1
There is an DBF-based accounting system (1C:Enterprise 7.7 with 1S-Rarus:MBTSS 2.5 configuration) running under limited user account. And this user has access to some other apps (LibreOffice for example).
Database of that accounting system is not in user profile, but only that user and administrators have access to one.
Unfortunately, some users mess up the system by accidentally accessing the files directly (for example, they find it using search). I'm wondering, maybe there is a method to limit "manual" user access to the folder at all?
What I'm thinking about is per-process permissions, which will only allow write access to the folder of accounting system for specific process, and won't let user mess it up. Something like in iOS, where only specific app can access its own files, but just for a single folder/process. I don't mind if the user still have read access to contents of that folder.
P.S. There is one method applicable for my specific case – using SQL database engine. But I'll need another version of that 1C:Enterprise for that, and price difference is just invidious.
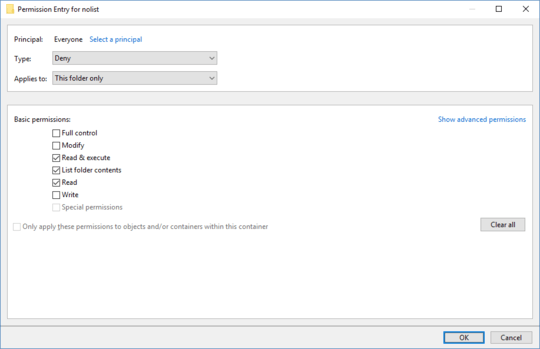
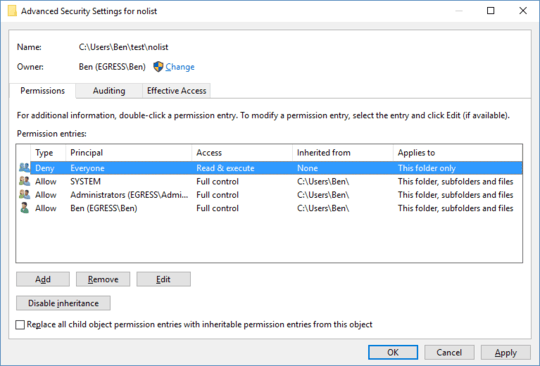
Hi. Thanks for answer, I upvoted because it may be useful for others, but unfortunately denying folder listing breaks the application (I tried that long ago; seemingly its code is fine balance of bugs compensating each other). Btw, AppLocker only denies executing AFAIK, can it really be set up as per-app ACL system? – LogicDaemon – 2016-12-04T07:58:47.327
1@LogicDaemon Sorry, the mention of AppLocker was in reference to applications as security principals. I removed that part since it's confusing. Does the application still break if you disable listing on a higher-up folder? Another option might be to have the application run as a different user. The users with access to the script that launches it would have access to the account's password, but I think that's OK because you're just trying to stop accidental manual access. – Ben N – 2016-12-04T16:56:15.870
I'll probably do make it run under other user via script, it's good idea, thanks. Denying access to base folders breaks some parts of app too, I found it hard way – it started breaking in production after implementing this permissions and quick smoke-testing :( – LogicDaemon – 2016-12-05T08:00:31.633