4
1
I am trying to show only HTTP traffic in capture window in last version of Wireshark, but I cannot figure out what is the syntax in capture filter.
I have tried suggestions for old versions of Wireshark but with no success.
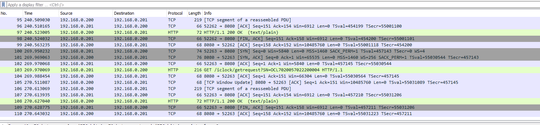
I have this current filter:
ip host 192.168.0.201
Meaning that I want to capture packets from and to that ip address. I need to add HTTP protocol condition. I have tried "ip host 192.168.0.201 http", "ip host 192.168.0.201 and ip.proto == 'http', and a lot of other combinations but none worked.
EDIT:
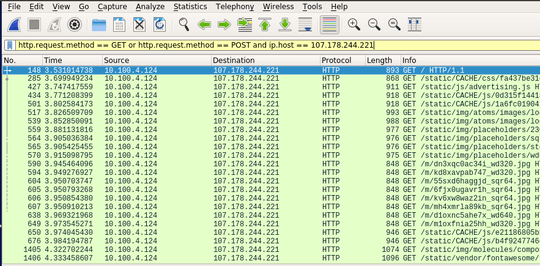
This is the actual capture session, so that you can figure out what the problem is:
Regards Jaime
Did you try entering the actual port number of HTTP (port 80) instead of 'http' – Kirill2485 – 2017-06-30T21:53:10.590
Port is 8080.... but I don't want to filter by port but by protocol... protocol http means methods Get or Post.. when I don't filter by protocol, I get entries with http and tcp protocols, both using sale port 8080. Since tcp entries are the most, I need to filter them. – jstuardo – 2017-06-30T22:29:17.347
If you just want to monitor GET and POST requests a website, the Chrome developer tools let you do that. Just press F12 and go to "Network" – Kirill2485 – 2017-07-01T00:28:29.833
No....you cannot suppose this is a PC. This is actually a device that sends requests to a website and receive responses from it. That traffic is what I need to monitor. That is the reason I need a tool such as Wireshark. – jstuardo – 2017-07-01T00:34:46.897