2
In Windows 10, if a user on a standard account attempts to perform a task that requires administrative privileges, they are asked to type in a password of an administrative account, on behalf of which they may perform this task, provided they type in the password correctly.
Is there any way to prevent this behavior, that is, to prohibit standard users from performing administrative tasks and prevent them from being asked for an administrative password? So that they cannot perform administrative tasks no matter what, as long as they're logged into a standard account?
In Linux, I can prohibit others from using
su, so I doubt I'd be unable to do sth similar in Windows... – gaazkam – 2016-12-05T02:44:14.9903Your regular users shouldn't know the admin passwords. – Journeyman Geek – 2016-12-05T03:17:05.297
@JourneymanGeek You are right of course, but despite that I still think in my special case this what I want to do is justified :) – gaazkam – 2016-12-05T03:37:57.973
There may be some sort of a shell tweak that hides the "Run as administrator" option – timotree – 2016-12-05T04:00:52.787
@timotree Won't help much :( Merely launching many apps (like System COnfiguration) or clicking many options in Control Panel tend to trigger this prompt for admin passwd, not only clicking on Run as administrator – gaazkam – 2016-12-05T04:07:46.510
I would definitely agree with @JourneymanGeek . This is much more of a personnel management or HR issue than it is a Systems Administrator problem. We are always glad to help whenever possible, but the real solution to this problem involves changing the admin passwords and letting standard users know that inappropriate behavior on the Windows systems won't be tolerated. The end-users wouldn't be happy with a Windows 10 machine configured to use kiosk mode.
– Run5k – 2016-12-05T05:46:38.7231
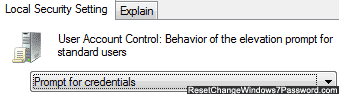
It's possible on Windows 7 using secpol, see Hide User Account Control prompts for non-administrative users. This will Automatically deny elevation requests. I don't have a copy of Windows 10 to see if this works there as well.
– DavidPostill – 2016-12-05T22:32:14.313@DavidPostill , I just double-checked and that group policy is available on a Windows 10 Pro machine, also. – Run5k – 2016-12-06T13:57:16.743
@Run5k Thanks. I will add this as an answer. – DavidPostill – 2016-12-06T14:18:03.823