28
6
I have searched frequently for a way to do this and never found a good answer, though there have been tickets created in the past (#142818 & #405549).
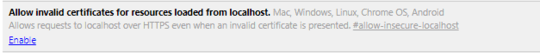
Apparently, the chromium devs have failed to create a chrome://flags override for "broken" SSL and/or password saving. This would seem to be the easiest way to fix this annoying "feature" (via flags). I DO understand completely why they block it by default.
Since there is no override to my knowledge, I had assumed that you would need to import the given self-signed certificate to a trusted root area in (Windows) store. This does not appear to work either.
Has anyone been able to get this to work? I can live with the warning - just not the lack of password saving. I spent most of my workday in a dev environment and need to keep re-entering passwords dozens of times a day (copy/paste).
Importing your self-signed cert into the Windows certificate store does work for Chrome, I do this all time. How are you importing it and into which store? – heavyd – 2017-08-15T16:08:38.800
Last attempt - Import self-signed .cer format into "Trusted Root Cert Auths./Certificates" – bshea – 2017-08-15T19:51:51.170
Not to state the obvious, but wouldn't be a bit easier if Chrome just added a flag override for us? Anyway, if you can point me in right direction or tell me what I am doing wrong please do :) – bshea – 2017-08-15T20:00:53.310
Importing your self-signed cert into the Windows certificate store does not work for me, too – Ivan – 2018-01-19T10:01:52.933
Update - I have never found an easy way/flag to do this as of date of this comment. But, with advent of free certificate issuance (LetsEncrypt/etc), my password saving problem's have been slowly going away as most times I can just create a legitimate SSL certificate. Problem solved. Note: The web server (during cert issuance) and client browser needs access to Internet, though. Which usually isn't an issue.. – bshea – 2020-02-03T15:27:41.563