0
I have a new connection that has been working for 6 months at my SOHO. This connection is on 4G LTE at about 45M/12M. Before that I had a DSL with a fixed IP running at about 10M/1M but I want to stop this.
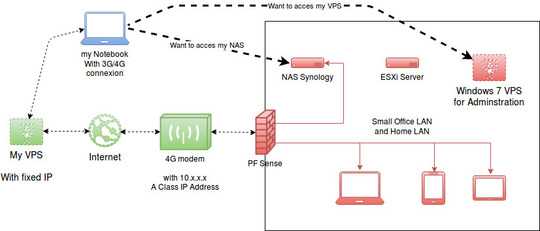
The problem is that my Provider is giving me an A class IP address 10.x.x.x on the 4G/LTE Modem, so the NAT on my firewall is not working anymore! I can't access my services (Mail, caldav, carddav, RDP, ...) when I'm outside my home and office.
I also have got a VPS in a data centre with a fixed IP. This VPS is a Ubuntu LTS based web server. Ports 80/443 and 25 needs to stay available for Apache and Exim.
I think the solution is maybe to make a connection between my VPS working as a "NAT VPN proxy"?
My idea is to create a port range on my VPS listening for example 30000 to 39999 and when we catch this range the VPS will redirect my traffic to my PFSense in a VPN tunnel. So, VPS would be the VPN server and PFsense is the VPN client permanently connected to the VPS.
Example of ports and corresponding services :
VPS port PFSense NAT LAN devices IP Description
30143 30143 -> 143 TCP 192.168.10.100 IMAP to Synology NAS
35000 35000 -> 5000 TCP 192.168.10.100 Web access to NAS
33389 33389 -> 3389 TCP 192.168.10.20 MS RDP to VPS
35060 35060 -> 5060 TCP 192.168.10.10 Asterisk Server
...
- What do you think ?
- Maybe I can make a PPPOE beetween my VPS and PFSense ?
- Or is it possible with OpenVPN ?
- Is existing another solution ?
This is not because "of a class A network", network classes have been replace by CIDR for ~20 years. It's because the ISP uses private addresses and carrier grade NAT. – Sven – 2017-05-05T08:25:46.603
Yes, I know that 4G networks are on private addresses ! I see this and that's the problem. Ok, my vocabulary is old :D ! Is my title better like this @Sven ? – Meloman – 2017-05-05T08:28:48.537