZ subnets and use a classic network configuration: Route all traffic over the firewall and let it decide what happens to it. Unfortunately the routing tables of a VPC don't allow me to route all traffic within the VPC (or a subnet thereof) to a central firewall. So the question is, how can I leverage AWS to get the traffic fom my subnets to my firewall, so it can do its thing.
What are you trying to achieve? Monitoring is a solution, but we don't know the problem you're trying to solve. – Tim – 2017-08-29T20:32:27.537
I've edited my post to address your questions. – briconaut – 2017-08-30T08:22:08.397
I think a diagram would explain this better. From what I can tell, which isn't much, you're trying to intercept traffic between two networks that you're not part of. I think you may need to think in terms of layers, rather than centralization. – Tim – 2017-08-30T09:09:05.170
Second edit to address your questions, including a simple diagram. – briconaut – 2017-08-30T09:53:44.633
If the wiki can access the hornetq server now, then you already have a problem. Security groups allow very granular access control, better in many ways than a separate firewall. Additionally, is impossible to forge, spoof, or sniff traffic from inside a compromised EC2 instance -- the network infrastructure is automatically smarter than that. Also, VPC traffic flow logs can identify unexpected traffic. VPC is not a LAN, and I would suggest that trying to treat it as one is an exercise in futility, and prone to introducing bottlenecks and single points of failure. – Michael - sqlbot – 2017-08-30T20:26:09.677
I'll have to check the traffic flow logs feature, it looks quite promising. – briconaut – 2017-09-01T08:04:22.473
I also agree with most of the rest of your assesment, but preventing an intrusion is just the first step. I'm tasked with making sure, that after that happens (not /if/ that happens), the rest of the VPC is protected as well as possible. But most likely, as you indicate, applying this 'classical' architecture to a VPC is simply the wrong aproach. In the end, selling a different design to management will be the real challenge. – briconaut – 2017-09-01T08:14:51.397