0
I'd like to serve the same website with different TLS certificate for different ranges of source IP addresses. For instance, on one block, I expect users to connect to browsers where a company's local CA is installed in the client's root trust store. On another block, there will be another group of users who don't have that local CA, so I'd like to present a self-signed cert or one signed by their company's CA. On yet another block will be a M2M connection where simple self-signed cert is all that's needed.
I've read about using ssl_multicert.config in Apache Traffic Server, or using Server Name Indication (SNI), but those all deal with the destination IP (server), not the source IP (client).
I know I could run Apache on a separate port for each certificate and then play with the REDIRECT jump target in iptables. I'm looking for a clean way to do this using just Apache (2.4) configuration options. Anyone know?
1
Related: https://serverfault.com/questions/296617/apache-virtual-host-based-on-source-ip
– Bob – 2017-03-02T22:50:09.987What you describe seems like it would be breaking the basic principles of https where a certificate which is signed by a trusted Root CA indicates that the connection being made is actually who they have the certificate to. There is a reason even load balancer work the way they do – Ramhound – 2017-03-02T23:23:01.653
@bob, very appropriate related question. Search as I tried, I could not find that one. Since I would not be changing docroots or anything, only specifying a different certificate, I may just need to put the SSLCertificateFile and SSLCertificateKeyFile directives within If, ElseIf, and Else blocks. If someone beats me to testing this and posts the answer if it works, they get the green checkmark! – petiepooo – 2017-03-02T23:23:33.970
With SNI turned on you can serve multiple domains from the same IP and the same port with different SSL certificates – Alex – 2017-03-02T23:26:25.837
@Ramhound, I would agree with you if we were talking about true CAs and internet IPs/FQDNs. In my case, I'm talking about internal networks with invalid FQDNs on a host that has more than one interface with different RFC1918 IPs. My company's internal CA has no validity within the other network, and vice versa. And the M2M clients have neither of those local root CAs installed. – petiepooo – 2017-03-02T23:31:16.350
Sorry @Alex. I've clarified the question to show that I'm serving the same website to all; just with different certs for the different source IPs. SNI differentiates on the server's FQDN (or destination IP), not the source IP. – petiepooo – 2017-03-02T23:34:44.643
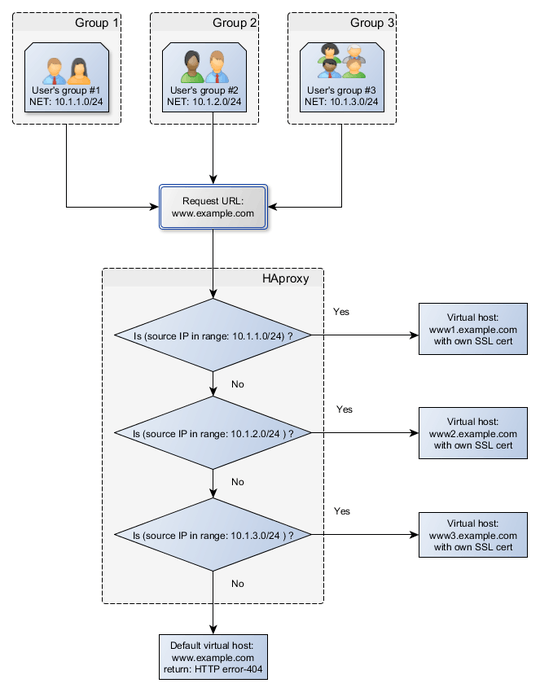
Oh, I see... May be setup the same site in multiple virtual hosts but with different subdomains as www1, www2... for different user's groups and manage routing to www1, www2 by incoming IP via
HAproxy. This way you can setup different SSL certificates on www1, www2 ... – Alex – 2017-03-02T23:42:25.617^^ This is how you achieve what you describe. – Ramhound – 2017-03-02T23:50:11.410
FWIW, the <If> clause cannot contain an SSLCertificateFile directive. I get AH00526 Syntax error and the message "SSLCertificateFile not allowed here" when I try. – petiepooo – 2017-03-03T21:40:50.873
@alex, if you want to write up the vhosts and HAproxy solution as an answer rather than a comment, I'll tag it as the answer. I think that's a cleaner solution than using different ports and messing with iptables, even though it involves another app on the front end.. – petiepooo – 2017-03-03T21:43:28.963
@petiepooo Moved it to the answer, may be some1 else will find it useful too – Alex – 2017-03-05T02:57:38.700