7
2
Intro
I recently noticed some services that had odd values appended to the service name when tidying up my PC. In the output from sc query they look like this:
SERVICE_NAME: CDPUserSvc_40b5c
DISPLAY_NAME: CDPUserSvc_40b5c
TYPE : e0 USER_SHARE_PROCESS INSTANCE
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
[snip]...
SERVICE_NAME: UserDataSvc_40b5c
DISPLAY_NAME: User Data Access_40b5c
TYPE : e0 USER_SHARE_PROCESS INSTANCE
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_PRESHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
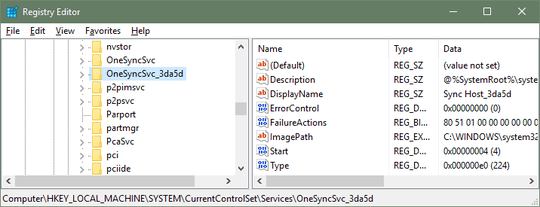
Regedit Output as images:
Ideas/Actions
My first thought was that I possibly had a virus/malware infection and there was something trying to impersonate a legitimate service with bad tradecraft. I believe I have ruled this out as the services are almost exactly the same as their legitimate non-hex appended counterparts. (see regedit output)
Some of the services have an invalid description, but identical code for creating the description in regedit. Additionally, I have issued sc delete <svcname> successfully. However, they are recreated upon reboot.
Questions
What are these services and why are they named like this?
How do I remove them?


They appear to be quite new to Windows and used for Connected Devices Platform https://msdn.microsoft.com/en-us/library/mt766144.aspx. See: http://superuser.com/questions/1115769/what-is-the-cdpusersvc-service/1118109
– HelpingHand – 2017-02-26T01:37:01.613